Abstract
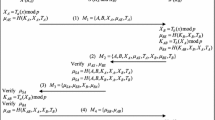
More than two participants implement communication over the network at the same time, aiming to establish a common session key, and it is named group session communication. Nowadays, many researchers lay emphasis on achieve a perfect group key agreement protocol in order to resist various attacks and complete mutual authentication for every two-party among them. Actually, investigators have overlooked an important issue called insider attack, which the inner participants could disclose the source of the messages to outsider parties. Therefore, in this paper, we present a novel group key agreement protocol with deniable authentication to against insider attack. After achieve the process of deniable authentication, the group participants unable to reveal the source of the messages to another party because any subgroup participants still can simulate the whole transcript process. Meanwhile, our protocol based on chaotic maps algorithm, which enhance the calculation efficiency and realize the goal of privacy protection successful.


Similar content being viewed by others
References
Bresson, E., Chevassut, O., & Pointcheval, D. (2002). Group Diffie–Hellman key exchange secure against dictionary attacks. Advances in Cryptology, 2501, 497–514.
Wang, L. M., & Wu, C. K. (2006). Identity based group key agreement from bilinear pairing. WuHan University Journal of Natural Sciences, 11(6), 1731–1735.
Guo, X., & Zhang, J. (2010). Secure group key agreement protocol based on chaotic Hash. Information Sciences, 180(20), 4069–4074.
Teng, J. K., Wu, C. K., & Tian, Y. L. (2015). A strongly secure identity-based authenticated group key exchange protocol. Science China Information Sciences, 58(9), 1–12.
Han, S. (2008). Security of a key agreement protocol based on chaotic maps. Chaos, Solitons and Fractals, 38(3), 764–768.
Li, C. C., Chen, C. L., Wu, C. Y., & Huang, S. Y. (2012). An extended chaotic maps-based key agreement protocol with user anonymity. Nonlinear Dynamics, 69(1), 79–87.
Xie, Q., Zhao, J. M., & Yu, X. Y. (2013). Chaotic maps-based three-party password-authenticated key agreement scheme. Nonlinear Dynamics, 74(4), 1021–1027.
Yau, W. C., & Phan, R. C. W. (2015). Cryptanalysis of a chaotic map-based password-authenticated key agreement protocol using smart cards. Nonlinear Dynamics, 79(2), 809–821.
Dwork, C., & Sahai, A. (1998). Concurrent zero-knowledge: Reducing the need for timing constraints. In Advances in Cryptology - CRYPTO ’98, International Cryptology Conference, Santa Barbara, California, USA, August 23-27, 1998, Proceedings (pp. 442–457). DBLP.
Deng, X., Lee, C. H., & Zhu, H. (2001). Deniable authentication protocols. IEE Proceedings on Computers and Digital Techniques, 148(2), 101–104.
Fan, L., Xu, C. X., & Li, J. H. (2002). Deniable authentication protocol based on Diffie-Hellman algorithm. Electronics Letters., 38, 705–706.
Lee, W.-B., Wu, C.-C., & Tsaur, W.-J. (2007). A novel deniable authentication protocol using generalized ElGamal signature scheme. Information Sciences, 177(6), 1376–1381.
Li, F., Xiong, P., & Chun, J. (2014). Identity-based deniable authentication for ad hoc networks. Computing, 96(9), 843–853.
Wang, B., & Song, Z. X. (2009). A non-interactive deniable authentication scheme based on designated verifier proofs. Information Sciences, 179(6), 858–865.
Hwang, S. J., & Chao, C. H. (2010). An efficient non-interactive deniable authentication protocol with anonymous sender protection. Journal of Discrete Mathematical Sciences and Cryptography, 13(3), 219–231.
Li, F., & Takagi, T. (2013). Cryptanalysis and improvement of robust deniable authentication protocol. Wireless Personal communications, 69(4), 1391–1398.
Bohli, J. M., & Steinwandt, R. (2006). Deniable group key agreement. VIETCRYPT, 4341, 298–311.
Wang, X., & Zhao, J. (2010). An improved key agreement protocol based on chaos. Communications in Nonlinear Science and Numerical Simulation, 15, 4052–4057.
Zhang, L. (2008). Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos, Solitons & Fractals, 37(3), 669–674.
Tsai, J. L. (2011). A novel authenticated group key agreement protocol for mobile environment. Annals of Telecommunications, 66(11-12), 663–669.
Xu, C., Hua, G., Li, Z., & Mu, Y. (2014). Affiliation hiding authenticated asymmetric group key agreement based on short signature. The Computer Journal, 57(10), 1580–1590.
Teng, J., & Wu, C. (2012). A provable authenticated certificateless group key agreement with constant rounds. Communications and Networks, 14(1), 104–110.
Kocarev, L., & Lian, S. (2011). Chaos-based cryptography: Theory, algorithms and applications (pp 53–54). Springer.
Barreto, P., Lynn, B. & Scott, M. (2004). On the selection of pairing-friendly groups, In: Selected areas in cryptography, LNCS (Vol. 3006, pp. 17–25). Springer.
Diffie, W., & Hellman, M. (1976). New directions in cryptography. IEEE Transaction on Information Theory, 22(6), 644–654.
Acknowledgements
This work is supported by the Liaoning Provincial Natural Science Foundation of China (Grant No. 201602680).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhu, H., Zhang, Y. An Efficient Chaotic Maps-Based Deniable Authentication Group Key Agreement Protocol. Wireless Pers Commun 96, 217–229 (2017). https://doi.org/10.1007/s11277-017-4163-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-4163-x