Abstract
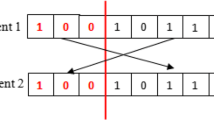
Due to the increasing demand for IoMT applications in numerous fields such as healthcare, smart city, smart grids, industrial internet, etc. The privacy and security become a major issue in front of various researchers working in this field. This work proposed a lightweight image encryption algorithm based on a logistic-tent map and crossover operator of a genetic algorithm. Various 1-D chaotic maps are discussed in the literature review, but in some cases, hybrid 1-D chaotic maps have higher performance than simple 1-D chaotic maps. So 1-D chaotic map along with a crossover operator is used in this work. Here logistic-tent map and crossover are used to generate the random session key for each image encryption. Also, a crossover operator is used in encryption rounds for increasing confusion and diffusion. Here in this work, for each image encryption, a new intelligent session key is generated. The strength of the proposed image cryptographic scheme is assessed against resistance to the differential attack (UACI and NPCR), statistical attack (histogram analysis, correlation coefficient and information entropy) and sensitivity to the secret key. The extensive experiments of performance and security assessment show that the proposed cryptographic image scheme is secure enough to withstand all potential cryptanalytic attacks.












Similar content being viewed by others
Availability of supporting data
The data will be provided based on data request by the evaluation team.
References
Elhoseny, M., Ramírez-González, G., Abu-Elnasr, O. M., et al. (2018). Secure medical data transmission model for IoT-based healthcare systems. IEEE Access, 6, 20596–20608. https://doi.org/10.1109/ACCESS.2018.2817615
Elhoseny, M., Shankar, K., Lakshmanaprabu, S. K., et al. (2020). Hybrid optimization with cryptography encryption for medical image security in Internet of Things. Neural Computing and Applications, 32, 10979–10993. https://doi.org/10.1007/s00521-018-3801-x
Tankard, C. (2015). The security issues of the Internet of Things. Comput Fraud Secur, 2015, 11–14. https://doi.org/10.1016/S1361-3723(15)30084-1
Hameed, S., Khan, F. I., & Hameed, B. (2019). Understanding Security Requirements and Challenges in Internet of Things (IoT): A Review. J Comput Networks Commun. https://doi.org/10.1155/2019/9629381
Liu, B., Li, Y., Zeng, B., & Lei, C. (2016). An efficient trust negotiation strategy towards the resource-limited mobile commerce environment. Frontiers of Computer Science, 10(3), 543–558.
Shen, J., Wang, C., Li, T., Chen, X., Huang, X., & Zhan, Z. H. (2018). Secure data uploading scheme for a smart home system. Information Sciences, 453, 186–197.
Xiong J, Ren J, Chen L, Yao Z, Lin M, Wu D, Niu B. Enhancing privacy and availability for data clustering in intelligent electrical service of IoT. IEEE Internet of Things Journal, 2018
Wu, D., Si, S., Wu, S., & Wang, R. (2018). Dynamic trust relationships aware data privacy protection in mobile crowd-sensing. IEEE Internet of Things Journal, 5(4), 2958–2970.
Peng, S., Yang, A., Cao, L., Yu, S., & Xie, D. (2017). Social influence modeling using information theory in mobile social networks. Information Sciences, 379, 146–159.
Cai, Z., Yan, H., Li, P., Huang, Z. A., & Gao, C. (2017). Towards secure and flexible EHR sharing in mobile health cloud under static assumptions. Cluster Computing, 20(3), 2415–2422.
Wang, H., Zheng, Z., Wu, L., & Li, P. (2017). New directly revocable attribute-based encryption scheme and its application in cloud storage environment. Cluster Computing, 20(3), 2385–2392.
Roy, S., Rawat, U., Sareen, H. A., & Nayak, S. K. (2020). IECA: an efficient IoT friendly image encryption technique using programmable cellular automata. Journal of Ambient Intelligence and Humanized Computing. https://doi.org/10.1007/s12652-020-01813-6
Dagadu, J. C., Li, J., & Aboagye, E. (2019). Medical Image Encryption Based on Hybrid Chaotic DNA Diffusion. Wireless Personal Communications. https://doi.org/10.1007/s11277-019-06420-z
Zhang, W., Zhu, Z., & Yu, H. (2019). A symmetric image encryption algorithm based on a coupled logistic-bernoulli map and cellular automata diffusion strategy. Entropy, 21, 504.
