Abstract
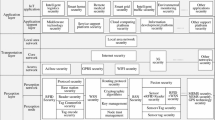
Aiming at increasingly serious security problems of wireless local area networks (WLANs), this paper analyzes and studies the different security attacks and threats according to the four layer network architecture of WLAN. A WLAN security assessment and enhancement system called SAEW is proposed, which comprises two subsystems of security assessment system of WLAN (SAW) and security enhancement system of WLAN (SEW). The SAW is based on fuzzy logic that combines layering analysis and relevance analysis. The security vulnerabilities of PHY and MAC layer, key management layer and identity authentication layer and relevance of the four layers are analyzed. The security index system of WLAN, fuzzy set and rule base are built based on the WLAN security analysis of the above four layers. Moreover, according to the principles of fuzzy logic, the security level of WLAN is acquired through fuzzy reasoning. Towards the WLAN with low security level, the security enhancement of WLAN is processed. The SEW builds the trusted WLAN to improve the security level of WLAN, which is based on trusted network connect (TNC). By introducing different roles in TNC, such as a metadata access point client defending WPA/WPA2 brute forcer, the security enhancement and defense mechanisms are realized. The results of case study show that the security level is promoted by trusted WLAN.



Similar content being viewed by others
Abbreviations
- WLAN:
-
Wireless local area network
- AP:
-
Access point
- STA:
-
Mobile wireless station
- AS:
-
Authentication server
- AHP:
-
Analytic hierarchy process
- SAEW:
-
Security assessment and enhancement system of WLAN
- SAW:
-
Security assessment system of WLAN
- SEW:
-
Security enhancement system of WLAN
- TNC:
-
Trusted network connect
- DMCG:
-
Distributed multi-core CPU and GPU parallel cracking method
- NJ:
-
None jammers
- SJ:
-
Single channel jammer
- OLJ:
-
All channel jammer using interference of overlapping channels
- ARJ:
-
All channel jammer with alterable jamming radius using interference of non-overlapping channels and adjustment of transmission power
- ARES:
-
Anti-jamming reinforcement system
- \(J\) :
-
Jamming degree of PHY and MAC layer
- \({\textit{KS}}\) :
-
Key strength of key management layer
- \({\textit{AM}}\) :
-
Authentication mechanism of identity authentication layer
- \(V\) :
-
Security level
- \({\textit{RP}}\) :
-
Regular passwords
- \({\textit{LIRP}}\) :
-
Low number irregular passwords
- \({\textit{HIRP}}\) :
-
High number irregular passwords
- \({\textit{EHIRP}}\) :
-
Extremely high number irregular passwords
- AR:
-
Access requestor
- PEP:
-
Policy enforcement point
- PDP:
-
Policy decision point
- MAP:
-
Metadata access point
- MAPC:
-
MAP client
References
IEEE Computer Society., & IEEE Standard for Information Technology. (2007). Telecommunications and information exchange between systems—Local and metropolitan area networks—Specific requirements—Part 11: Wireless LAN medium access control (MAC) and physical layer (PHY) specifications, IEEE STD 802.11TM-2007 (revision of IEEE Std 802.11-1999).
Wang, Y., Streff, K., & Raman, S. (2012). Smartphone security challenges. Computer, 45(12), 52–58.
Tews, E. (2007). Attacks on the WEP protocol. Doctoral dissertation, TU Darmstadt.
Yong-lei, L., Zhi-gang, J., & Ying, W. (2010). Survey on security scheme and attacking methods of WPA/WPA2. In IEEE 6th international conference on wireless communication networking and mobile computing (pp. 1–4). Chengdu: IEEE.
Fanbao, L., & Tao, X. (2012) How to break EAP-MD5. In Proceedings of the 6th IFIP WG 11.2 international workshop (pp. 49–57). Berlin: Springer.
Hoeper, K., & Chen, L. (2007). Where EAP security claims fail. In The fourth international conference on heterogeneous networking for quality, reliability, security and robustness and workshops. New York: ACM.
Liu, D. Q., & Coslow, M. (2008). Extensible authentication protocols for IEEE standards 802.11 and 802.16. In Proceedings of the international conference on mobile technology, applications, and systems. New York: ACM.
Choi, Y. B., Muller, J., Kopek, C. V., et al. (2006). Corporate wireless LAN security: Threats and an effective security assessment framework for wireless information assurance. International Journal of Mobile Communications, 4(3), 266–290.
