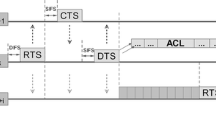
Abstract
Nowadays, the cognitive radio has become a promising solution for spectrum shortage disputes and to achieve dynamic spectrum access. This study focuses on two things: The first aim of this study is the integrity check to be carried when accepting new cognitive users or accept cognitive user who wish to re-join the group. In spite of these checks and after entering the group, some cognitive users turn out to be selfish after accessing the group. Hence the second goal is how to mitigate the attack caused by the selfish malicious user with the help of collaborator node. The collaborator node senses the spectrum and conveys the message along with the authentication tag. The information with the tag is accepted by the cognitive radio.








Similar content being viewed by others
Abbreviations
- PKSM:
-
Spectrum manager public key
- PKCR:
-
Cognitive radio public key
- SKA:
-
Symmetric key between CR and SM
- SK:
-
Symmetric key
- PKGP:
-
Group public key
- PKCR:
-
Cognitive radio public key
- SKB:
-
Symmetric Key between CR and GP
- PID:
-
Physical ID
- LID:
-
Link identifier
- OID:
-
Object identifier
- RN:
-
Random number
References
Force, S. P. T. (2002). Spectrum policy task force report. Federal Communications Commission ET Docket No. 02–135.
Federal Communications Commission (2003). Facilitating opportunities for flexible, efficient and reliable spectrum use employing cognitive radio technologies, notice of proposed rulemaking and order, FCC 03–322.
Liu, Y., Zhong, Z., Wang, G., & Hu, D. (2015). Cyclostationary detection based spectrum sensing for cognitive radio networks. Journal of Communications, 10(1), 74–79.
Vadivelu, R., Sankaranarayanan, K., & Vijaykumar, V. (2014). Matched filter based spectrum sensing for cognitive radio at low signal to noise ratio. Journal of Theoretical and Applied Information Technology, 62(1), 107–113.
Kaur, P., & Singh, C. (2015). Spectrum sensing based on energy detection in cognitive radio. International Journal of Advanced Research in Electronics and Communication Engineering, 4(5), 1214–1217.
Diaconu, A. V., & Loukhaoukha, K. (2013). An Improved secure image encryption algorithm based on Rubik’s cube principle and digital chaotic cipher. Mathematical Problems in Engineering, 2013, 1–10.
Siddaramappa, V., Ramesh, K. B. (2015). Cryptography and bioinformatics techniques for secure information transmission over insecure channels. In International conference on applied and theoretical computing and communication technology (iCATccT) (pp. 137–139).
Alahmadi, A., Abdelhakim, M., Ren, J., & Li, T. (2014). Defense against primary user emulation attacks in cognitive radio networks using advanced encryption standard. IEEE Transactions on Information Forensics and Security, 9(5), 772–781.
Borle, K. M., Chen, B., Du, W. (2013). A physical layer authentication scheme for countering primary user emulation attack. In IEEE international conference on acoustics, speech and signal processing (pp. 2935–2939).
Chandrashekar, S., Lazos, L. (2010). A primary user authentication system for mobile cognitive radio networks. In 3rd international symposium on applied sciences in biomedical and communication technologies (pp. 1–5).
Chen, R., Park, J. M., & Reed, J. H. (2008). Defense against primary user emulation attacks in cognitive radio networks. IEEE Journal on Selected Areas in Communications, 26(1), 25–37.
Pu, D., & Wyglinski, A. M. (2014). Primary-user emulation detection using database-assisted frequency-domain action recognition. IEEE Transactions on Vehicular Technology, 63(9), 4372–4382.
Jin, Z., Anand, S., Subbalakshmi, K. P. (2009). Detecting primary user emulation attacks in dynamic spectrum access networks. In IEEE international conference on communications (pp. 1–5).
Dang, M., Zhao, Z., Zhang H. (2013). Detection of primary user emulation attacks based on compressive sensing in cognitive radio networks. In International conference on wireless communications & signal processing (pp. 1–5).
Liu, Y., Ning, P., Dai, H. (2010). Authenticating primary users’ signals in cognitive radio networks via integrated cryptographic and wireless link signatures. In IEEE symposium on security and privacy (pp. 286–301).
Alahmadi, A., Abdelhakim, M., Ren, J., Li, T. (2013). Mitigating primary user emulation attacks in cognitive radio networks using advanced encryption standard. In IEEE global communications conference (pp. 3329–3334).
Alom, M. Z., Godder, T. K., Morshed, M. N., Maali, A. (2017). Enhanced spectrum sensing based on energy detection in cognitive radionetwork using adaptive threshold. In International conference on networking, systems and security (NSysS) (pp. 138–143).
Eslami, A., Karamzadeh, S. (2016). Memory based energy detection spectrum sensing method in cognitive radio driven hospitals. In Advances in wireless and optical communications (RTUWO) (pp. 111–115).
Zhang, B. Y., Gong, G. (2013). Randomness properties of stream ciphers for wireless communications. In The sixth international workshop on signal design and its application in communications (pp. 107–109).
Guo, Q., & Wang, G. (2010). Generation of a chaos-based PN sequence and its quality analysis. International Conference on Communications, Circuits and Systems, 2010, 756–759.
Rukhin, A., Soto, J., Nechvatal, J., Smid, M., Barker, E., Stefan, L., et al. (2010). A statistical test suite for random and pseudorandom number generators for cryptographic applications. Special Publication (pp. 800–22), Revision 1a: 1-131.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Jayapalan, A., Savarinathan, P., Praveenkumar, P. et al. Detecting and Mitigating Selfish Primary Users in Cognitive Radio. Wireless Pers Commun 109, 1021–1031 (2019). https://doi.org/10.1007/s11277-019-06602-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06602-9