Abstract
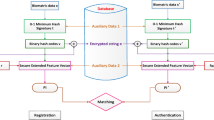
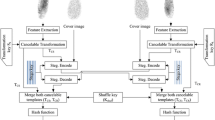
In order to solve the prealignment problem, this paper constructs new fingerprint features which will not change along with the rotation of fingerprint image. And then the SHA1 algorithm is improved in four aspects: the modification of original register values, the modification of additive constants, the modification of logic functions, the modification of compression functions, then this paper improves the SHA2 algorithm in two aspects: the modification of compression functions and the modification of message word. Based on that, two cancelable and irreversible fingerprint encryption schemes are proposed in this paper. The efficiency analysis and security authentication show that these schemes have enhanced the security without increasing the complexity.












Similar content being viewed by others
References
Juels, A., & Sudan, M (2002) A fuzzy vault scheme. In Proceedings of IEEE international symposium on information theory, pp. 408.
Uludag, U., & Jain, A. (2006) Securing fingerprint template: Fuzzy vault with helper data. In Proceedings of conference on computer vision and pattern recognition workshop (CVPRW), Washington, DC, pp. 163–169.
Tulyakov, S., Farooq, F., Mansukhani, P., & Govindaraju, V. (2007). Symmetric hash functions for secure fingerprint biometric systems. Pattern Recognition Letters, 28(16), 2427–2436.
Nandakumar, K., Jain, A., & Pankanti, S. (2007). Fingerprint-based fuzzy vault: Implementation and performance. IEEE Transactions on Information Forensics and Security, 2(4), 744–757.
Ronglin, Z., & Eryun, L. (2011). Improved cancelable fingerprint fuzzy vault system. Journal of Xidian University, 38(4), 173–180.
Tulyakov, K., & Govindaraju. (2010). Combination of symmetric hash functions for secure fingerprint matching. In 2010 international conference on pattern recognition, pp. 890–893.
Wang, X., Yin, Y., & Yu, H. (2005). Finding collisions in the full SHA-1. In Advances in cryptology—CRYPTO 2005 Lecture Notes in Computer Science (Vol. 3621, pp. 17–36).
Acknowledgments
This work was supported by the National Nature Science Foundation of China under Grant 61171072, the Key Program for Technology & Innovation of College in Guangdong Province (CXZD1143) and the Science & Technology Projects of Shenzhen (CXB201104210002A, ZDSY20120612094312435, JCYJ20130329115832637 and ZDSYS20140430164957660).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Yang, Y., Yu, J., Zhang, Q. et al. Improved Hash Functions for Cancelable Fingerprint Encryption Schemes. Wireless Pers Commun 84, 643–669 (2015). https://doi.org/10.1007/s11277-015-2654-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2654-1