Abstract
Intermittent connectivity due to the difficult topography in disaster area prevents a direct transmission from the base station to the demand users. An analytical framework to evaluate the reliability performance of the cellular network has been proposed. This project aims to evaluate the communication efficiency over the cellular network with the implementation of random linear network coding (RLNC) at the source node before transmission. The RLNC scheme employed in a new bounds algorithm provides a better estimation of the reliability performance of the communication over the cellular network. Thus, the decoding success probability in the communication, with and without the implementation of RLNC at the source node is developed. The implementation of the RLNC at the source node before transmission can increase the performance of the communication reliability over the cellular network from 2 to 82% under a high noise interference environment, d0 = 0.7 for M = 4, without requiring a large value of relay nodes at cluster 2. Thus, as the number of relay nodes at cluster 2 increases (M > N), the reliability of data exchange between the source and the destination node increases.
Similar content being viewed by others
1 Introduction
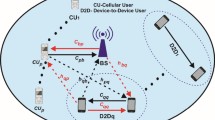
Intermittent connectivity due to the difficult topography in a disaster area prevents a direct transmission from the base station to the demand users. Nowadays, cellular mobile network has become a dominant communication technology in the world. Thus, cellular mobile network can be a help in supporting disaster recovery and relief operation in the disaster area. In addition, modern mobile devices are equipped with advanced signal processing capabilities and multiple radio interfaces such as WIFI and Bluetooth, which provide a broad range of application. Cellular mobile network based on the ad-hoc network, which is a communication service for a group of mobile users without requiring a fixed communication infrastructure, is the most preferred approach for supporting disaster recovery due to its low cost and power consumption for transmission. It has also been reported in [1] that adopting the mobile ad-hoc network had improved the robustness and reliability of the cellular network. Thus, the focus of this paper is on the communication network in a disaster area which uses the cooperative techniques between cellular and WIFI links as shown in Fig. 1.
The remainder of the paper is organized as follows. Section 2 is a review of the network coding (NC) and decoding probability. The methodology of this paper is discussed in Sect. 3. Section 4 contains the results and discussions of the reliability performance of the communication over a cellular network. Finally, Sect. 5 concludes this paper.
2 Literature Review
2.1 Network Coding (NC)
Ahlswede et al. [2] is the first person to propose the NC, achieving the maximum information flow in a single source multicast network. The NC is performed with Exclusive-OR (XOR) operator for data encoding and decoding at a node. NC is a novel technique for improving the network throughput, robustness and timeliness of a communication network. NC can be categorized into two types; inter-session and intra-session [3]. Inter-session NC encodes data from different data link connection to solve the bottleneck problem while the intra-flow NC encodes data from the same data link connection to prevent the data loss. Network model with NC has higher throughput and reliability compared to a network model without NC [4]. However, the throughput and reliability of a network model with NC depend on few factors such as the network geometry, signal to noise (SNR), operating point on the probability of throughput-outage, and a combination of multiple transmission. Furthermore, NC has significantly improved the message delivery probability compare to message replication as reported in [5] and it is because the NC reduces the network bandwidth to achieve the maximum data flow. The drawback of NC is that it can only perform well when the number of the message, M is lesser than the number of the encountered nodes, L.
Although inter-session NC improved the reliability of data exchanges between a transmitter and a receiver, an unnecessary redundancy is still being introduced. Thus, intra-flow NC is adopted in communication system to reduce the number of transmission by achieving spatial diversity [6]. Intra-session NC is more suitable in an ad-hoc communication compared to the inter-session NC [7]. This is because the intra-session NC is much more resilient to packets loss in ad-hoc network. However, intra-session NC had higher complexity computational compare to the inter-session NC. Thus, intra-session NC based RLNC, which encoded packets to a linear combination of coded packets using a randomly chosen coefficients from the elements of a finite field in the network. Linear NC is one type of the NC scheme, which replaced the XOR operator with a linear combination of the packets over a finite field size [8]. Thus, linear NC produces a larger degree of flexibility in the combination of the packet. Figure 2 shows the difference between linear network coding and network coding.
