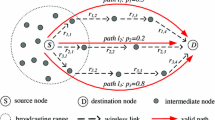
Abstract
In order to transfer the increasing big data we need to make use of multiple wireless paths. Overlay networks provide the possibility of taking advantage of multiple available routing paths to realize the bandwidth aggregating. We present a game-theoretic study of the selfish strategic collaboration of multiple heterogeneous overlays when they are allowed to use massively-multipath transfer. Overlays are modeled as players in this multipath selection game model, we discuss the asymmetric case where all overlays have the different round trip times (RTT) and different wastefulness level, and demonstrate the existence and uniqueness of Nash equilibrium (NE). Then we find overlays differing only in their RTTs still receive equal throughput shares and utilities at the NE. However, if overlays differ only in their wastefulness levels, a more wasteful overlay has a larger utility and a larger throughput (bandwidth) share than a less wasteful overlay.









Similar content being viewed by others
References
Iyengar, J., Amer, P., & Stewart, R. (2006). Concurrent multipath transfer using SCTP multihoming over independent end-to-end paths. IEEE/ACM Transactions Networking,. doi:10.1109/TNET.2006.882843.
Ford, A., Raiciu, C., Handley, M., Barre, S., & Iyengar, J. (2011). Architectural guidelines for multipath TCP development. March 2011, IETF, RFC 6182. Retrieved Dec 2014, from http://tools.ietf.org/html/rfc6182.txt
Abdulhadi, S., Jaseemuddin, M., & Anpalagan, A. (2012). A survey of distributed relay selection schemes in cooperative wireless ad hoc networks. Wireless Personal Communications, 63(4), 917–935. doi:10.1007/s11277-010-0174-6.
Wang, B., Wei, W., Guo, Z., & Towsley, D. (2009). Multipath live streaming via TCP: Scheme, performance and benefits. ACM Transactions on Multimedia Computing Communications and Applications (TOMCCAP), 5(3), 1–23. doi:10.1145/1556134.1556142.
Basar, T., & Olsder, G. J. (1998). Dynamic noncooperative game theory. New York: Academic Press. doi: 10.1137/1.9781611971132
Akella, A., Seshan, S., RichardKarp, C. M. U., & Shenker, S. (2002). Selfish behavior and stability of the internet: A game-theoretic analysis of TCP. Proceedings of ACM SIGCOMM,. doi:10.1145/633025.633037.
Abdulhadi, S., Jaseemuddin, M., & Anpalagan, A. (2014). On the throughput capacity of cooperative multi-hop wireless ad hoc networks with multi-flow. Wireless Personal Communications, 79(1), 629–646. doi:10.1007/s11277-014-1877-x.
Trestian, R., Ormond, O., & Muntean, G.-M. (2012). Game theory-based network selection: Solutions and challenges. IEEE Communications Surveys & Tutorials, 14(4), 1212–1231. doi:10.1109/SURV.2012.010912.00081.
Zhang, Y., & Guizani, M. (2011). Game theory for wireless communications and networking (1st ed.). CRC Press. ISBN:10:1439808899
Cetinkaya, C., & Knightly, E. (2004). Opportunistic traffic scheduling over multiple network paths. Proceedings of IEEE INFOCOM, Hong Kong. doi:10.1109/INFCOM.2004.1354602.
Wang, B., Wei, W., Kurose, J., & Towsley, D. (2007). Application-layer multipath data transfer via tcp: Schemes and performance tradeoffs. Performance Evaluation, 64, 965–977. doi:10.1016/j.peva.2007.06.013.
Amer, P., Becke, M., Dreibholz, T., Ekiz, N., Iyengar, J., Natarajan, et al., Load sharing for the stream control transmission protocol (SCTP). Draft-tuexen-tsvwg-sctp-multipath-07 (work in progress), Oct 2013. Retrieved Sep. 2014, from http://tools.ietf.org/html/draft-tuexen-tsvwg-sctp-multipath-07.txt
Becke, M., Dreibholz, T., Adhari, H., & Rathgeb, E. P. (2012). On the fairness of transport protocols in a multi-path environment. Proceedings of IEEE ICC, Ottawa/Canada. doi:10.1109/ICC.2012.6363695.