Barbeau, M. (2010). Assessment of the true risks to the protection of confidential information in the wireless home and office environment. In IEEE international symposium on “a world of wireless, mobile and multimedia networks” (pp. 1–6). Montreal: IEEE Computer Society.
Dongmei, Z., Changguang, W., & Jianfeng, M. (2007). A risk assessment method of the wireless network security. Journal of Electronics (China), 24(3), 428–432.
Tsai, H.-Y., & Huang, Y.-L. (2011). An analytic hierarchy process-based risk assessment method for wireless networks. IEEE Transactions on Reliability, 60(4), 801–816.
The Trusted Network Connect (TNC) Work Group. (2012). TCG trusted network connect TNC architecture for interoperability spccification version 1.5 revision 3. Beaverton: TCG.
Todo, Y., & Ozawa, Y. (2012). Falsification attacks against WPA-TKIP in a realistic environment. IEICE Transactions on Information and Systems, E95–D(2), 588–595.
Rajyaguru V., Tamma B. R., & Manoj B. S., et al. (2012) On detecting CTS duration attacks using K-means clustering in WLANs. In IEEE international conference on advanced networks and telecommunciations systems (pp. 90–95). Bangalore: IEEE Computer Society.
Peco, S., Mitko, B., & Aleksandar, R. (2012). Wireless local area network behavior under RTS flood DoS attack, 20th telecommunications forum. Belgrade: IEEE Computer Society.
Liu, C., Yu, J. T., & Brewster, G. (2010) Empirical studies and queuing modeling of denial of service attacks against 802.11 WLANs. In IEEE international symposium on “a world of wireless, mobile and multimedia networks” (pp. 1–9). Montreal: IEEE Computer Society.
EWSA.[EB/OL]http://www.elcomsoft.com/ewsa.html. (2012).
Pyrit.[EB/OL]http://code.google.com/p/pyrit. (2012).
ZerOne.[EB/OL]. http://forum.anywlan.com/thread-12122-1-1.html. (2012).
Yong-lei, L., & Zhi-gang, J. (2013). Distributed method for cracking WPA/WPA2-PSK on multi-core CPU and GPU architecture. Intetrnational Journal of Communication Systems. doi:10.1002/dac.2699.
Huang, Q., Kobayashi, H., & Liu, B. (2003) Modeling of distributed denial of service attacks in wireless networks. In IEEE Pacific rim conference on communications, computers and signal processing (pp. 41–44). Piscataway: IEEE Press.
Xu, W., Trappe, W., & Zhang, Y. et al. (2005) the feasibility of launching and detecting jamming attacks in wireless networks. In Proceedings of the 6th ACM international symposium on mobile ad hoc networking and computing (pp. 46–57). New York: ACM.
Wang, W. J., Bhattacharjee, S., Chatterjee, M., et al. (2013). Collaborative jamming and collaborative defense in cognitive radio networks. Pervasive and Mobile Computing, 9(4), 572–587.
Sun, Y. Q., Wang, X. D., & Zhou, X. M. (2012). Jamming attacks in wireless nwtwork. Journal of Software, 23(5), 1207–1221.
Pelechrinis, K., Iliofotou, M., & Krishnamurthy, S. V. (2011). Denial of service attacks in wireless networks: the case of jammers. IEEE Communications Surveys & Tutorials, 13(2), 245–257.
Zhe, C., Zhigang, J., & Yonglei, L. (2012). Design and implementation of 802.11 jammer based on adjacent channel interference. Computer Engineer, 38(7), 250–252.
Yonglei, L., Zhigang, J., Ming, G., et al. (2013). ARJ: An IEEE 802.11g all-channel jammer with alterable jamming radius. Chinese Journal of Computers, 36(4), 870–881.
Pelechrinis, K., Koufogiannakis, C., & Krishnamurthy, S. V. (2010). On the efficacy of frequency hopping in coping with jamming attacks in 802.11 networks. IEEE Transactions on Wireless Communications, 9(10), 3258–3271.
Pelechrinis, K., Broustis, I., Krishnamurthy, S. V., et al. (2011). A measurement-driven anti-jamming system for 802.11 networks. IEEE/ACM Transactions on Networking, 19(4), 1208–1222.
Asokan, N., Niemi, V., & Nyberg, K. (2005) Man-in-the-middle in tunneled authentication protocols. In Proceedings of the 11th international conference on security protocols (pp. 28–41). Berlin: Springer.
Bakytbek, E., & Gokhan, D. (2012). Analysis of EAP–FAST protocol. In Proceedings of the 34th international conference on information technology interfaces (pp. 417–422). Cavtat/Dubrovnik: University of Zagreb.