Although the latency, capacity and energy efficiency of communication network with packets loss has been improved with the implementation of RLNC [9, 10], the effectiveness of RLNC is limited by the number of network coded packets received at the destination. If the number of network coded packets received is lesser than the number of network coded packets transmitted, then the performance of the communication network is poor.
Since the packet losses in a cellular communication network at disaster area is very high, the receiver failed to regain the source information that had been sent by the transmitter. Thus, a cellular communication network based on the intra-session NC at the transmitter in an intermittent connectivity area is the best solution to solve the packet loss. This is because of the intra-session NC criteria which has higher resiliency to packet losses compared to the inter-session NC. Also, implementation of RLNC will improve the efficiency of cellular communication network due to the larger degree of flexibility in combination of packet. Therefore, in this paper, a cellular communication network based on RLNC at source node before transmission has been proposed.
2.2 Decoding Probability Algorithms
RLNC scheme is used to compute and evaluate the decoding performance with consideration of packet losses at a relay node [11, 12]. Galois Field size and the number of relays are the important characteristics of decoding performance at a destination node. A network with the smallest Galois Field size has poor performance even in the presence of low packet losses. However, the performance of [11] decreases as the number of sources increases due to the high complexity decoding probability computational. The author in [11] did not consider the packet losses between the relay and the destination node.
Next, the author in [13] has investigated another way to evaluate the performance of the RLNC with erasure channels. The proposed method had a lower complexity computational than the work in [11] and applicable to a larger scale of content distribution on decoding probability and much more efficient. However, the proposed bounds are limited to a large number of source nodes and large finite field size. Hence, the proposed bounds on decoding probability result are similar to the simulation result of a small number of source and finite field size.
Then, the author in [14] presented an improved bounds on decoding probability which has a better estimation of the performance of a communication system compare to the work in [11]. Besides that, it performed well in the condition where a large number of source nodes and finite field size is used. However, the proposed algorithm only perform well in a condition where the quantity of the source nodes is lesser than the quantity of the relay nodes. Then in [14], the improved version of bounds provides a better evaluation performance of the cooperative networks.
Thus, in this paper, the bounds failure probability algorithm proposed by [14], which employed a sparse RLNC scheme, is the best estimation in reliability performance of network coded MIMO over the cellular communication network under various condition. This algorithm will be enhanced by considering adopting the RLNC at the source node before the transmission.
3 Methodology
3.1 Investigate Bounds Failure Decoding Probability
Suppose a RLNC scheme shown in Fig. 3 with N source nodes, M relay nodes, and a destination, where M ≥ N [13]. All the transmitting data links are supposed to be independent of each other. All the relays generate a linear combination of messages (with XOR process) received from the N sources and delivered the coded packet to the destination. At the destination node, the coded data are then decoded by solving the linear equation.
Let the source packet denote as \(x \in {\mathbb{F}}_{q}^{N \times 1}\) where \({\mathbb{F}}_{q}^{N \times 1}\) is a finite field of size q with N × 1 vector of transmitted source message. The received coded packet defined as \(y \in {\mathbb{F}}_{q}^{M \times 1}\) and the network coefficient matrix is defined as \(\alpha \in {\mathbb{F}}_{q}^{M \times N}\). Therefore, the coded packet matrix is obtained as \(y_{j} = \sum\nolimits_{i = 1}^{N} {\alpha_{ji} x_{i} }\).
Note that all of the arithmetic operations at the relay nodes are performed over finite fields. To obtain the element matrix α [13], two erasure channel were considered; one is from the source to the relay, and the other is from the relay to the destination, which is determined by d1 and d2 respectively and expressed as.
The receiver can obtain the initial source packet providing the N independent data link out of the M independent coded packet. Thus, the upper and the lower bounds of decoding failure probability can be derived.