Gummadi, K. P., Madhyastha, H. V., Gribble, S. D., Levy, H. M., & Wetherall, D. (2004). Improving the reliability of internet paths with one-hop source routing. In Proceedings of USENIX OSDI, San Francisco, CA, pp. 183–198.
Fei, T., Tao, S., Gao, L., & Guerin, R. (2006). How to select a good alternate path in large peer-to-peer systems. Proceedings of IEEE INFOCOM. doi:10.1109/INFOCOM.2006.179.
Zhang, M., Lai, J., Krishnamurthy, A., Peterson, L., & Wang, R. (2004). A transport layer approach for improving end-to-end performance and robustness using redundant paths. In Proceedings of USENIX annual technical conference, Boston, MA, June 2004. doi:10.1.1.111.3109
Liao, J., Wang, J., & Zhu, X. (2008). A multi-path mechanism for reliable VOIP transmission over wireless networks. Computer Networks, 52(13), 2450–2460. doi:10.1016/j.comnet.2008.04.008.
Liao, J., Wang, J., Li, T., & Zhu, X. (2011). Introducing multipath selection for concurrent multipath transfer in the future internet. Computer Networks. doi:10.1016/j.comnet.2010.12.010.
Liao, J., Wang, J., Wu, B., & Wu, W. (2012). Toward a multi-plane framework of NGSON: A required guideline to achieve pervasive services and efficient resource utilization. IEEE Communications Magazine, 50(1), 90–97. doi:10.1109/MCOM.2012.6122537.
Wang, J., Liao, J., Li, T., & Wang, J. (2013). On the collaborations of multiple selfish overlays using multi-path resources. Peer-to-Peer Networking and Applications. doi:10.1007/s12083-013-0245-z.
Padhye, J., Firoiu, V., Towsley, D., & Kurose, J. (1998). Modelling TCP throughput: A simple model and its empirical validation. In Proceedings of ACM SIGCOMM, pp. 303–314. doi:10.1145/285243.285291
Floyd, S., Handley, M., Padhye, J., & Widmer, J. (2008). TCP friendly rate control (TFRC): Protocol specification, September 2008. IETF, RFC 5348. Retrieved April 2014, from http://tools.ietf.org/html/rfc5348.txt
Koutsoupias, E., & Papadimitriou, C. H. (2009). Worst-case equilibria. Computer Science Review, 3(2), 65–69. doi:10.1016/j.cosrev.2009.04.003.
Acknowledgments
This work was jointly supported by: (1) the National Basic Research Program of China (No. 2013CB329102); (2) National Natural Science Foundation of China (No. 61471063, 61421061, 61372120,61271019, 61101119, 61121001); (3) the Key (Keygrant) Project of Chinese Ministry of Education.(No. MCM20130310); (4) Beijing Municipal Natural Science Foundation (No. 4152039); (5) Beijing Higher Education Young Elite Teacher Project (No. YETP0473); (6) MICINN (No.TIN2010-19077); (7) CAM (No.S2009TIC-1692).
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1
The appendix provides the proof of Theorem 1. First, we transform the objective function into a simpler form: Φ = C/(1 − p). It is easy to see that we need to find the minimal feasible p to minimize Φ.
