Abstract
In a client–server environment, it is an important issue to ensure that only legal users have access to use the various remote services. Nowadays, many chaotic maps-based authenticated key agreement schemes using static ID have been widely used. However, static ID authentication schemes cannot provide user anonymity. It is a better choice to utilize dynamic ID authentication scheme. Recently, Lin proposed a chaotic maps-based mobile dynamic ID authenticated key agreement scheme and proved that it is secure against existential active attacks. Unfortunately, in this paper, we show that Lin’s scheme cannot resist dictionary attack, user spoofing attack and denial of service (DoS) attack. In addition, in the password-change phase of Lin’s scheme, if anyone else inputs the two uncorrelated passwords, the mobile device will continue to update the password which lead to legal user cannot log in forever. Finally we proposed an improved protocol based on chaotic maps. Compared with previous related works, the improved protocol not only can withstand existential active attacks, but also has better computational efficiency.


Similar content being viewed by others
References
Xie, Q., Zhao, J. M., & Yu, X. Y. (2013). Chaotic maps-based three-party password-authenticated key agreement scheme. Nonlinear Dynamics, 74(4), 1021–1027.
Guo, C., & Chang, C. C. (2013). Chaotic maps-based password-authenticated key agreement using smart cards. Communications in Nonlinear Science and Numerical Simulation, 18(6), 1433–1440.
Chain, K., & Kuo, W. C. (2013). A new digital signature scheme based on chaotic maps. Nonlinear Dynamics, 74(4), 1003–1012.
Lin, H.-Y. (2014). Chaotic map based mobile dynamic ID authenticated key agreement scheme. Wireless Personal Communications, 78(2), 1487–1494.
Das, M. L., Saxana, A., & Gulati, V. P. (2004). A dynamic ID-based remote user authentication scheme. IEEE Transactions on Consumer Electronics, 50(2), 629–631.
Wang, Y. Y., Liu, J. Y., Xiao, F. X., & Dan, J. (2009). A more efficient and secure dynamic ID-based remote user authentication scheme. Computer Communications, 32(4), 583–585.
Khan, M. K., Kim, S. K., & Alghathbar, K. (2011). Cryptanalysis and security enhancement of a more efficient and secure dynamic ID-based remote user authentication scheme. Computer Communications, 34(3), 305–309.
Tang, H. B., & Liu, X. S. (2012). Cryptanalysis of a dynamic ID-based remote user authentication with key agreement scheme. Informational Journal of Communication Systems, 25(12), 1639–1644.
He, Debiao, & Shuhua, Wu. (2013). Security flaws in a smart card based authentication scheme for multi-server environment. Wireless Personal Communications, 70(1), 323–329.
He, Debiao, & Wang, Ding. (2014). Robust biometrics-based authentication scheme for multi-server environment. IEEE Systems Journal,. doi:10.1109/JSYST.2014.2301517.
He, D., Zhang, Y., & Chen, J. (2014). Cryptanalysis and improvement of an anonymous authentication protocol for wireless access networks. Wireless Personal Communications, 74(2), 229–243.
Xiao, D., Liao, X., & Deng, S. (2007). A novel key agreement protocol based on chaotic maps. Information Sciences, 177, 1136–1142.
Wang, X., & Zhao, J. (2010). An improved key agreement protocol based on chaos. Communications in Nonlinear Science and Numerical Simulation, 15, 4052–4057.
Kocarev, L., & Lian, S. (2011). Chaos-based cryptography: Theory, algorithms and applications (pp. 53–54). Berlin: Springer.
Xue, K., & Hong, P. (2012). Security improvement on an anonymous key agreement protocol based on chaotic maps. Communications in Nonlinear Science and Numerical Simulation, 17(7), 2969–2977.
Niu, Y., & Wang, X. (2011). An anonymous key agreement protocol based on chaotic maps. Communications in Nonlinear Science and Numerical Simulation, 16(4), 1986–1992.
Kar, J., & Majhi, B. (2009). An efficient password security of three party key exchange protocol based on ECDLP. In 12th international conference on information technology 2009 (ICIT 2009), Bhubaneswar, India, Tata McGrow Hill Education Private Limited (pp. 75–78).
Katz, J., & Shin, J. S. (2005). Modeling insider attacks on group key-exchange protocols. In Proceedings of the 12th ACM conference on computer and communications security–CCS’05, ACM (pp. 180–189).