-
(a)
The proposed upper bound and lower bound of decoding failure probability algorithms in [13] for N source nodes and M relay nodes with packet loss probability of d1 and d2 over a finite field is presented in Eqs. (2) and (3) respectively:
$$\begin{aligned} P_{fail} \le & \frac{1}{q - 1}\sum\limits_{k = 1}^{N} {\left( {\begin{array}{*{20}c} N \\ k \\ \end{array} } \right)(q - 1)^{k} \times \left[ {d_{2} + (1 - d_{2} )} \right.} \\ & \left. { \times \left( {q^{ - 1} + (1 - q^{ - 1} )\left( {1 - \frac{{1 - d_{1} }}{{1 - q^{ - 1} }}} \right)^{k} } \right)} \right]^{M} \\ \end{aligned}$$(2)$$\begin{aligned} P_{fail} \ge & \sum\limits_{k = 1}^{N} {\left( {\begin{array}{*{20}c} N \\ k \\ \end{array} } \right)\left( {\left( {d_{1} + d_{2} - d_{1} d_{2} } \right)^{M} } \right)^{k} } \\ & \times \;\left( {1 - \left( {d_{1} + d_{2} - d_{1} d_{2} } \right)^{M} } \right)^{N - k} \\ \end{aligned}$$(3) -
(b)
The new upper and lower bound of decoding failure probability algorithms in [14] is based on Fig. 3 and is formulated in Eqs. (4) and (7) respectively.
where nmax(N,r) is the minimum probability that matrix α can have and α is an N × N non-singular matrix. μ0(N,r) is the expectation value of decoding failure at the destination and expressed in Eqs. (5) and (6) respectively.
where \(\beta_{\hbox{max} } = \hbox{max} \{ d_{1} ,\frac{{1 - d_{1} }}{q - 1}\}\) which specifies the maximum probability of obtaining an element from the finite field of size q.
The lower bound failure decoding probability is defined as below:
where nmin(N,r) and P0(N,r) is derived in Eqs. (8) and (9) respectively.
where \(\beta_{\hbox{min} } = \hbox{min} \left\{ {d_{1} ,\frac{{1 - d_{1} }}{q - 1}} \right\}\), which specifies the minimum probability of obtaining an element from the finite field of size q.
3.2 A Network Model With and Without the Implementation of RLNC at the Source Node
The reliability of communication over cellular network could be improved by employing intra network coding at source node before transmission. Re-encoding packets from a source at an intermediate node has been shown to improve the reliability performance of communication against packet losses [15]. Suppose that a network system with a source node, N and M relay nodes at the cluster 1 and cluster 2 respectively and a destination as shown in Fig. 4.
Assuming that there is no direct link between a source node to a destination node, all the supported connected links are independent of each other. The erasure probability of the links connecting from the source to relay nodes cluster 1, relay nodes cluster 1 to relay nodes cluster 2 and relay nodes cluster 2 to the destination, are denoted as d0, d1 and d2 as shown in Fig. 4. The RLNC algorithm was performed at the source node before the transmission which causes the source information fragmented into n data packets xi and generated m linear combination of messages yj while m ≥ n as expressed in Eq. (10).
where Cji is a coding matrix randomly generated from a finite field, \({\mathbb{F}}_{q}\).
Then, the m coded data packets will be transmitted to all the N relay nodes cluster 1. The coded data packets at N relay nodes cluster 1 is then transmitted simultaneously to all the M relay nodes cluster 2. The coded data packets are then recombined to generate an output at the destination. Thus, the coded packets are decoded and expressed as shown in Eq. (11).
where C −1ji are mʹ × n coding matrix, randomly generated from same finite field size, \({\mathbb{F}}_{q}\).
Note that no direct link between sources to a destination. All data transmitting links connecting source-relay nodes cluster 1, relay nodes cluster 1-relay nodes cluster 2, and relay nodes cluster 2-destination are modeled as memory-less erasure channels characterized by erasure probability. There is erasure probability of links connecting source-relay nodes cluster 1; relay nodes cluster 1-relay nodes cluster 2 and relay nodes cluster 2-destination which are denoted as d0, d1 and d2. Note that all erasure probabilities are in the range of 0–1. Let \({\bar{\varepsilon }}\) and ε denote as non-occurrence and occurrence of erasure probability for links between relay and destination. So, P{ε} = d2 and P{\({\bar{\varepsilon }}\)} = 1 − d2. The coding coefficient, \(\hat{C}_{ji}^{ - 1}\) are determined uniformly at random, zero coefficient is allocated for failure received packets and the successfully received data packet is uniformly allocation of non-zero coefficient. In order to obtain the element matrix C, the coding coefficient distribution from Eq. (1) is rewritten as below:
where θ is a dummy variable. The probability of erasure event for a jth link between relay and destination given that ε is true, thus P[\(\hat{C}_{ji}^{ - 1}\) = 0|ε] = 1 is set.