Liu, X., & Fapojuwo, A. O. (2006). Formal Evaluation of major authentication methods for IEEE 802.11i WLAN standard. In IEEE 64th vehicular technology conference (pp. 1–5). Montreal: IEEE.
Idrissi Y. E. H. E., Zahid, N., & Jedra, M. (2012) Security analysis of 3GPP (LTE)—WLAN interworking and a new local authentication method based on EAP-AKA (pp. 137–142). London: IEEE Computer Society.
Malekzdeh, M., Ghani, A. A. A., Desa, J., et al. (2009). Vulnerability analysis of extensible authentication protocol (EAP) DoS attack over wireless networks. ICGST-CNIR Journal, 9(1), 39–46.
Nyberg, K. (2006). Connect now to MitM. http://www.tcs.hut.fi/Publications/knyberg/crypto06_rump.pdf.
Yonglei, L., & Zhigang, J. (2013). Security analysis of WPS in WLAN [J/OL]. Computer Engineering and Applications. http://www.cnki.net/kcms/detail/11.2127.TP.20120618.1131.004.html.
Tang, Z.-H., Xu, L., Chen, Z., et al. (2008). On the security of WAI protocol in the third version of WAPI. In Proceedings of the international conference on intelligent information hiding and multimedia signal processing (pp. 516–519). Piscataway: IEEE Press.
Yonglei, L., & Zhigang, J. (2012). Security enhancement of WAPI access authentication protocol (WAI). Journal of Harbin Institiute of Technology (New Series), 19(6), 42–46.
Milliken, J., & Marshall, A. (2010). The threat-victim table: A security prioritisation framework for diverse WLAN network topographies. In Proceedings of the international conference on security and cryptography (pp. 1–6). Athens: INSTICC.
Gill, R., Smith, J., Clark, A. (2006). Specification-based intrusion detection in WLANs. In Annual computer security applications conference (pp. 141–150). Miami Beach: IEEE Computer Society.
Ali, Q. I., & Lazim, S. (2012). Design and implementation of an embedded intrusion detection system for wireless applications. IET Information Security, 6(3), 171–182.
Hussain, F. A., & Aslam, K. F. (2012). A survey of intrusion detection systems for wireless sensor networks. International Journal of Ad Hoc and Ubiquitous Computing, 9(2), 69–83.
Yonglei, L., Guofeng, T., Zhisheng, L., et al. (2011). Survey of wireless 802.11 honeypot. Application of Electronic Technique, 37(4), 142–144.
Sun, P., Wu, Z-q, Feng, D-m, et al. (2009). Study and design of access authentication protocol based on TPM. Computer Engineering and Applications, 45(34), 78–81.
Li, J., Wu, Z-q, Yu, L., et al. (2010). Design of enhanced wireless trusted network accessing attestation model and its protocols. Computer Engineering and Applications, 46(7), 121–124.
Ma, Z., Ma, J-f, Yang, C., et al. (2010). Trusted network connect protocol for wireless environment. Journal of Beijing University of Technology, 36(5), 577–581.
Palmieri, F., Fiore, U., & Castiglione, A. (2011). Automatic security assessment for next generation wireless mobile networks. Mobile Information Systems, 7(3), 217–239.
Aspyct.org., & Aircrack-ng. (2012). http://www.aircrack-ng.org.
Sii, H. S., Ruxton, T., & Wang, J. (2001). A fuzzy-logic-based approach to qualitative safety modelling for marine systems. Reliability Engineering and System Safety, 73(1), 19–34.
Lunbiao, Y., Yingyi, G., & Weixin, L. (2011). Principles and applications of fuzzy mathematics (5th ed.). Guangzhou: South China University of Technology Press.
Lei, Z., Jiang, Y., Rong, Z., et al. (2012). Prevention research of cracking WPA–PSK key based on GPU. In Proceedings of the 2nd international conference on consumer electronics, communications and networks (pp. 1965–1969). Piscataway: IEEE Computer Society.
Yonglei, L. (2013). Defense of WPA/WPA2-PSK brute forcer. In 3rd IEEE international conference on computer science and automation engineering. Guangzhou: IEEE (accepted).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Liu, Yl., Jin, Zg. SAEW: A Security Assessment and Enhancement System of Wireless Local Area Networks (WLANs). Wireless Pers Commun 82, 1–19 (2015). https://doi.org/10.1007/s11277-014-2188-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-014-2188-y