Abstract
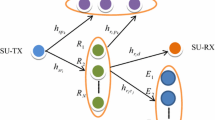
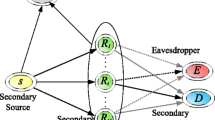
In this paper, we study performances of cooperative relay networks in cognitive radio with reactive multiple decode-and-forward (DF) relays. In particular, we first derive exact and asymptotic expressions of outage probability for the considered scheme with K-th best relay selection over Rayleigh fading channel. Next, in the presence of an eavesdropper and the same relay selection scheme, secrecy performance of the cognitive relay network is also evaluated, in terms of average secrecy capacity. We then perform Monte-Carlo simulations to verify the theoretical derivations. Our results have presented the significance of using relay networks to enhance the system and secrecy performance of cognitive reactive DF relay networks.







Similar content being viewed by others
References
Ghasemi, A., & Sousa, E. S. (2007). Fundamental limits of spectrum-sharing in fading environments. IEEE Transactions on Wireless Communications, 6, 649–658.
Duong, T. Q., Yeoh, P. L., Bao, Vo Nguyen Quoc, Elkashlan, M., & Yang, N. (2012). Cognitive relay networks with multiple primary transceivers under spectrum sharing. IEEE Signal Processing Letters, 19, 741–744.
Duy, T. T., & Kong, H. Y. (2014). Adaptive cooperative decode-and-forward transmission with power allocation under interference constraint. Wireless Personal Communications, 74, 401–414.
Bletsas, A., Shin, H., & Win, M. Z. (2007). Cooperative communications with outage-optimal opportunistic relaying. IEEE Transactions on Wireless Communications, 6, 3450–3460.
Suraweera, H. A., Smith, P. J., & Shafi, M. (2010). Capacity limits and performance analysis of cognitive radio with imperfect channel knowledge. IEEE Transactions on Vehicular Technology, 59, 1811–1822.
Duong, T. Q., da Costa, D. B., Elkashlan, M., & Bao, V. N. Q. (2012). Cognitive amplify-and- forward relay networks over Nakagami-m fading. IEEE Transactions on Vehicular Technology, 61, 2368–2374.
Kim, K. J., Duong, T. Q., & Tran, X.-N. (2012). Performance analysis of cognitive spectrum-sharing single-carrier systems with relay selection. IEEE Transactions on Signal Processing, 60, 6435–6449.
Duong, T. Q., Duy, T. T., Matthaiou, M., Tsiftsis, T., & Karagiannidis, G. K. (2013). Cognitive cooperative networks in dual-hop asymmetric fading channels. In Proceedings of IEEE Global Communications Conference (Globecom), Atlanta, GA, (pp. 977-983).
Bao, V. N. Q., Duong, T. Q., da Costa, D. B., Alexandropoulos, G. C., & Nallanathan, A. (2013). Cognitive amplify-and-forward relaying with best relay selection in non-identical Rayleigh fading. IEEE Communications Letters, 17, 475–478.
Sagong, S., Lee, J., & Hong, D. (2011). Capacity of reactive DF scheme in cognitive relay networks. IEEE Transactions on Wireless Communications, 10, 1276–1536.
Duy, T. T., & Kong, H. Y. (2013). Performance analysis of incremental amplify-and-forward relaying protocols with nth best partial relay selection under interference constraint. Wireless Personal Communications, 71, 2741–2757.
Zhang, X., Yan, Z., Gao, Y., & Wang, W. (2013). On the study of outage performance for cognitive relay networks (CRN) with the Nth best-relay selection in Rayleigh-fading channels. IEEE Transactions on Wireless Communications, 2, 110–113.
Wyner, A. D. (1975). The wire-tap channel. Bell System Techical Journal, 54, 13551367.
Bloch, M., Barros, J., Rodrigues, M. R. D., & McLaughlin, S. W. (2008). Wireless information theoretic security. IEEE Transactions on Information Theory, 54, 2515–2534.
Gopala, P. K., Lai, L., & Gamal, H. E. (2008). On the secrecy capacity of fading channels. IEEE Transactions on Information Theory, 54, 4687–4698.
Wang, L., Yang, N., Elkashlan, M., Yeoh, P. L., & Yuan, J. (2014). Physical layer security of maximal ratio combining in two-wave with diffuse power fading channels. IEEE Transactions on Information Forensics and Security, 9, 247–258.
