Abstract
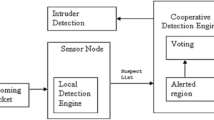
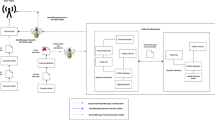
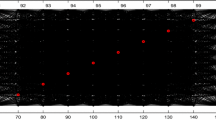
In wireless sensor networks identifying the optimal path is a complex task, it requires some effective routing schemes to handle the issues in networks. To provide such environment for carrying effective routing for data forwarding is nightmare for the traditional methods. In this paper, we propose a bio inspired based secure routing scheme with the help of bee algorithms. The proposed routing mechanism consists of two important metrics known as primary scout bee and secondary scout bee for carrying routing and security mechanism. It provides better data efficiency with security in many scenarios. Here we use three kinds of routing attacks, to evaluate the proposed scheme such as flood attack, spoof attack and Sybil attack. The final verdict of adopting this technique is to derive a secure routing path for carrying the message in WSN environment. The simulation result shows that, the proposed Beeware routing scheme provides a better result compared to other mechanism.







Similar content being viewed by others
References
Giagkos, A., & Wilson, M. S. (2014). BeeIP–A swarm intelligence based routing for wireless ad hoc networks. Information Sciences,265, 23–35.
Bok, K., et al. (2016). An energy-efficient secure scheme in wireless sensor networks. Journal of Sensors,2016, 1–11.
Latha, D., & Palanivel, K. (2014). Secure routing in wireless sensor networks through the identified trusted node. International Journal of Advanced Research in Computer Engineering and Technology (IJARCET),3(11), 1–5.
Zhang, M., et al. (2015). B-iTRS: A bio-inspired trusted routing scheme for wireless sensor networks. Journal of Sensors. https://doi.org/10.1155/2015/156843.
Kannadhasan, S., Suresh, P., & Rajesh Baba, M. (2013). Encryption and decryption technique in wireless sensor networks. International Journal of Advanced Research in Computer Science, 4(4).
Chakravarthy, V. D., Sivarajan, S., & Gayathiri, N. (2014). Artificial bee colony (ABC) algorithm with ECDH algorithm for finding optimal path and secure data transfer. International Journal of Scientific and Engineering Research,5(3).
Bitam, S., Zeadally, S., & Mellouk, A. (2016). Bio-inspired cybersecurity for wireless sensor networks. IEEE Communications Magazine,54(6), 68–74.
Toppo, M. K., & Sundarraj, M. B. (2015). Implementation of bio inspired algorithm in identification of best route via ant colony optimization, energy level and throughput with encryption. International Journal on Recent and Innovation Trends in Computing and Communication,3, 1709–1712.
Abro, A. G., & Mohamad-Saleh, J. (2012). Intelligent scout-bee based artificial bee colony optimization algorithm. In 2012 IEEE international conference on control system, computing and engineering (ICCSCE). IEEE.
Greggers, U., et al. (2013). Scouts behave as streakers in honeybee swarms. Naturwissenschaften,100(8), 805–809.
Jadidoleslamy, H. (2014). A comprehensive comparison of attacks in wireless sensor networks. International Journal of Computer Communications and Networks, 4(1).
Rajaram, S., Babu Karuppiah, A., & Vinoth Kumar, K. (2014). Secure routing path using trust values for wireless sensor networks. arXiv preprint arXiv:1407.1972.
Arfat, Y., & Shaikh, R. A. (2016). A survey on secure routing protocols in wireless sensor networks. International Journal of Wireless and Microwave Technologies (IJWMT),6, 9–19.
Karlof, C., & Wagner, D. (2003). Secure routing in wireless sensor networks: Attacks and countermeasures. Ad Hoc Networks,1(2), 293–315.
Tang, D., et al. (2015). Cost-aware secure routing (CASER) protocol design for wireless sensor networks. IEEE Transactions on Parallel and Distributed Systems,26(4), 960–973.
Alrajeh, N. A., Alabed, M. S., & Elwahiby, M. S. (2013). Secure ant-based routing protocol for wireless sensor network. International Journal of Distributed Sensor Networks,9(6), 326295.
Mohammadi, S., Atani, R. E., & Jadidoleslamy, H. (2011). A comparison of routing attacks on wireless sensor networks. Organization,4, 21.
Latha, D., & Palanivel, K. (2014). Secure routing through trusted nodes in wireless sensor networks—A survey. International Journal of Advanced Research in Computer Engineering and Technology (IJARCET),3, 8.
Tripathi, A., et al. (2016). Guaranteed data delivery with ACO, ABC and AODV for wireless sensor networks. International Journal of Computer Technology and Applications,9(20), 213–219.
Saleem, K., & Fisal, N. (2008). A bio-inspired secure routing protocol for WSNs. In Proceedings of 2008 student conference on research and development (SCOReD 2008).
Bouldin, J., & Meghanathan, N. (2010). Rank-based data gathering in wireless sensor networks. International Journal of Research and Reviews in Applied Sciences,5(2), 159–163.
Gao, C., et al. (2014). A bio-inspired algorithm for route selection in wireless sensor networks. IEEE Communications Letters,18(11), 2019–2022.
Saleem, K., Fisal, N., & Hafizah, S. (2011). BIOSARP: Biological inspired self-organized secure autonomous routing protocol for wireless sensor network. In Proceedings of the 11th WSEAS international conference on applied computer science. World Scientific and Engineering Academy and Society (WSEAS).
Dressler, F., & Akan, O. B. (2010). A survey on bio-inspired networking. Computer Networks,54(6), 881–900.
Kolias, C., Kambourakis, G., & Maragoudakis, M. (2011). Swarm intelligence in intrusion detection: A survey. Computers and Security,30(8), 625–642.
Liu, D., Ning, P., & Du, W. (2005). Detecting malicious beacon nodes for secure location discovery in wireless sensor networks. In 25th IEEE international conference on distributed computing systems, 2005. ICDCS 2005. Proceedings. IEEE.
Sahoo, R. R., et al. (2013). A light weight trust based secure and energy efficient clustering in wireless sensor network: Honey bee mating intelligence approach. Procedia Technology,10, 515–523.
Saleem, M., Di Caro, G. A., & Farooq, M. (2011). Swarm intelligence based routing protocol for wireless sensor networks: Survey and future directions. Information Sciences,181(20), 4597–4624.
Dyer, A. G., et al. (2014). Bee reverse-learning behavior and intra-colony differences: Simulations based on behavioral experiments reveal benefits of diversity. Ecological Modelling,277, 119–131.
Suresh, D., & Selvakumar, K. (2014). Improving network lifetime and reducing energy consumption in wireless sensor networks. International Journal of Computer Science and Information Technologies,5(2), 1035–1103.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that there is no conflict of interests regarding the publication of this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Raghav, R.S., Thirugnansambandam, K. & Anguraj, D.K. Beeware Routing Scheme for Detecting Network Layer Attacks in Wireless Sensor Networks. Wireless Pers Commun 112, 2439–2459 (2020). https://doi.org/10.1007/s11277-020-07158-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07158-9