Abstract
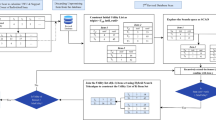
Big data is being widely used in various fields and the accuracy and calculation cost regarding the search results of big data are being researched constantly. In this paper, a big data access reduction scheme based on total probability theory is proposed to improve the accuracy and minimize calculation cost of big data search. The proposed scheme uses the reduction approach of divide-and-conquer; that is, it distinguishes all the attributes of data so as to minimize the data. Also, to improve the efficiency of data access, the proposed scheme assigns the attribute information in accordance with the properties of big data access to minimize the required amount of information to classify the information in the big data group into tuple based on the probability values, in order to apply the least randomness within the big data group. In particular, the proposed scheme aims to improve data access compared to the existing methods by connecting the probability values among the data to access the divided data more easily. The performance evaluation results show that compared to the existing method, the proposed scheme improved accuracy by 7.1%, decreased data storage space by 3.8%, and shortened the process time by 11.1%.





Similar content being viewed by others
References
Hu, H., Wen, Y., Chua, T. S., & Li, X. (2014). Toward scalable systems for big data anaqlytics: A technology tutorial. IEEE Access, 2, 652–687.
Russom, P. (2011). Big data analytics. TDWI Research Fourth Quarter, p. 6.
Gadepally, V., & Kepner, J. (2014). Big data dimensional analysis. In Proceedings of 2014 IEEE high performance extreme computing conference (HPEC) (pp. 1–6), Sep 2014.
Demchenko, Y., De Laat, C., & Membrey, P. (2014). Defining architecture components of the big data ecosystem. In Proceedings of 2014 international conference on collaboration technologies and systems (CTS) (pp. 104–112).
Manyika, J., Chui, M., Brown, B., Bughin, J., Dobbs, R., Roxburgh, C., & Byers, A. H. (2011). Big data: The next Frontier for innovation, competition and productivity (pp. 1–137). Mckinsey Global Institute.
Leskovec, J., Krause, A., Guestrin, C., Faloutsos, C., Vanbriesen, J., & Glance, N. (2007). Cost-effective outbreak detection in networks. In Proceedings of the 13th ACM SIGKDD international conference on Knowledge discovery and data mining (KDD ‘07) (pp. 420–429).
Chen, K., Zhou, Y., Zha, H., He, J., Shen, P., & Yang, X. (2013). Cost-effective node monitoring for online hot event detection in sina weibo. In Proceedings of the 22nd international conference on World Wide Web, ACM (pp. 107–108).
Kempe, D., Klenberg, J., & Tardos, E. (2003). Maximizing the spread of influence through a social network. In Proceedings of the ninth ACM SIGKDD international conference on Knowledge discovery and data mining (pp. 137–146).
Kim, S. H., Kim, N. U., & Chung, T. M. (2013). Attribute relationship evaluation methodology for big data security. In 2013 International conference on IT convergence and security (ICITCS) (pp. 1–4).
Son, S. Y. (2013). Big data, online marketing and privacy protection. KISDI Premium Report, 13(1), 1–26.
Kim, J. T., Oh, B. J., & Park, J. Y. (2013). Standard trends for the bigdata technologies. Electronics and Telecommunications Trends, 28(1), 92–99.
Shen, P., Zhou, Y., & Chen, K. (2013). A probability based subnet selection method for hot event detection in sina weibo microblogging. In Proceedings of 2013 IEEE/ACM international conference on advances in social networks analysis and mining (pp. 1410–1413).
Shrivastba, K. M. P., Rizvi, M. A., & Singh, S. (2014). Big data privacy based on differential privacy a hope for big data. In Proceedings of 2014 international conference on computational intelligence and communication networks (pp. 776–781).
Katal, A., Wazid, M., & Goudar, R. H. (2013). Big data: Issues, challenges, tools and good practices. In Proceedings of 2013 sixth international conference on contemporary computing (IC3) (pp. 404–409).
Jung, Y. C. (2012). Big data revolution and media policy issues. KISDI Premium Report, 12(2), 1–22.
Paryasto, M., Alamsyah, A., Rahardjo, B., Kuspriyanto (2014). Big-data security management issues. In Proceedings of 2014 2nd international conference on information and communication technology (ICoICT) (pp. 59–63).
Acknowledgements
This Research was supported by the Tongmyong University Research Grants 2016. Funding was provided by Seung-Soo Shin.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Jeong, YS., Shin, SS. An Efficient Access Reduction Scheme of Big Data Based on Total Probability Theory. Wireless Pers Commun 93, 7–19 (2017). https://doi.org/10.1007/s11277-016-3920-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-016-3920-6