For a network with RLNC implemented at the source node before the transmission, the decoding success probability based on [14] is rewritten as
On the other hand, for a network without RLNC implemented at the source node before the transmission, if there was no source packet re-encoded at the intermediate node, and only inter-network coding network performed at the intermediate node, the decoding success probability based on [14] is rewritten as
4 Results and Discussion
4.1 Accuracy of Bounds Failure Probability Algorithms
The analysis of both bounds failure decoding probability algorithms from [13, 14] is presented. Few parameters can influence the estimation accuracy of the bounds failure probability algorithms. They are finite field size and the quantity of the relay nodes.
First of all, the impact of the finite field size on the estimation accuracy of the bounds failure decoding probability is illustrated in Fig. 5. A failure decoding probability that has a better estimation has a tight bound. Tight bound refer to the smallest gap between the upper and the lower band. From Fig. 5, by comparing the result shown in (a) and (d), notice that the new bounds algorithm (UBnew and LBnew) still provides tight bounds for a larger value of q (Fig. 5d). However, as can be seen from Fig. 5, the curve of the proposed upper bound (UBold) is moving further away from the lower bound (LBold) for a larger value of q. In addition, the proposed upper bound algorithm provides a poor simulation result when the q value is higher than 16 (q > 16). Thus, the new bounds failure probability provide a better estimation of the reliability of the cellular communication network compared to the proposed bounds algorithm.
Next, the effect of the quantity of the relay nodes on the accurate estimation of both bounds failure probability is shown in Fig. 6. According to [16], the receiver can recover the source packet if and only if the linear independent coded packet is larger than source packet (M ≥ N). Thus, the maximum value of failure decoding probability is equal to one when M < N. Notice that the proposed upper bounds algorithms (old UB) provides poor simulation result, where the value of Pfail is larger than one (Pfail > 1) as the M ≤ 1.5 N. On the other hand, the new upper bound algorithms (new UB) provide a maximum value of failure decoding probability as M approaches to N. In addition, the new bounds algorithm provides a tighter bound as M approaches to N compared to the proposed bounds algorithms. However, both bounds failure algorithms provides a tight bound for a larger value of relay nodes. Thus, the new bounds failure decoding probability algorithms is better and much more accurate compared to the proposed bounds algorithms.
The effect of the erasure probability in the link between the relay and the destination nodes on accurate estimation of both bounds algorithms are shown in Fig. 7. The proposed upper bounds algorithm shows a poor simulation result where Pfail is larger than one (Pfail > 1) when d2 is larger than 0, as illustrated in Fig. 7a. Furthermore, notice that the erasure probability d2 will not influence the tightness of new bounds failure probability as shown in Fig. 7b. Thus, the new bounds algorithms failure probability perform well and accurate in estimating the reliability performance of the communication over the cellular network either in the small or large value of erasure probability d2. The summary of the simulation parameters influencing the accuracy estimation of reliability performance of network model is tabulated in Table 1.
As can be seen from Table 1, it can be concluded that the new bounds failure decoding probability is better than the proposed bounds in estimating the performance reliability of a network model. Thus, the new bounds algorithms improve the reliability performance of the communication over the cellular network with or without implementing the RLNC at the source node as summarized in Table 1.
4.2 Reliability Performance of Communication Over Cellular Network With and Without Implement RLNC at the Source Node
The reliability performance of the communication over the cellular network is analyzed with a decoding success probability algorithm. Few parameters have an influence on the reliability performance of the communication over a cellular network. They are the finite field, the erasure probability, the number of relay nodes at cluster 1 and cluster 2, and the coding design parameter. A comparison of the reliability performance of the communication over the cellular network, with and without the implementation of RLNC at the source node is illustrated in Fig. 8a, b respectively. The simulation parameters are shown in Table 2.