Elkashlan, M., Wang, L., Duong, T. Q., Karagiannidis, G. K., & Nallanathan, A. (2014). On the security of cognitive radio networks. IEEE Transactions on Vehicular Technology. doi:10.1109/TVT.2014.2358624.
Yang, N., Yeoh, P. L., Elkashlan, M., Schober, R., & Collings, I. B. (2013). Transmit antenna selection for security enhancement in mimo wiretap channels. IEEE Transactions on Communications, 61, 144–154.
Yang, N., Yeoh, P. L., Elkashlan, M., Schober, R., & Yuan, J. (2013). MIMO wiretap channels: Secure transmission using transmit antenna selection and receive generalized selection combining. IEEE Communications Letters, 17, 1754–1757.
Wang, L., Elkashlan, M., Huang, J., Schober, R., & Mallik, R. K. (2014). Secure transmission with antenna selection in MIMO Nakagami-m channels. IEEE Transactions on Wireless Communications, 13, 6054–6067.
Wang, L., Elkashlan, M., Huang, J., Tran, N. H., & Duong, T. Q. (2014). Secure transmission with optimal power allocation in untrusted relay networks. IEEE Wireless Communications Letters, 3, 289–292.
Wang, L., Kim, K. J., Duong, T. Q., Elkashlan, M., & Poor, H. V. (2015). Security enhancement of cooperative single carrier systems. IEEE Transactions on Information Forensics and Security, 10, 90–103.
Liu, Y., Wang, L., Duy, T. T., Elkashlan, M., & Duong, T. Q. (2015). Relay selection for security enhancement in cognitive relay networks. IEEE Wireless Communications Letters, 4, 46–49.
Duy, T. T., & Kong, H. Y. (2013). Performance analysis of two-way hybrid decode-and-amplify relaying scheme with relay selection for secondary spectrum access. Wireless Personal Communications, 69, 857–878.
Lee, J., Wang, H., Andrews, J. G., & Hong, D. (2011). Outage probability of cognitive relay networks with interference constraints. IEEE Transactions on Wireless Communications, 10, 390395.
Gradshteyn, I., & Ryzhik, I. (2007). Table of integrals, series, and products (7th ed.). New York, London: Academic Press Inc.
Duong, T. Q., Duy, T. T., Elkashlan, M., Tran, Nghi. H., & Dobre, Octavia A. (2014). Secured cooperative cognitive radio networks with relay selection. In Proceedings of IEEE Globecom2014, Austin, TX USA, (pp. 3151-3156).
Bao, V. N. Q., & Duy, T. T. (2012). Performance analysis of cognitive underlay DF relay protocol with Kth best partial relay selection. In Proceedings of ATC2012, Ha Noi, VietNam, (pp. 130-135).
Duy, T. T., Duong, T. Q., da Costa, D. B., Bao, V. N. Q., & Elkashlan, M. (2015). Proactive relay selection with joint impact of hardware impairment and co-channel interference. IEEE Transactions on Communications, 63, 1594–1606.
Acknowledgments
This research is funded by Vietnam National Foundation for Science and Technology Development (NAFOSTED) under Grant Number 102.04-2013.13.
Author information
Authors and Affiliations
Corresponding author
Additional information
This paper has been presented in part as the best paper in Signal Processing and Communications Symposium at the IEEE CHINACOM, Maoming, China, August 2014.
Appendix: A Detailed Derivation of (31)
Appendix: A Detailed Derivation of (31)
Using Eqs. (25), (26), and (30), the corresponding asymptotic outage probability of (17) is given by
Using again Eqs. (56) and (30) for (19), we get (57) as
Thus, combining (56) and (57), we can obtain \(\tilde{P}_\mathrm{out}\). Similarly, an asymptotic expression for \(\tilde{P}_\mathrm{H,out}\) in the homogeneous networks can be readily computed as \(\tilde{P}_\mathrm{H,out}\) in (31).
Rights and permissions
About this article
Cite this article
Ha, DB., Vu, T.T., Duy, T.T. et al. Secure Cognitive Reactive Decode-and-Forward Relay Networks: With and Without Eavesdropper. Wireless Pers Commun 85, 2619–2641 (2015). https://doi.org/10.1007/s11277-015-2924-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2924-y