Abstract
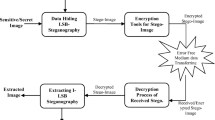
The popularity of wireless multimedia applications in real life and the open nature of wireless media for access make the security of confidential multimedia over wireless channels a major task. This paper proposes a two multi-layer security algorithm using steganography with encryption that strengthens the image security through its transmission over a wireless channel. The steganography conceals the data existence within a cover medium, while the encryption hides the data meaning by using specific algorithms. The suitability of image as a cover medium is due to abundance of redundant bits, and bulk data capacity. The chaos based encryption algorithms are adopted in this paper. In this work a confidential image is embedded into a cover image using least significant bit steganography, and then the output stego image is encrypted using a 2-D Logistic map or 2-D chaotic Baker map. The encrypted stego image is then transmitted over a wireless AWGN channel and the reverse processes are implemented to extract the received secret image. Several experiments have been carried out to examine the suitability of the proposed algorithms for securing high sensitivity images through transmission over wireless channels at different noise levels.




























Similar content being viewed by others
References
Raja, K. B., Chowdary, C. R., Venugopal, K. R., & Patnaik, L. M. (2005). A secure image steganography using LSB, DCT and compression techniques on raw images. In IEEE-0-7803-9588-3/05/$20.00 ©2005.
Neeta, D., Wagh, K. K., Snehal, K., & Jacobs, D. (2006). Implementation of LSB steganography and its evaluation for various bits. In 1st international conference on digital information management (pp. 173–178).
Juneja, M., & Sandhu, P. S. (2009). Designing of robust image steganography technique based on LSB insertion and encryption. In International conference on advances in recent technologies in communication and computing.
Chen, G. R., Mao, Y. B., & Chui, C. K. (2004). A symmetric image encryption scheme based on 3D chaotic cat map. Chaos, Solitons & Fractals, 21, 749–761.
Pareek, N. K., Patidar, V., & Sud, K. K. (2006). Image encryption using chaotic logistic map. Image and Vision Computing, 24, 926–934.
Arun, A. S., & Joseph, G. M. (2013). High security cryptographic technique using steganography and chaotic image encryption. IOSR Journal of Computer Engineering, 12(5), 49–54.
Mehta, A. M., Lanzisera, S., & Pister, K. S. J. (2008). Steganography in 802.15.4 wireless communication. In 2nd international symposium on advanced networks and telecommunication systems, ANTS.
Choudhary, K. (2012). Image steganography and global terrorism. Global Security Studies, 3(4), 115–135.
Kamal, A. H. M. (2013). Steganography: Securing message in wireless network. International Journal of Computers & Technology, 4(3), 797–801.
Owens, M. (2002). A discussion of covert channels and steganography. Bethesda, MD: SANS Institute.
Johnson, N. F., & Jajodia, S. (1998). Exploring steganography: Seeing the unseen. Computer Journal, 31(2), 26–34.
Chen M., Zhang, R., Niu, X., & Yang Y. (2006). Analysis of current steganography tools: Classifications & features. In International conference on intelligent information hiding and multimedia signal processing (IIH-MSP’06), IEEE-0-7695-2745-0/06 $20.00 © 2006.
Stuti, G., Rana, A., & Kaur, M. (2013). Comparison of image steganography techniques. International Journal of Computers and Distributed Systems, 3(I), 20–30.
Pareek, N. K., Patidar, V., & Sud, K. K. (2006). Image encryption using chaotic logistic map. Science Direct, Image and Vision Computing, 24, 926–934.
Srividya, G., Nandakumar, P. (2011). A Triple-Key chaotic image encryption method. In 2011 international conference on communications and signal processing (ICCSP) (pp. 266–270).
Ahmad, M., & Alam, M. S. (2009). A new algorithm of encryption and decryption of images using chaotic mapping. International Journal on Computer Science and Engineering, 2(1), 46–50.
Fridrich, J. (1998). Symmetric ciphers based on two-dimensional chaotic maps. International Journal of Bifurcation and Chaos, 8, 1259–1284.
El-Bendary, M. A. M., Abou-El-azm, A. E., El-Fishawy, N. A., Shawki, F., El-Tokhy, M. A. R., & Kazemian, H. B. (2012). Performance of the audio signals transmission over wireless networks with the channel interleaving considerations. EURASIP Journal on Audio, Speech, and Music Processing, 2012, 4. doi:10.1186/1687-4722-2012-4.
Soliman, N. F., Albagory, Y., Elbendary, M. A. M., Al-Hanafy, W., El-Rabaie, E. M., Alshebeili, S. A., & Abd El-Samie, F. E. (2014). Chaotic interleaving for robust image transmission with LDPC Coded OFDM. Wireless Personal Communications, 79(3), 2141–2154.
Silva, E. A., Panetta, K., Agaian, S. S. (2007). Quantifying image similarity using measure of enhancement by entropy. In SPIE proceedings Vol. 6579, mobile multimedia/image processing for military and security applications.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Nassar, S.S., Ayad, N.M., Kelash, H.M. et al. Secure Wireless Image Communication Using LSB Steganography and Chaotic Baker Ciphering. Wireless Pers Commun 91, 1023–1049 (2016). https://doi.org/10.1007/s11277-016-3387-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-016-3387-5