Yicong Z., Long B., C.L. Philip C., (2014). A new 1D chaotic system for image encryption, Signal Processing, 97, 172–182, ISSN 0165–1684, https://doi.org/10.1016/j.sigpro.2013.10.034.
Wang, X., Feng, L., Li, R., Zhang, F.: A fast image encryptionalgorithm based on non-adjacent dynamically coupled map latticemodel. Nonlinear Dyn. 1–28, (2019)
Tang, J., Yu, Z., Liu, L. (2019). A delay coupling method to reduce thedynamical degradation of digital chaotic maps and its applicationfor image encryption. Multimedia Tools Applications 1–24.
Talhaoui, M. Z., Wang, X., & Midoun, M. A. (2020). Fast image encryption algorithm with high security level using the Bülban chaotic map. Journal of Real-Time Image Processing. https://doi.org/10.1007/s11554-020-00948-1
Liu, Y., Zhang, J., Han, D., Wu, P., Sun, Y., & Moon, Y. S. (2020). A multidimensional chaotic image encryptionalgorithm based on the region of interest. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-020-08645-8
You, L., Yang, E., & Wang, G. (2020). A novel parallel image encryption algorithm based on hybrid chaoticmaps with OpenCL implementation. Soft Computing. https://doi.org/10.1007/s00500-020-04683-4
Li, R.: Fingerprint-related chaotic image encryption scheme based on blockchain framework. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-020-08802-z.
Liu, H., Zhao, B., & Huang, L. (2019). A novel quantum image encryption algorithm based on crossover operation and mutation operation. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-019-7186-3
Anderson, R., Biham, E., Knudsen, L. (2019). Serpent: A Proposal for the Advanced Encryption Standard. In Proceedings of the First Advanced Encryption Standard (AES) Conference, Ventura, CA, USA, 20–22, August 1998.
Ren, W.; Miao, Z. (2010). A Hybrid Encryption Algorithm Based on DES and RSA in Bluetooth Communication. In Proceedings of the 2010 Second International Conference on Modeling, Simulation and Visualization Methods, Sanya, China, 15–16; pp. 221–225.
De Dormale, G.M., Bass, J., Quisquater, J.-J. (2007). On solving RC5 challenges with FPGAs. In Proceedings of the 15th Annual IEEE symposium on field-programmable custom computing machines (FCCM 2007), Napa, CA, USA, 23–25, pp. 281–282.
Schneier, B. (1990). The IDEA Encryption Algorithm. Dr. Dobb’s J., 18, 50–56.
Burwick, C., Coppersmith, D., D’Avignon, E., Gennaro, R., Halevi, S., Jutla, C., Matyas, S.M., O’Connor, L., Peyravian, M., Safford, D., et al. (1998). MARS—A candidate cipher for AES.
Coppersmith, D., Johnson, D. B., & Matyas, S. M. (1996). A proposed mode for triple-DES encryption. IBM Journal of Research and Development, 40, 253–262.
Milad, A. A., Muda, H. Z., Noh, Z. A., & Algaet, M. A. (2012). Comparative study of performance in cryptography algorithms (Blowfish and Skipjack). Journal of Computer Science, 8, 1191–1197.
Asassfeh, M. R., Qatawneh, M., & Alazzeh, F. (2018). Performance evaluation of blowfish algorithm on supercomputer IMAN1. International Journal of Computer Networks and Communications, 10(2), 43–53.
Funding
This Research Received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Author information
Authors and Affiliations
Contributions
This work proposed a lightweight image encryption algorithm based on a logistic-tent map and crossover operator of a genetic algorithm.
Corresponding author
Ethics declarations
Conflict of interest
The authors of this research article declares that no conflict of interest in preparing this research article.
Consent for Publication
All the authors of this paper have shown their Participation voluntarily.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Gupta, M., Gupta, K.K., Khosravi, M.R. et al. An Intelligent Session Key-Based Hybrid Lightweight Image Encryption Algorithm Using Logistic-Tent Map and Crossover Operator for Internet of Multimedia Things. Wireless Pers Commun 121, 1857–1878 (2021). https://doi.org/10.1007/s11277-021-08742-3
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-08742-3