Canetti, R., & Krawczyk, H. (2001). Analysis of key-exchange protocols and their use for building secure channels. In EUROCRYPT, Vol. 2045 of Lecture notes in computer science (pp. 453–474).
Niu, Y., & Wang, X. (2011). An anonymous key agreement protocol based on chaotic maps. Communications in Nonlinear Science and Numerical Simulation, 16(4), 1986–1992.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1: Security Proof of the Proposed Scheme
1.1 Mutual Authentication and Key Agreement
Definition 1
Mutual authentication and key agreement refers to two parties authenticating each other suitably and getting the session key simultaneously.
Theorem 1
The proposed protocol can achieve mutual authentication and key agreement.
Proof
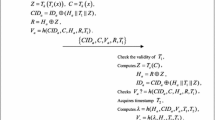
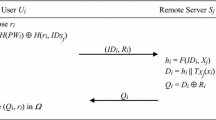
Server B uses the secret key s to compute K SA = T s T k (x), so the improved scheme allows B authenticated Alice by checking whether \( H_{A}^{\prime } \) = H A . Because only Alice’s MD can compute the H a = h(s||ID a ) by inputting the right ID a and PW a .
Alice authenticates server B uses by checking whether \( V_{1} {\text{ equals }}h(V_{2} \oplus H_{a} ) \). Because only B can compute H a = h(s||ID a ) based on its secret key s.
As for the key agreement, after authenticating each other, the temporary T k (x), r, R and the ID ID a , ID b were already authenticated by B. So finally Alice and B can make the key agreement simultaneously.
1.2 Impersonation Attack/Man-in-the-Middle Attack
Definition 2
An impersonation attack is an attack in which an adversary successfully assumes the identity of one of the legitimate parties in a system or in a communications protocol.
Definition 3
The man-in-the-middle attack is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker.
Theorem 2
The proposed protocol can resist impersonation attack.
Theorem 3
The proposed protocol can resist Man-in-the-middle attack.
Proof
An adversary cannot impersonate anyone of the Alice or B. The improved scheme has already authenticated each other between Alice and B (in “Mutual authentication and key agreement” section of Appendix 1) based on the secrets s, PW a and the nonces k, R, r. So there is no way for an adversary to have a chance to carry out impersonation attack.
Because C, V 1, V 2 contain the participants’ identities, a man-in-the-middle attack cannot succeed.
1.3 Replay Attack
Definition 4
A replay attack is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed.
Theorem 4
The proposed protocol can resist replay attack.
Proof
An adversary cannot start a replay attack against our scheme because of the freshness of k, R, r in each session. If T k (x), V 1 and V 2 has appeared before or the status shows in process, any of the participants in instance protocol will reject the session request. If the adversary wants to launch the replay attack successfully, it must compute and modify T k (x), V 1, V 2 and C correctly which is impossible.
1.4 Known-Key Security
Definition 5
Known-key security is that a protocol can protect the subsequent session keys from disclosing even if the previous session keys are revealed by the intendant user.
Theorem 5
The proposed protocol can achieve known-key security.
Proof
Since the session key SK = h(ID a ||ID b ||R||h(R||r))) is depended on the random nonces k, R and r, and the generation of nonces is independent in all sessions, an adversary cannot compute the previous and the future session keys when the adversary knows one session key. And in the password-change phase, any session key is only used once, so it has known-key security attribute.
1.5 Perfect Forward Secrecy
Definition 6
An authenticated multiple key establishment protocol provides perfect forward secrecy if the compromise of both of the node’s secret keys cannot results in the compromise of previously established session keys [17].
Theorem 6
The proposed protocol can achieve perfect forward secrecy.
Proof
In the improved scheme, the session key SK = h(ID a ||ID b ||R||h(R||r))) is related with R and r, which were randomly chosen by Alice and the server B, respectively. So any session key has not related with the secret key (such as s, PW a ) of each of participants. Furthermore because of the intractability of the CMBDLP and CMBDHP problem, an adversary cannot compute the previously established session keys.
1.6 Data Integrity
Definition 7
Authentication multiple key establishment protocol is said to achieve the property of data integrity, if there is no polynomial time algorithm that can alter or manipulate the transmitted messages.