The effect of the erasure probability of the link between the source node and the relay nodes at cluster 1, d0, on decoding success probability of a cellular communication network, with and without the implementation of RLNC at source node when M = 4 is simulated and tabulated in Table 3.
The decoding success probability of communication over the cellular network without implementing RLNC at the source node is significantly degraded by the erasure probability in the link between the source node and the relay nodes at cluster 1 as shown in Fig. 8a. Notice that the decoding success probability will no longer increase as the M > 4. In addition, the decoding success probability is too low (only 2%) at high interference condition, d0 = 0.7. The result shows that the cellular communication network is not reliable at a high interference condition (disaster area). However, the reliability performance of a cellular communication network improved when implementing the RLNC at the source node into a cellular communication network as shown in Fig. 8b. The decoding success probability of cellular communication with the implementation of RLNC at the source node increases up to approximately 82% at a high interference condition d0 = 0.7 as shown in Table 3. This shows that the combination of the link diversity packet created by the source node and the multi-relay at cluster 1 and cluster 2 is enough to reduce the packet loss. Next, the effect of the number of the relay at cluster 2, M, on data exchange reliability between a source and a destination node in the cellular network was analyzed and tabulated in Table 4.
As shown in Fig. 8a, b, the grey (M = 4), white (M = 3) and black color (M = 2) of the surface area corresponding to a different number of relay nodes at cluster 2. The communication over the cellular network is not reliable when the M = 2. This is because the number of relay nodes at cluster 2 is less than the number of relay nodes at cluster 1 (N = 3). The decoding success probability increases as the number of relay nodes at cluster 2 increases. The decoding success probability of cellular communication network with the implementation of RLNC at the source node gives better performance compared to a network without the RLNC at the source node. Implementation of RLNC at source node into the cellular communication network improves almost 52% and 80% of decoding success probability for M = 3 and M = 4 respectively. This is because the RLNC algorithm offers more packet diversity and much more resilient to packet loss. In addition, implementing the RLNC at the source node reduced the number of a transmitted packet at the source node.
Furthermore, the effect of the number of coded packets generated at the source node, m, on decoding success probability of the cellular communication network in the conditions of M = 3, n = 3, N = 3, q = 256, d0 = 0.7 and d1 = d2 = 0.01 is shown in Fig. 9. The decoding success probability increases as the coded packet generated increases. Thus, the reliability performance of the cellular communication network can be much more stable by adaptably changing the number of coded packets generated at the source node which provides diverse packet. The result shows that the reliable data exchange between the source and the destination can be improved by adjusting the number of coded data packets generated at the source at without being affected by the relay nodes condition. This is because the effectiveness of reliability performance of the cellular communication network depending on the availability of at least n linearly independent coded packet at the source node.
The effect of the finite field size on the decoding success probability for the condition of n = 3, m = 4, N = 3 and M = 3 are illustrated in Fig. 10. The simulation parameters are shown in Table 5.
From Fig. 10, notice that the decoding success probability increases as the finite field size increased. The decoding success probability increased from 67 to 89% (approximately 22% improvement) on d0 = d1 = d2 = 0.15 condition. This is because as the finite field size increases, the number of packet transmissions needed decreases and the number of linearly independent coded packet received at the destination node increases. Thus, a larger finite field size value provides better reliability performance of a cellular communication network.
5 Conclusion
This paper evaluated the efficiency of communication over a cellular network with the implementation of RLNC at the source node before the transmission. From the analysis of decoding failure probability, it was found that the new bounds on decoding failure probability algorithm had higher accuracy estimation compared to the proposed bounds algorithm in various condition. The reliability performance of a communication over a cellular network at a disaster area is poor due to the intermittent connectivity scenario. Thus, an analytical framework was proposed to enhance the reliability performance of a cellular network in an intermittent connectivity area. A cellular network with RLNC at the source node is proposed to reduce the packet losses. Thus, a decoding success probability algorithm for a receiver of a communication network is developed based on the new upper bound algorithm. The decoding success algorithm can reduce the computational time.