Note that p is a function of n (see (9)). If we take T 0,i = 4R i , as recommended in [22], and let \( \overline{\phi } (p) = \mu \sqrt p + 4\nu \left( {p^{3/2} + 32p^{7/2} } \right) \). (9) can be rewritten as
Solving for p given a specific n is actually equivalent to solving the above equation. First note that, \( \mathop {\lim }\limits_{p \to 0} F = \sum\nolimits_{j = 1}^{m} {n_{j} /R_{j} } ;\mathop {\lim }\limits_{p \to 1} F = - C \cdot \overline{\phi } (1) < 0 \). Furthermore, F(p,n) is a strictly monotonic decreasing function of p since \( {{\partial {\text{F}}} \mathord{\left/ {\vphantom {{\partial {\text{F}}} {\partial {\text{p}}}}} \right. \kern-0pt} {\partial {\text{p}}}} = - \sum\nolimits_{j = 1}^{m} {n_{j} /R_{j} - C\overline{\phi } < 0} \).
Thus, there must be a unique solution p in F (p, n) = 0 for any given feasible n. That is, p as a function of n is implicitly defined in F(p, n) = 0. Note that p is an increasing function of n, thus, minimal p opt (satisfying F (p, n) = 0) is uniquely achieved at n opt = (1, 1, …, 1). Then, we see that the system cost expressed in (7) uniquely achieves minimum value at n opt with
Appendix 2
The appendix provides the proof of Theorem 2. Each player i tries to solve for its optimal strategy \({\hbox{n}}_{i}^{*}\), as a response to the strategies of all other players. Thus, if there is an interior point NE n ne = \(\left( {n_{1}^{*} , \ldots, n_{m}^{*} } \right)\), then it must be true that ∀i, ∂U i /∂ \({\hbox{n}}_{i}^{*}\) = 0, and \( n_{i}^{*} = R_{i} \arg \max_{{n_{i} \in S_{i} }} U_{i} \left( {n_{1}^{*} ,n_{2}^{*} , \ldots ,n_{i}^{*} , \ldots ,n_{m}^{*} } \right) \). If we denote \( z_{i} = n_{i} /R_{i} \), utility function (6) is rewrited as:
In the following, we first introduce a fact indicating that the stationary point satisfying ∂U i /∂z i = 0 is actually the maximum point if it is in [1, ∞). Then we show that there is a unique n ne satisfying ∂U i /∂ \(z_{i}^{*}\) = 0, ∀i.
First, we need to seek all vectors n ne satisfying a set of m equations
We first prove that if n ne exists, \( n_{i}^{*} /n_{j}^{*} = R_{i} /R_{j} \), ∀ i,j . Then, we show that n ne is actually unique by proving that there is only one \(p^{*}\) such that \( n_{i}^{*} /n_{j}^{*} = R_{i} /R_{j} \), ∀i, j.
To simplify calculation formula, first we need to set \( \bar{\phi } = \mu \sqrt p + 4\nu (p^{3/2} + 32p^{7/2} ) \), thus \( {\text{B}}_{\text{i}} = 1/R_{i} \bar{\phi } \), \( \phi_{i} = R_{i} \bar{\phi } \) and \( \varphi_{i} = R_{i} \overline{\varphi } \). As \( {\text{B}}_{\text{i}} = C/R_{i} ( 1- {\text{p}})\sum\nolimits_{i = 1}^{m} {{{n_{i} } \mathord{\left/ {\vphantom {{n_{i} } {R_{i} }}} \right. \kern-0pt} {R_{i} }}} \), we have \( C\bar{\phi } = \left( {1 - {\text{p}}} \right)\sum\nolimits_{i = 1}^{m} {{{n_{i} } \mathord{\left/ {\vphantom {{n_{i} } {R_{i} }}} \right. \kern-0pt} {R_{i} }}} \), and utility function (Eq. 22) is further rewrited as:
For an arbitrary player i, we have:
where \( {{\bar{\phi } = \phi_{i} /R_{i} = \mu \sqrt p + 4\nu \left( {p^{3/2} + 32p^{7/2} } \right) = 1} \mathord{\left/ {\vphantom {{\bar{\phi } = \phi_{i} /R_{i} = \mu \sqrt p + 4\nu \left( {p^{3/2} + 32p^{7/2} } \right) = 1} {R_{i} B_{i} }}} \right. \kern-0pt} {R_{i} B_{i} }} \)
And \( z_{ - i} = \sum\nolimits_{k = 1,k \ne i}^{m} {z_{k} } \) and \( \bar{\varphi } = d\bar{\phi }/dp \), \( \mu = \sqrt { 2 {\text{b}}/ 3} \), \( \nu = 3/ 2\sqrt { 3 {\text{b}}/ 2} \), b = 1 or 2, and T 0,i = 4R i .
