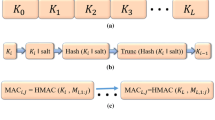
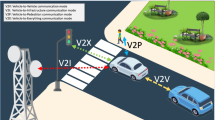
Abstract
In the recent paper, Nai-Wei Lo and Jia-Lun Tsai mathematically proposed an efficient authentication scheme for vehicular sensor network. It uses elliptic curve cryptography based ID-based signature (IBS) for authentication purpose without pairings. The proposed scheme provides secure authentication in Vehicle-to-RSU (V2R) and RSU-to-Vehicle (R2V) communications. But it does not provide secure Vehicle-to-Vehicle (V2V) communications. It also has few other drawbacks. Hence, we propose a new ID-based authentication scheme without pairings for vehicular networks. It provides secure V2R, R2V and V2V communications with other security features like privacy preservation, message integrity and tracability. In this paper, we first review the authentication scheme proposed by Nai-Wei Lo et al. along with its limitations. Then we illustrate the proposed IBS based authentication scheme without pairings. At last, the performance of the proposed scheme is compared with that of the Nai-Wei Lo et al.’s scheme. NS2 simulation result shows that the proposed scheme has less computation and communication overhead than the latter scheme.






Similar content being viewed by others
References
Azimi, R., Bhatia, G., Rajkumar, R., & Mudalige, P. (2011). Vehicular networks for collision avoidance at intersections. In Proceedings of SAE World Congress, Detroit, MI, USA, April 2011 (pp. 1–11).
Zeadally, S., et al. (2012). Vehicular ad hoc networks (VANETS): Status, results, and challenges. Telecommunication Systems, 50(4), 217–241.
Misener, J. A. (2005). Vehicle-infrastructure integration (VII) and safety: Rubber and radio meets the road in California. Intellimotion, 11(2), 1–3.
Lee, U., et al. (2006). Mobeyes: Smart mobs for urban monitoring with a vehicular sensor network. IEEE Wireless Communications, 13(5), 52–57.
Fuentes, J. M. D., et al. (2011). Overview of security issues in vehicular ad-hoc networks. In M. M. Cruz-Cunha & F. Moreira (Eds.), Handbook of research on mobility and computing (pp. 894–911), IGI Global. https://www.igi-global.com/.
Armknecht, F., et al. (2007). Cross-layer privacy enhancement and non-repudiation in vehicular communication. In Proceedings of ITG-GI conference on communication in distributed systems (KiVS) (pp. 1–12).
Yoon, H., Cheon, J. H., & Kim, Y. (2005). Batch verifications with ID-based signatures. In Proceedings of ICISC (pp. 233–248).
Zhang, C., Lu, R., Lin, X., Ho, P. -H., & Shen, X. (2008). An efficient identity based batch verification scheme for vehicular sensor networks. In Proceedings of IEEE INFOCOM (pp. 246–250).
Shim, K. A. (2010). An ID-based aggregate signature scheme with constant pairing computations. Journal of Systems and Software, 83(10), 1873–1880.
Shim, K. A. (2013). Reconstruction of a secure authentication scheme for vehicular ad hoc networks using a binary authentication tree. IEEE Transactions on Wireless Communications, 12(11), 5386–5393.
Barreto, P. S. L. M., Kim, H. Y., Lynn, B., & Scott, M. (2002). Efficient algorithms for pairing-based cryptosystems. In Proceedings of cryptology (pp. 354–368).
Tsai, J. L., & Lo, N. W. (2015). A privacy-aware authentication scheme for distributed mobile cloud computing services. IEEE Systems Journal, 9(3), 805–815.
Lo, N.-W., & Tsai, J.-L. (2016). An efficient conditional privacy-preservation scheme for vehicular sensor networks without pairings. IEEE Transactions on Intelligent Transportation Systems, 17(5), 1319–1328.
Hunag, J. L., Yeh, L. Y., & Chien, H. Y. (2011). ABAKA: An anonymous batch authenticated and key agreement scheme for value-added services in vehicular ad hoc networks. IEEE Transactions on Vehicular Technology, 60(1), 248–262.
Raya, M., et al. (2007). Securing vehicular ad hoc networks. Journal of Computer Security, 15(1), 39–68.
Shamir, A. (1984). Identity-based cryptosystems and signature schemes. In Advances in cryptology (pp. 47–53). New York, NY: Springer.
Yeh, L. Y., & Lin, Y. C. (2014). A proxy-based authentication and billing scheme with incentive-aware multihop forwarding for vehicular networks. IEEE Transactions on Intelligent Transportation Systems, 15(4), 1607–1621.
Intelligent Transportation Systems Committee. (2006). IEEE Trial-Use standard for wireless access in vehicular environments (WAVE)—Security services for applications and management messages, IEEE Std. 1609.2, July 2006.
Liu, J. K., Yuen, T. H., Au, M. H., & Susilo, W. (2014). Improvements on an authentication scheme for vehicular sensor networks. Expert Systems with Applications, 41(5), 2559–2564.
Pointcheval, D., & Stern, J. (2000). Security arguments for digital signatures and blind signatures. Journal of Cryptology, 13(3), 361–396.
Pointcheval, D., & Stern, J. (1996). Security arguments for digital signatures and blind signatures. In Proceedings of Eueocrypt (Vol. 1070, pp. 387–398).
Hubaux, J. P., Capkun, S., & Luo, J. (2004). The security and privacy of smart vehicles. IEEE Security Privacy Magazine, 2(3), 49–55.
Tsai, J. L., Lo, N. W., & Wu, T. C. (2013). Novel anonymous authentication scheme using smart cards. IEEE Transactions on Industrial Informatics, 9(4), 2004–2013.
Yan, G., Wen, D., Olariu, S., & Weigle, M. C. (2013). Security challenges in vehicular cloud computing. IEEE Transactions on Intelligent Transportation Systems, 14(1), 284–294.
Shim, K. A. (2012). CPAS: An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks. IEEE Transactions on Intelligent Transportation Systems, 61(4), 1874–1883.
Boneh, D., Gentry, C., Lynn, B., & Shacham, H. (2003). Aggregate and verifiably encrypted signatures from bilinear maps. Lecture Notes in Computer Science, 2656, 416–432.
Wasef, A., & Shen, X. (2013). Expedite message authentication protocol for vehicular ad hoc networks. IEEE Transactions on Mobile Computing, 12(1), 78–89.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Jenefa, J., Mary Anita, E.A. An Enhanced Secure Authentication Scheme for Vehicular Ad Hoc Networks Without Pairings. Wireless Pers Commun 106, 535–554 (2019). https://doi.org/10.1007/s11277-019-06178-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06178-4