Theorem 7
The proposed protocol can achieve data integrity property.
Proof
While the each participant sends the sensitive data to another participant in the instance protocol by the communication channel, the adversary alter or manipulate the data and cheat one of the honest participants by relying on the wrong session keys.
If the adversary wants to alter or manipulate the message C, T k (x) of Step 4 for cheating server B, the adversary will be detected in the Step 5. Because the adversary does not have the PW a of Alice, then the adversary cannot compute \( C = E_{{K_{AS} }} (H_{A} ||ID_{a} ||ID_{b} ) \), finally the adversary cannot pass the validation of B. As for V 1, V 2, the adversary cannot alter or manipulate it because V 1, V 2 is just two values of a secure hash and Alice can verify V 1, V 2 by the local information H a .
1.7 Guessing Attacks
Definition 8
In an off-line guessing attack, an attacker guesses a password or long-term secret key and verifies his/her guess, but he/she does not need to participate in any communication during the guessing phase. In an undetectable on-line guessing attack, an attacker searches to verify a guessed password or long-term secret key in an on-line transaction and a failed guess cannot be detected and logged by the server.
Theorem 8
The proposed protocol can resist Guessing attacks.
Proof
In our proposed scheme of the authenticated key exchange phase, the undetectable on-line guessing attack will fail since after Step 5, B can authenticate Alice. The off-line guessing attack will not work against the proposed scheme since the password pw A is not transmitted on the public channel at all. Even if the adversary gets the Alice’s MD and wants to execute off-line guessing attack, he will fail because the information \( N_{a} = h\left( {ID_{a} ||PW_{a} } \right) \oplus h(s||ID_{a} ) \) is protected by server’s secret key s. Therefore, the proposed scheme can resist guessing attacks.
1.8 Session Key Security
Definition 9
A communication protocol exhibits session key security if the session key cannot be obtained without any long-term secrets.
Theorem 9
The proposed protocol can achieve session key security.
Proof
In the authenticated key agreement phase and password and shared secret key among servers update phase, a session key SK = h(ID a ||ID b ||R||h(R||r))) is generated from R and r. These parameter values are different in each session, and each of them is only known by Alice and B. Whenever the communication ends between B and Alice, the key will immediately self-destruct and will not be reused. Therefore, assuming the attacker has obtained a session key, Alice will be unable to use this session key to decode the information in other communication processes. Because the random point elements R and r are all generated randomly and are protected by the CMBDLP, CMBDHP, a secure one-way hash function and the secure symmetric encryption, a known session key cannot be used to calculate the value of the next session key. Additionally, since the values R and r of the random elements are very large, attackers cannot directly guess the values R and r of the random elements to generate session key. Therefore, the proposed scheme provides session key security.
1.9 Key Compromise Impersonation Attacks (KCI Attacks)
Definition 10
An adversary is said to impersonate a party B to another party A if B is honest and the protocol instance at A accepts the session with B as one of the session peers but there exists no such partnered instance at B [18]. In a successful KCI attack, an adversary with the knowledge of the long-term private key of a party A can impersonate B to A.
Theorem 10
The proposed protocol can resist KCI attack.
Proof
We assume that an adversary can know Alice’s secret password PW a . Then, an adversary can impersonate server B to cheat Alice, and to get the session key. But above-mentioned process will not be achieved and the attack course terminates at the beginning. Because an adversary cannot own the server’s secret key s, and then an adversary cannot decrypt \( C = E_{{K_{AS} }} (H_{A} ||ID_{a} ||ID_{b} ||R) \). Finally the adversary cannot pass validation of Alice because the adversary cannot compute V 1, V 2. So the key compromise impersonation attacks will fail.
1.10 Stolen Mobile Device Attack
Definition 11
Anyone gets the mobile device in some way to execute some kind of attacks.
Theorem 11
The proposed scheme can resist stolen mobile device attack.
Proof
It is very clear that the proposed scheme provides identify authentication on-line. Because there is no authenticated information stored in MD, the offline guessing attack when MD is lost cannot execute. Therefore, the proposed scheme can resist stolen mobile device attack.
1.11 Stolen-Verifier Attack
Definition 12
An authentication protocol is vulnerable to the stolen-verifier attack if a malicious adversary can modify user’s password stored in the remote server’s password table.
Theorem 12
The proposed scheme can resist Stolen-verifier attack.