Fact 1: Best response of a player is unique, which is the stationary point if the stationary point is in [1, ∞). First we need to show that for any given z -i , there is only one unique maximal point for U i . In fact, player i needs to solve the following equations to get a candidate for a maximal point z m i :
where (Eq. 25) is a simplification of ∂U i /∂z i = 0. We can regard z m i and p as the implicit functions of z -i . Note that for any given z -i , there exists a unique pair of (z m i , p) as the solution to (Eq. 25) and (Eq. 26). In fact, the unique stationary point z m i obtained from this implicit function is indeed a maximal point. We can enlarge the domain of U i to be (0, ∞), and notice that z m i is also a unique stationary point for this enlarged domain. Since U i (0, z −i ) = 0 and \( \mathop {\lim }\limits_{{z_{i} \to \infty }} U_{i} = - \infty \), the values of two end points are not larger than U i (z m i , z −i ) given that z m i is indeed an interior point. Then we can conclude z m i is indeed a maximal point in domain (0, ∞). If z m i is still a stationary interior point in [1, ∞), then it also must be a maximal point. We can show that z m i = f i (z −i ) and p = f p (z −i ) are continuous functions on domain z -i ∈ (0,∞), in which f i (z -i ) is referred to as the best response function. In addition, from implicit function theorem, we know that they are continuously differentiable.
Now, we go on to prove the existence and uniqueness of NE. Consider two arbitrary players i and j, and let \( \delta_{i} z_{i} = \sum\nolimits_{k = 1,k \ne i}^{m} {z_{k} } \);\( \delta_{j} z_{j} = \sum\nolimits_{k = 1,k \ne j}^{m} {z_{k} } \).
When ∂U i /∂z i = ∂U j /∂z j = 0, we have:
Let \( \Delta = \beta \bar{\varphi }/((1 - p)\bar{\varphi } + \bar{\phi }) \), then combining (Eq. 27) and (Eq. 28) leads to
For (Eq. 29) to be true, we need either ∆ = 1 or δ i = δ j . We can show that ∆ = 1 cannot be true. We prove this by contradiction. Assume that it is true, then we can substitute it into (Eq. 27), and get β = 1−p. Substituting β = 1−p into ∆ = 1, we get φ = 0. We know that φ = 0 is impossible given that p ∈ (0, 1), thus ∆ ≠ 1. Thus, the only possible solution is δ i = δ j , ∀i, j. This implies that \(z_{i}^{*} = z_{j}^{*}\), i.e., \( n_{i}^{*} /n_{j}^{*} = R_{i} /R_{j} \) at NE n ne if it exists.
In the following, we prove that, when \( n_{i}^{*} /n_{j}^{*} = R_{i} /R_{j} \), there exists a unique solution \(p^{*}\) for (Eq. 23). Then we can conclude that there is one unique n ne .
Since at NE all players have the same number of paths, from (Eq. 24), we obtain:
Let F(p) denote the left-hand-side of (Eq. 30). Ideally, solving equation (Eq. 30) with p as unknown, we can get the loss rate at NE \(p^{*}\). Then, substituting \(p^{*}\) back into (Eq. 30), we can get n ne as the number of paths of all players at NE. However, (Eq. 30) contains several powers of p such as 7/2 and 5/2, thus it is impossible to get an algebraic solution of p. Thus, in the following, we examine several properties of F(p), from which we make an inference about the behavior of NE. For an exact value of \(p^{*}\) and n ne when given a network setting, we can use Matlab to numerically solve for them.
