Abstract
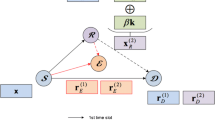
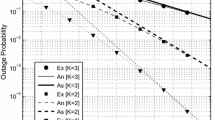
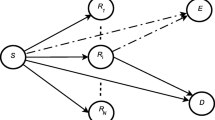
In this paper, we consider cooperative relaying protocols for enhancing wireless physical layer security. For time-division multiple-access based cooperative protocols, we analyze achievable secrecy rates with total and individual relay power constraints and design relay beamforming weights to improve the secrecy rate, assuming that multiple cooperative relays operate in decode-and-forward mode. Numerical results are presented to compare the secrecy rates of the cooperative protocols in various secure communication environments.




Similar content being viewed by others
References
Mukherjee, A., Fakoorian, S. A. A., Huang, J., & Swindlehurst, A. L. (2014). Principles of physical layer security in multiuser wireless networks: A survey. IEEE Communications Surveys and Tutorials, 16(3), 1550–1573.
Wyner, A. D. (1975). The wire-tap channel. Bell System Technical Journal, 54(8), 1355–1387.
Liang, Y., Poor, H. V., & Shamai, S. (2008). Secure communication over fading channels. IEEE Transactions on Information Theory, 54(6), 2470–2492.
Gopala, P. K., Lai, L., & Gamal, H. E. (2008). On the secrecy capacity of fading channels. IEEE Transactions on Information Theory, 54(10), 4687–4698.
Dong, L., Han, Z., Petropulu, A. P., & Poor, H. V. (2010). Improving wireless physical layer security via cooperating relays. IEEE Transactions on Signal Processing, 58(3), 1875–1888.
Zhang, J., & Gursoy, M. C. (2010). Collaborative relay beamforming for secrecy. In Proceedings of IEEE international conference on communications (ICC), Cape Town, South Africa (pp. 1–5).
Zheng, G., Choo, L., & Wong, K. (2011). Optimal cooperative jamming to enhance physical layer security using relays. IEEE Transactions on Signal Processing, 59(3), 1317–1322.
Li, J., Petropulu, A. P., & Weber, S. (2011). On cooperative relaying schemes for wireless physical layer security. IEEE Transactions on Signal Processing, 59(10), 4985–4997.
Bassily, R., & Ulukus, S. (2012). Secure communication in multiple relay networks through decode-and-forward strategies. Journal of Communications and Networks, 14(4), 352–363.
Nabar, R. U., Bölcskei, H., & Kneubühner, F. W. (2004). Fading relay channels: performance limits and space-time signal design. IEEE Journal on Selected Areas in Communications, 22(6), 1099–1109.
Boyd, S., & Vandenberghe, L. (2004). Convex optimization. Cambridge: Cambridge Univ. Press.
Havary-Nassab, V., Shahbazpanahi, S., Grami, A., & Luo, Z. (2008). Distributed beamforming for relay networks based on second-order statistics of the channel state information. IEEE Transactions on Signal Processing, 56(9), 4306–4316.
Sturm, J. F. (1999). Using SeDuMi 1.02, a Matlab toolbox for optimization over symmetric cones. Optimization Methods and Software, 11–12, 625–653.
Lofberg, J. (2004). YALMIP: A toolbox for modeling and optimization in MATLAB. In Proceedings of IEEE international symposium on computer aided control system design (CACSD), Taipei, Taiwan (pp. 284–289).
Sidiropoulos, N. D., Davidson, T. N., & Luo, Z. (2006). Transmit beamforming for physical-layer multicasting. IEEE Transactions on Signal Processing, 54(6), 2239–2251.
Luo, Z., Ma, W., So, A., Ye, Y., & Zhang, S. (2010). Semidefinite relaxation of quadratic optimization problems. IEEE Signal Processing Magazine, 27(3), 20–34.
Acknowledgments
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Science, ICT & Future Planning (NRF-2013R1A1A1A05004401).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Lee, JH. Cooperative Relaying Protocol for Improving Physical Layer Security in Wireless Decode-and-Forward Relaying Networks. Wireless Pers Commun 83, 3033–3044 (2015). https://doi.org/10.1007/s11277-015-2580-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2580-2