Abstract
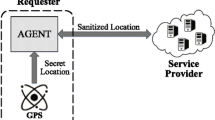
As location-based services (LBSs) require users to report their location to obtain services, many people are starting to realize the exposed to high privacy threats. In order to preserve the privacy, a great deal of privacy preserving algorithms is preserved in the last several years. Unfortunately, existing privacy preserving algorithms for LBSs usually mainly consider generalizing or cloaking the location and neglect the correlation probability between the query and location, and the adversary can use the probability to guess the real location. In this paper, based on the concept of differential privacy, we propose a mechanism for achieving probability indistinguishable, and then based on this mechanism a location-shift scheme to obfuscate the correlation between the query and location is proposed. To address the correlation probability obfuscation, we first show the correlation attack model with four potential methods based on the correlation probability. Then we study the proposed attacks on several existing algorithms designed for snapshot as well as continues services and define a formalization of probability indistinguishable to propose a countermeasure with location-shift, which can mitigate this type of attacks. At last, we verify the security of our location-shift scheme with entropy and mutual information, and the empirical evaluations further verify the effectiveness and efficiency of our scheme.







Similar content being viewed by others
References
Gruteser, M. & Grunwald, D. (2003). Anonymous usage of location-based services through spatial and temporal cloaking. In Proceedings of the 1st international conference on mobile systems, applications and services, San Francisco, California, pp. 31–42.
Gedik, B. & Ling, L. (2005). Location privacy in mobile systems: A personalized anonymization model. In Proceedings of 25th IEEE international conference on distributed computing systems. ICDCS 2005, pp. 620–629.
Fuyu, L., Hua, K. A., & Ying, C. (2009). Query l-diversity in location-based services. In Tenth international conference on mobile data management: Systems, services and middleware, 2009. MDM ‘09, pp. 436–442.
Rebollo-Monedero, D., Forne, J., Solanas, A., & Martinez-Balleste, A. (2010). Private location-based information retrieval through user collaboration. Computer Communications, 33, 762–774.
Rebollo-Monedero, D., Forne, J., & Domingo-Ferrer, J. (2012). Query profile obfuscation by means of optimal query exchange between users. IEEE Transactions on Dependable and Secure Computing, 9, 641–654.
Shokri, R., Theodorakopoulos, G., Papadimitratos, P., Kazemi, E., & Hubaux, J. P. (2014). Hiding in the mobile crowd: Location privacy through collaboration. IEEE Transactions on Dependable and Secure Computing, 11, 266–279.
Niu, B., Zhu, X. Y., Li, Q. H., Chen, J., & Li, H. (2015). A novel attack to spatial cloaking schemes in location-based services. Future Generation Computer Systems—The International Journal of Grid Computing and Escience, 49, 125–132.
Khoshgozaran, A., Shirani-Mehr, H., & Shahabi, C. (2008). SPIRAL: A scalable private information retrieval approach to location privacy. In 2008 Ninth international conference on mobile data management workshops, pp. 49–56.
Khoshgozaran, A., Shahabi, C., & Shirani-Mehr, H. (2011). Location privacy: Going beyond K-anonymity, cloaking and anonymizers. Knowledge and Information Systems, 26, 435–465.
Lien, I. T., Lin, Y.-H., Shieh, J.-R., & Wu, J.-L. (2013). A novel privacy preserving location-based service protocol with secret circular shift for k-NN search. IEEE Transactions on Information Forensics and Security, 8, 863–873.
Paulet, R., Kaosar, M. G., Yi, X., & Bertino, E. (2014). Privacy-preserving and content-protecting location based queries. IEEE Transactions on Knowledge and Data Engineering, 26, 1200–1210.
Ben, N., Qinghua, L., Xiaoyan, Z., Guohong, C., & Hui, L. (2015). Enhancing privacy through caching in location-based services. In 2015 IEEE conference on computer communications (INFOCOM), pp. 1017–1025.
Ma, C. G., Zhou, C. L., & Yang, S. T. (2015). A voronoi-based location privacy-preserving method for continuous query in LBS. International Journal of Distributed Sensor Networks, 2015, 1–17.
Schlegel, R., Chow, C. Y., Huang, Q., & Wong, D. S. (2015). User-defined privacy grid system for continuous location-based services. IEEE Transactions on Mobile Computing, 14, 2158–2172.
Wang, Y., Xia, Y., Hou, J., Gao, S. M., Nie, X., & Wang, Q. (2015). A fast privacy-preserving framework for continuous location-based queries in road networks. Journal of Network and Computer Applications, 53, 57–73.
