Abstract
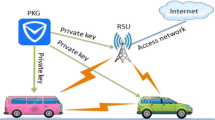
The authentication protocols are trusted components in a communication system in order to protect sensitive information against a malicious adversary in the road network environment by means of providing a variety of services including users’ privacy and authentication. Authenticated key agreement protocol is a useful cryptographic primitive, which can be used to protect the confidentiality, integrity and authenticity for transmitted data over insecure networks. From the point of view of the management of pre-shared secrets, one of the advantages of three-party authenticated key agreement protocols is that they are more suitable for use in a network with large numbers of users compared with two-party authenticated key agreement protocols. Using smart cards is a practical, secure measure to protect the secret private keys of a user. In this paper, we introduce an Authentication key establishment protocol for IPv6-based Road networks. In this architecture, a mobile vehicle obtains a unique address from a neighbor mobile vehicle or a road side unit without duplicate address detection, and the leaving mobile vehicle’s address space can be automatically reclaimed for reassignment. If the next mobile vehicle located is in transmission range, then the mobile vehicle forwards the packets; if not, then it carries the packets until meeting. The carry mostly occurs on sparsely populated road segments; with long carry distances having long end-to-end packet delays. On the other hand, we also describe a new authentication method based on a cryptographic protocol including a zero-knowledge proof that each node must use to convince another node on the possession of certain secret without revealing anything about it, which allows encrypted communication during authentication. The proposed protocol featured with the following characteristics: Firstly, it offers anonymous authentication: a message issuer can authenticate itself. Secondly, it provides confidential: the secrecy of the communication content can be protected. The address configuration scheme must lower the cost in order to enhance the scalability. Thirdly, it is efficient: it achieves low storage requirements, fast message verification and cost-effective identity tracking in case of a dispute. In this paper, we evaluate the performance of this protocol. The data results show that protocol effectively improves the address configuration performance and our scheme is secure against passive and active attacks. Our scheme provides high security along with low computational and communication costs. As a result, our scheme is practically suitable for mobile devices in the road network environment as compared to other related schemes in the literature.


















Similar content being viewed by others
References
Joy, C. M., Saurabh, A., & Arobinda, G. (2014). Distributed event notification in VANET with multiple service providers. In DEBS ‘14: Proceedings of the 8th ACM International Conference on Distributed Event-Based Systems, May 2014.
Zitong, C., Yubao, L., Raymond, C.-W. W., Jiamin, X., Ganglin, M., & Cheng, L. (2014). Efficient algorithms for optimal location queries in road networks. In SIGMOD ‘14: Proceedings of the 2014 ACM SIGMOD International Conference on Management of Data, June 2014.
Memon, I. (2015). Authentication users privacy: An integrating location privacy protection algorithm for secure moving objects in location based services. Wireless Personal Communications,. doi:10.1007/s11277-015-2300-y.
Akhtar, R., Leng, S., Memon, I., Ali, M., & Zhang, L. (2014). Architecture of hybrid mobile social networks for efficient content delivery. Wireless Personal Communications. doi:10.1007/s11277-014-1996-4.
Alsabaan, M., Alasmary, W., Albasir, A., & Naik, K. (2013). Road network for a greener environment: A survey. IEEE Communications Surveys & Tutorials, 15(3), 1372–1388.
Moore, N. (2006). Optimistic duplicate address detection (DAD) for IPv6. IETF RFC 4429.
Czyz, J., Allman, M., Zhang, J., Iekel-Johnson, S., Osterweil, E., & Bailey, M. (2014). Measuring IPv6 adoption. In SIGCOMM ‘14: Proceedings of the 2014 ACM Conference on SIGCOMM, August 2014.
Memon, I., Mohammed, M. R., Akhtar, R., Memon, H., Memon, M. H., & Shaikh, R. A. (2014). Design and implementation to authentication over a GSM system using certificate-less public key cryptography (CL-PKC). Wireless Personal Communications, 79, 661–686. doi:10.1007/s11277-014-1879-8.
Ghosh, U., & Datta, R. (2011). A secure dynamic IP configuration scheme for mobile ad hoc networks. Ad Hoc Networks, 9(7), 1327–1342.
Wang, X., & Mu, Y. (2013). A secure IPv6 address configuration scheme for a MANET. Security and Communication Networks, 6(6), 777–789.
Liu, A. X., & Khakpour, A. R. (2013). Quantifying and verifying reachability for access controlled networks. IEEE/ACM Transactions on Networking (TON), 21(2), 551–565. doi:10.1109/TNET.2012.2203144.
Won, M., & Stoleru, R. (2014). A low-stretch-guaranteed and lightweight geographic routing protocol for large-scale wireless sensor networks. Transactions on Sensor Networks (TOSN), 11(1), 1–18. doi:10.1145/2629659.
Škoberne, N., Maennel, O., Phillips, I., Bush, R., Zorz, J., & Ciglaric, M. (2014). IPv4 address sharing mechanism classification and tradeoff analysis. IEEE/ACM Transactions on Networking (TON), 22(2), 391–404.
Zhou, H., Mutka, M. W., & Ni, L. M. (2010). Secure prophet address allocation for MANETs. Security and Communication Networks, 3(1), 31–43.
