Abstract
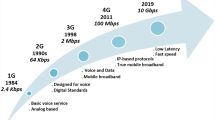
5G network technologies are generally expected to empower wireless communications to enable communication for anybody; of anything and anywhere, i.e. to finally fulfil the mobility promises made since the 2G introduction in the early 1990’s. A generally accepted technology vision is that new services and applications especially related to social networking, and machine-to-machine communications will be accelerated, underlining the shift to a more user centric application-driven connectivity, transparently deployed over various technologies and infrastructures by users and devices. A key challenge for realizing the vision is, however, “How will the technology system handle user data?” For the user centric and data centric 5G technologies to be accepted and function as a viable business model, user trust in their data privacy is paramount. Today personal data have become an economic asset belonging to the service providers whose business case often includes and is dependent on the use and selling of such data. The aim of the paper is to discuss user privacy concerns in today’s and tomorrow’s information society with a focus on economic aspects. The paper will further discuss the ‘privacy economy’ that will enable new business models focused on the economic value of private data

Similar content being viewed by others
References
Castells, M. (2009). Communication power. Oxford: Oxford University Press.
Fife, E., & Orjuela, J. (2012). The privacy calculus: Mobile apps and user perceptions of privacy and security. International Journal of Engineering Business Management, 4(1), 1–10.
BBC Series. (2010). The virtual revolution. http://www.bbc.co.uk/programmes/b00n4j0r/episodes/guide. Episode 2, “The cost of free”.
Leon, P. G., et al. (2015). Privacy and behavioral advertising: Towards meeting users’ preferences. In Symposium on usable privacy and security (SOUPS).
Futuresight. (2011). User perspectives on mobile privacy—Summary of research findings. GSMA.
Raine, L., et al. (2013). Anonymity, privacy, and security online. Pew Research Center.
Ericsson White Paper. (2015). 5G Security-Scenarios and Solutions, Uen 284 23-3269.
Lynggaard, P., & Skouby, K. E. (2015). Deploying 5G-technologies in smart city and smart home wireless sensor networks with interferences. Wireless Personal Communications, 81, 1399–1413.
White House. (2012). Consumer data privacy in a networked world: A framework for protecting privacy and promoting innovation. Journal of Privacy and Confidentiality , 2012, 95–142.
Reidenberg, J. R., et al. (2015). Disagreeable privacy policies: Mismatches between meaning and users’ understanding. Berkeley Technology Law Journal, 30(1), 39.
Castelluccia, C., et al. (2012). Privacy, accountability and trust—Challenges and opportunities. European Network and Information Security Agency (ENISA).
Khajuria, S., et al. (2015). Where does my private data go?-visualization of users’ privacy. In 48th annual Hawaii international conference on system sciences.
Electronic Frontier Foundation/Privacy Badger: http://www.eff.org/privacybadger.
MyPermissions: http://mypermissions.org/.
PC. (2014). http://www.pcworld.com/article/2147306/f-securefreedome-review-vpn-and-security-for-mobile-devices.html.
AVG PrivacyFix: http://www.avg.com/ww-en/privacyfix.
The World in 2025: 10 predictions of innovation. THOMSON REUTERS report, [Online]. Available: http://sciencewatch.com/sites/sw/files/m/pdf/World-2025.pdf.
Sørensen, L. T, et al. (2015). 5G visions of user privacy. In IEEE 81st vehicular technology conference (VTC Spring).
Chaplin, M., & Creasey, J. (2011). The 2011 standard of good practice for information security. Information Security Forum (ISF).
Regulation (EU) of the European Parliament and of the council “General Data Protection Regulation” Document 32016R0679 (2016).
Mortensen, H. (2016). Guildeline—General data protection regulation—Implementation in Danish companies. The Danish ICT and Electronics Federation, DI.
Hayek, Friederich. (1945). The use of knowledge in society. The American Economic Review, 35(4), 519–530.
Varian, H. R. Markets for information goods. http://people.ischool.berkeley.edu/~hal/Papers/japan/.
Acquisti, A., et al. (2016). The economics of privacy. Journal of Economic Literature, 52(2), 442–492.
Noam, E. (1997). Privacy and self-regulation: Markets for electronic privacy. In US Department of Commerce: Privacy and self-regulation in the information age. Washington.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Khajuria, S., Skouby, K.E. Privacy and Economics in a 5G Environment. Wireless Pers Commun 95, 145–154 (2017). https://doi.org/10.1007/s11277-017-4421-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-4421-y