Palanisamy, B., & Liu, L. (2015). Attack-resilient mix-zones over road networks: Architecture and algorithms. IEEE Transactions on Mobile Computing, 14, 495–508.
Gao, S., Ma, J. F., Shi, W. S., & Zhan, G. X. (2015). LTPPM: A location and trajectory privacy protection mechanism in participatory sensing. Wireless Communications & Mobile Computing, 15, 155–169.
Hwang, R.-H., Hsueh, Y.-L., & Chung, H.-W. (2014). A novel time-obfuscated algorithm for trajectory privacy protection. IEEE Transactions on Services Computing, 7, 126–139.
Ozer, M., Keles, I., Toroslu, H., Karagoz, P., Hakki, I., & Ergut, S. (2014). Predicting the next location change and time of change for mobile phone users. In Presented at the proceedings of the third ACM SIGSPATIAL international workshop on mobile geographic information systems, Dallas, Texas, 2014.
Xue, A. Y., Zhang, R., Zheng, Y., Xie, X., Huang, J., Xu, Z. et al. (2013). Destination prediction by sub-trajectory synthesis and privacy protection against such prediction. In 29th IEEE international conference on data engineering (ICDE), Brisbane, Australia, 2013, pp. 254–265.
Su, H., Zheng, K., Wang, H., Huang, J., & Zhou, X. (2013). Calibrating trajectory data for similarity-based analysis. In Proceedings of the 2013 ACM SIGMOD international conference on management of data, pp. 833–844.
Chen, X. H., Pang, J., & Xue, R. (2014). Constructing and comparing user mobility profiles. ACM Transactions on the Web, 8(21), 1–21.
Lei, Z., Chunguang, M., & Songtao, Y. (2016). Location association similar based anonymus algorithm. China Science Paper, 11, 197–201.
Niu, B., Qinghua, L., Xiaoyan, Z., Guohong, C., & Hui, L. (2014). Achieving k-anonymity in privacy-aware location-based services. In INFOCOM, 2014 proceedings IEEE, pp. 754–762.
Dwork, C. (2006). Differential privacy. In Lecture notes in computer science, pp. 1–12.
Xiong, L. (2013). Adaptive differentially private data release for data sharing and data mining. In 2013 IEEE 13th international conference on data mining workshops (Icdmw), pp. 891–891.
Cheng, X., Su, S., Xu, S. Z., & Li, Z. Y. (2015). DP-apriori: A differentially private frequent itemset mining algorithm based on transaction splitting. Computers & Security, 50, 74–90.
Xu, J., Zhang, Z. J., Xiao, X. K., Yang, Y., Yu, G., & Winslett, M. (2013). Differentially private histogram publication. VLDB Journal, 22, 797–822.
Riboni, D., & Bettini, C. (2015). Incremental release of differentially-private check-in data. Pervasive and Mobile Computing, 16, 220–238.
Dewri, R. (2013). Local differential perturbations: Location privacy under approximate knowledge attackers. IEEE Transactions on Mobile Computing, 12, 2360–2372.
Andrés, M. E., Bordenabe, N. E., Chatzikokolakis, K., & Palamidessi, C. (2013). Geo-indistinguishability: Differential privacy for location-based systems. In Proceedings of the 2013 ACM SIGSAC conference on computer & communications security, pp. 901–914.
Bordenabe, N. E., Chatzikokolakis, K., & Palamidessi, C. (2014). Optimal geo-indistinguishable mechanisms for location privacy. In Proceedings of the 2014 ACM SIGSAC conference on computer and communications security, pp. 251–262.
Primault, V., Mokhtar, S. B., Lauradoux, C., & Brunie, L. (2014). Differentially private location privacy in practice. Eprint Arxiv.
Chatzikokolakis, K., Palamidessi, C., & Stronati, M. (2015). Geo-indistinguishability: A principled approach to location privacy. In R. Natarajan, G. Barua, & M. R. Patra (Eds.), Distributed computing and internet technology, ICDCIT 2015, Vol. 89562015, pp. 49–72.
Perazzo, P., & Dini, G. (2015). A uniformity-based approach to location privacy. Computer Communications, 64, 21–32.
Acknowledgements
This work was supported by National Natural Science Foundation of China No. 61472097, Specialized Research Fund for the Doctoral Program of Higher Education No. 20132304110017, Natural Science Foundation of Heilongjiang Province of China No. F2015022.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Lei, Z., Chunguang, M., Songtao, Y. et al. Probability Indistinguishable: A Query and Location Correlation Attack Resistance Scheme. Wireless Pers Commun 97, 6167–6187 (2017). https://doi.org/10.1007/s11277-017-4833-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-4833-8