Sun, H.-M., Chen, C.-H., Yeh, C.-W., & Chen, Y.-H. (2013). A collaborative routing protocol against routing disruptions in MANETs. Personal and Ubiquitous Computing, 17(5), 865–874.
Shin, H., Talipov, E., & Cha, H. (2012). Spectrum: Lightweight hybrid address autoconfiguration protocol based on virtual coordinates for 6LoWPAN. IEEE Transactions on Mobile Computing, 11(11), 1749–1761.
Memon, I., Chen, L., Majid, A., Lv, M., Hussain, I., & Chen, G. (2015). Travel recommendation using geo-tagged photos in social media for tourist. Wireless Personal Communications, 80(4), 1347–1362. doi:10.1007/s11277-014-2082-7.
Talipov, E., Shin, H., Han, S., et al. (2011). Alightweight stateful address autoconfiguration for6LoWPAN. Wireless Network, 17(1), 183–197.
Al-Mistarihi, M. F., Al-Shurman, M., & Qudaimat, A. (2011). Tree based dynamic address autoconfiguration in mobile ad hoc networks. Computer Networks, 55(8), 1894–1908.
Mohandas, B. K., & Liscano, R. (2008). IP address configuration in VANET using centralized DHCP. In 33rd IEEE local computer networks conference (pp. 608–613)
Coussement, R., Bensaber, B. A.,, & Biskri, I. (2013). Decision support protocol for intrusion detection in VANETs. In DIVANet ‘13: Proceedings of the third ACM international symposium on design and analysis of intelligent road network and applications.
Rafiee, H., & Meinel, C. (2013). Privacy and security in IPv6 networks: challenges and possible solutions. In SIN ‘13: Proceedings of the 6th international conference on security of information and networks, November 2013.
Chen, Y.-S., Cheng, C.-H., Hsu, C.-S., & Chiu, G.-M. (2009). Network mobility protocol for vehicular ad hoc networks. In Wireless communications and networking conference, WCNC (pp. 1–6).
BenMimoune, A., Khasawneh, F. A., Kadoch, M., Sun, S., & Rong, B. (2014). Inter-cell handoff performance improvement in LTE-a multi-hop relay networks. In MobiWac ‘14: Proceedings of the 12th ACM international symposium on mobility management and wireless access.
Han, J., Lin, Y.-H., Perrig, A., & Bai, F. (2014). Short paper: MVSec: Secure and easy-to-use pairing of mobile devices with vehicles. In WiSec ‘14: Proceedings of the 2014 ACM conference on Security and privacy in wireless & mobile networks.
Memon, I., Mangi, F. A., & Jamro, D. A. (2013). Collision avoidance of intelligent service robot for industrial security system. IJCSI International Journal of Computer Science Issues, 10(2), 3.
Kamenyi, D. M., Wang, Y., Zhang, F., Memon, I., & Gustav, Y. H. (2013). Authenticated privacy preserving for continuous query in location based services. Journal of Computational Information Systems, 9(24), 9857–9864.
Memon, I., Mangi, F. A., Jamro, D. A., Basit, M. A., & Memon, M. H. (2013). Rumor riding: Peer to peer systems. International Journal of Scientific & Engineering Research, 4(6), 1020–1028.
Hwang, T., & Gope, P. (2014). Provably secure mutual authentication and key exchange scheme for expeditious mobile communication through synchronously one-time secrets. Wireless Personal Communications, 77, 197–224. doi:10.1007/s11277-013-1501-5.
Xiaonan, W., & Shan, Z. (2013). An IPv6 address configuration scheme for wireless sensor networks based on location information. Telecommunication Systems, 52(1), 151–160.
Chang, B.-J., Liang, Y.-H., & Yang, H.-J. (2014). Performance analysis with traffic accident for cooperative active safety driving in VANET/ITS. Wireless Personal Communications, 74, 731–755. doi:10.1007/s11277-013-1318-2.
Ying, B., Makrakis, D., & Mouftah, H. T. (2013). Privacy preserving broad cast message authentication protocol for VANETs. Journal of Network and Computer Applications, 36, 1352–1364.
Kumar, R., & Dave, M. (2013). A framework for handling local broadcast storm using probabilistic data aggregation in VANET. Wireless Personal Communications, 72, 315–341. doi:10.1007/s11277-013-1016-0.
Chena, Y.-S., Hsu, C.-S., & Yi, W.-H. (2012). An IP passing protocol for vehicular ad hoc networks with network fragmentation. Computers and Mathematics with Applications, 63(2), 407–426.
Wang, X., Mu, Y., Han, G., & Le, D. (2014). A secure IPv6 address configuration protocol for road network. Wireless Personal Communications. doi:10.1007/s11277-014-1882-0
Wu, X., Brown, K. N., Sreenan, C. J., Alvarez, P., Ruffini, M., Marchetti, N., et al. (2013). An XG-PON module for the NS-3 network simulator. In SimuTools ‘13: Proceedings of the 6th international ICST conference on simulation tools and techniques, March 2013.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Memon, I. A Secure and Efficient Communication Scheme with Authenticated Key Establishment Protocol for Road Networks. Wireless Pers Commun 85, 1167–1191 (2015). https://doi.org/10.1007/s11277-015-2833-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2833-0