Proof
It is very clear that there is no verifier-table including password in the remote server. So either the remote server or an adversary has no way to derive each user’s real password.
1.12 ID-Theft Attack
Definition 13
Identity theft is the fraudulent use of a person’s personal identifying information. An identity thief will use another person’s personal information such as social security number, date of birth, mother’s maiden name, or account numbers to open fraudulent new accounts. They will open new credit card or checking accounts, write drafts on existing checking accounts, charge on existing credit card accounts, or obtain new loans.
Theorem 13
The proposed scheme can resist ID-theft attack.
Proof
All the transmitting information C, T k (x) and V 1, V 2 on public channel is encrypted by a one-way secure hash function or a pair of secure symmetric encryption/decryption functions. Furthermore, in the improved scheme, we integrate random numbers with user’s identity to form a dynamic ID which varies with each login request. So the ID-theft attack will fail.
Appendix 2: The Provable Security of the Proposed Scheme
We recall the definition of session-key security in the authenticated-links adversarial model of Canetti and Krawczyk [19]. The basic descriptions are shown in Table 4.
We allow the adversary access to the queries SessionStateReveal, SessionKeyReveal, and Corrupt.
-
1.
SessionStateReveal( s ) This query allows the adversary to obtain the contents of the session state, including any secret information. s means no further output.
-
2.
SessionKeyReveal( s ) This query enables the adversary to obtain the session key for the specified session s, so long as s holds a session key.
-
3.
Corrupt(P i ) This query allows the adversary to take over the party P i , including long-lived keys and any session-specific information in P i ’s memory. A corrupted party produces no further output.
-
4.
Test( s ) This query allows the adversary to be issued at any stage to a completed, fresh, unexpired session s. A bit b is then picked randomly. If b = 0, the test oracle reveals the session key, and if b = 1, it generates a random value in the key space. The adversary Λ can then continue to issue queries as desired, with the exception that it cannot expose the test session. At any point, the adversary can try to guess b. Let GoodGuess Λ(k) be the event that the adversary Λ correctly guesses b, and we define the advantage of adversary Λ as \( Advantage^{\varLambda } (k) = \hbox{max} \left\{ {0,\left| {\Pr [GoodGuess^{\varLambda } (k)] - \frac{1}{2}} \right|} \right\} \), where k is a security parameter.
A session s is locally exposed with P i : if the adversary had issued SessionStateReveal( s ), SessionKeyReveal( s ), Corrupt(P i ) before s would have expired.
Definition 14
An authenticator exchange protocol Π 1 in security parameter k is said to be authentication secure in the adversarial model of Canetti and Krawczyk if for any polynomial-time adversary Λ,

-
1.
If two uncorrupted parties have completed matching sessions, these sessions produce the same key as output;
-
2.
Advantage Λ(k) is negligible.
Theorem 14
Under the CMBDHP assumption, using the Algorithm 1 to compute an authenticator is authentication secure in the adversarial model of Canetti and Krawczyk [19].
Proof
The proof is based on the proof given by Refs. [19, 20]. There are two uncorrupted parties in matching sessions output the same session key, and thus the first part of Definition 14 is satisfied. To show that the second part of the definition is satisfied, assume that there is a polynomial-time adversary Λ with a non-negligible advantage ɛ in standard model. We claim that Algorithm 1 forms a polynomial-time distinguisher for CMBDHP having non-negligible advantage.
Probability analysis It is clear that Algorithm 1 runs in polynomial time and has non-negligible advantage. There are two cases where the r-th session is chosen by Λ as the test session: (1) If the r-th session is not the test session, then Algorithm 1 outputs a random bit, and thus its advantage in solving the CMBDHP is 0. (2) If the r-th session is the test session, then Λ will succeed with advantage ɛ, since the simulated protocol provided to Λ is indistinguishable from the real protocol. The latter case occurs with probability 1/k, so the overall advantage of the CMBDHP distinguisher is ɛ/k, which is non-negligible.
Rights and permissions
About this article
Cite this article
Zhu, H. Cryptanalysis and Improvement of a Mobile Dynamic ID Authenticated Key Agreement Scheme Based on Chaotic Maps. Wireless Pers Commun 85, 2141–2156 (2015). https://doi.org/10.1007/s11277-015-2896-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2896-y