With the implementation of the RLNC at the source node before the transmission, the method can increase the reliability of the communication performance over a cellular network from 2 to 82% under a high noise interference environment, d0 = 0.7, without requiring a large value of relay nodes at cluster 2. This project can be further improved by considering the performance’s delay and coverage area of a communication over a cellular network with RLNC. More network architecture model is recommended to be adopted in a disaster area to further improve the coverage area and the efficiency of a communication network in a disaster area. A joint fountain coding and network coding approach is recommended to improve the throughput of a cellular network in a disaster area.
References
Nosratinia, A. (2004). Cooperative communication in wireless networks. IEEE Comunications Magazine, 42(10), 74–80.
Ahlswede, R., Cai, N., Yeung, R. W., & Li, S.-Y. (2000). Network information flow. IEEE Transactions on Information Theory, 46(4), 1204–1216.
Ostovari, P., Wu, J., & Khreishah, A. (2014). Network coding techniques for wireless and sensor networks. In The art of wireless sensor networks (pp. 129–162). Berlin, Heidelberg: Springer.
JIn, J.-Q., Ho, T., & Viswanathan, H. (2006). Comparison of network coding and non-network coding schemes for multi-hop wireless networks. In IEEE international symposium of information theory (pp. 197–201).
Halloush, R., Liu, H., Dong, L., Wu, M., & Radha, H. (2017). Hop-by-hop content distribution with network coding in multihop wireless networks. Digital Communications and Networks, 3(1), 47–54.
Apavatjrut, A., Goursaud, C., Jaffres-Runser, K., & Gorce, J.-M. (2012). Impact of intra-flow network coding on relay channel performance: An analytical study. In 2012 IEEE 8th international conference on wireless and mobile computing, networking and communication (WiMob) (pp. 232–239).
Pahlevani, P., HundebØll, M., Pedersen, M. V., Lucani, D., Charaf, H., Fitzek, F. H., et al. (2014). Novel concepts for device to device communication using network coding. IEEE Commuications Magazine, 52(4), 32–39.
Katti, S. R. (2008). Network coded wireless architecture. Massachusetts Institute of Technology.
Trullols Cruces, Ó., Barceló Ordinas, J. M., & Fiore, M. (2011). Exact decoding probability under random linear network coding. IEEE Communications Letters, 15(1), 67–69.
Tassi, A., Chatzigeorgiou, I., & Lucani, D. E. (2016). Analysis and optimization of sparse random linear network coding for reliable multicast services. IEEE Transaction on Communications, 64(1), 285–299.
Chiasserini, C. F., & Casetti, C. (2013). Decoding probability in random linear network coding with packet losses. IEEE Communications Letters, 17(11), 2128–2131.
Başaran, S. T., Kurt, G. K., Uysal, M., & Altunbaş, İ. (2016). A tutorial on network coded cooperation. IEEE Communications Surveys & Tutorials, 18(4), 2970–2990.
Seong, J.-T. (2014). Bounds on decoding failure probability in linear network coding schemes with erasure channels. IEEE Communications Letters, 18(4), 648–651.
Khan, A. S., & Chatzigeorgiou, I. (2016). Improved bounds on the decoding failure probability of network coding over multi-source multi-relay networks. IEEE Communications Letters, 20(10), 2035–2038.
Saxena, P., & Vazquez-Castro, M. A. (2015). Network coded multicast and multi-unicast over satellite. In The seventh international conference on advences in satellite and space communication (SPACOMM) (pp. 40–45).
Blömer, J., Karp, R., & Welzl, E. (1997). The rank of sparse random matrices over finite fields. Random Structures and Algorithms, 10(4), 407–419.
Acknowledgements
The authors appreciate those who contributed to make this research successful. This research is under the support of Center for Research and Innovation (PPI) and Faculty of Engineering, Universiti Malaysia Sabah (UMS) under the Fundamental Research Grant (FRG0453-TK-1/2016).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Farzamnia, A., Zhen, L.H. & Moung, E.G. Efficient Cellular Network with Network Coding in Disaster Area. Wireless Pers Commun 106, 701–718 (2019). https://doi.org/10.1007/s11277-019-06186-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06186-4