First, we prove that (Eq. 30) has only one solution for p in (0, 1). Note that F (p) is a continuous function, and the domain of F (p) is p ∈ (0, 1), and lim p→0 F (p) > 0 and limp→1 F (p) < 0. We claim that F (p) is a strictly monotonic decreasing function. If this claim is true, then there must be a single solution \(p^{*}\) for F (p) = 0. In the following, we prove this claim.
Consider the derivative
Thus, to prove that ∂F/∂p < 0, we only need to prove that \( \bar{\varphi }^{ 2} \) > \( \bar{\varphi }^{\prime} \) \( \bar{\phi } \). This can be easily proved.
Then, substituting \(p^{*}\) back into (Eq. 30), we can get \(n_{i}^{*}\) as the number of paths of the ith player at NE. Therefore, we conclude that there is only one NE for this game and it is symmetric. That is, \( z_{1}^{*} = z_{i}^{*} = \arg \max_{{n_{i} \in S_{i} }} U_{i} (z_{1}^{*} ,z_{2}^{*} , \ldots ,z_{i}^{*} , \ldots ,z_{m}^{*} ) \) and \(z_{i}^{*} = z_{j}^{*}\), thus \( n_{i}^{*} /n_{j}^{*} = R_{i} /R_{j} \), ∀i at NE n ne if it exists.
Therefore, F (p, m) is a monotonic decreasing function of p, and F (\(p^{*}\) , m) = 0. Since F (p 0 , m) < 0, \(p^{*}\) must be smaller than p 0 . When p < p 0 , we get dF/dm = 1/β − 1/(1 − p) = 1/(1 − p0) − 1/(1 − p) > 0. Thus, as m increases, F(p,m) is strictly monotonic increasing. Since F(p,m) is a monotonic decreasing function of p, we see that as m increases, for any given F(p), p will be strictly increasing towards p 0 . Then, it must be also true that for F (p *) = 0, as m increases, p approaches to p 0 .
Recall that at NE, we must have \( (1 - p^{*} )/R_{i} \bar{\phi }^{*} = C/mn_{i}^{*} \). Since all players must have at least one path, i.e., \(n_{i}^{*}\) ≥ 1, we must make sure that \( m(1 - p^{*} )/R_{\text{i}} \bar{\phi }^{*} \le C \). We know that as m increases, \(p^{*}\) → p 0 = 1−β, then \( R_{i} \bar{\phi }^{*} \) (as a function of \(p^{*}\)) also increases to \( R_{i} \bar{\phi }_{0}^{*} \) (function of p 0 ). Thus, \( (1 - p^{*} )/R_{i} \bar{\phi }^{*} \) is bounded below by \( (1 - {\text{p}}_{0} )/R_{\text{i}} \bar{\phi }_{0}^{*} \). So, as m becomes larger and larger, eventually, \( m(1 - p^{*} )/R_{\text{i}} \bar{\phi }^{*} \) will be larger than C, and NE is no longer an interior point. Supposing R 1 is the minimum RTT, and \( m(1 - p^{*} )/R_{ 1} \bar{\phi }^{*} \) is the largest value for all m(1 − \(p^{*}\))/\( R_{\text{i}} \bar{\phi }^{*} \), ∀i. Let m 0 denote this threshold, then it is the largest m satisfying \( m(1 - p^{*} )/R_{ 1} \bar{\phi }^{*} = m(1 - p^{*} )B_{1}^{*} \le {\text{C}} \). Since it is difficult to obtain an explicit expression of p as a function of m, we rely on the numerical method to identify m 0 .
Rights and permissions
About this article
Cite this article
Wang, J., Liao, J., Li, T. et al. Asymmetrical Multi-path Selection Game for Wireless Overlay Networks. Wireless Pers Commun 85, 2407–2429 (2015). https://doi.org/10.1007/s11277-015-2912-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2912-2