Abstract
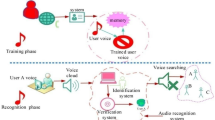
In a multi-sever scenario, a two-party remote user authentication scheme is faced with various kinds of security threats. The introduction of biometric technology can effectively improve the security on the user side and the resistance to password guessing attack. Therefore, many biometrics-based user authentication schemes have emerged in the last few years. However, in some recent authentication schemes, a server can easily impersonate a legal user by using the shared secret key and a randomly selected identity. In this study, we first analyze a study of these schemes and indicate the security weakness and vulnerability that might allow attacks. Then, we present an improved biometrics-based three-factor authentication scheme for multi-server environments that inherits most of the advantages of the original scheme and introduces digital signature to address the common security problem. Furthermore, the proposed scheme also has a simplified the authentication procedure and improves execution efficiency. Analysis results, including security analysis and performance comparison, indicate that the new scheme has good efficiency and is robust against various known attacks.


Similar content being viewed by others
Availability of data and material
All data generated or analysed during this study are included in this published article (and its supplementary information files).
References
Lamport, L. (1981). Password authentication with insecure communication. Communications of the Acm, 24(24), 770–772.
Tsai, J. L., & Lo, N. W. (2013). A new password-based multi-server authentication scheme robust to password guessing attacks. Wireless Personal Communications, 71(3), 1977–1988.
Nam, J., Choo, K. K., Han, S., Paik, J., & Won, D. (2015). Two-round password-only authenticated key exchange in the three-party setting. Symmetry, 7(1), 105–124.
Chang, C. C., & Wu, T. C. (1991). Remote password authentication with smart cards. IEE Proceedings-E, 138(3), 165–168.
Xiong, L., Niu, J., Kumari, S., Islam, S. H., Fan, W., Khan, M. K., & Das, A. K. (2016). A novel chaotic maps-based user authentication and key agreement protocol for multi-server environment with provable security. Wireless Personal Communications, 89(2), 569–597.
Jangirala, S., Mukhopadhyay, S., & Das, A. K. (2017). A multi-server environment with secure and efficient remote user authentication scheme based on dynamic id using smart cards. Wireless Personal Communications, 95(3), 1–33.
Mishra, D. (2016). Design and analysis of a provably secure multi-server authentication scheme. Wireless Personal Communications, 86(3), 1–25.
Mishra, D., & Dhal, S. (2017). Privacy preserving password-based multi-server authenticated key agreement protocol using smart card. Wireless Personal Communications, 99(3), 1–21.
Jiang, Q., Ma, J., Lu, X., & Tian, Y. (2015). An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-Peer Networking and Applications, 8(6), 1070–1081.
Wang, D., He, D., Wang, P., & Chu, C. H. (2015). Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. Dependable & Secure Computing IEEE Transactions on, 12(4), 428–442.
Maitra, T., Islam, S. H., Amin, R., Giri, D., Khan, M. K., & Kumar, N. (2016). An enhanced multi-server authentication protocol using password and smart-card: Cryptanalysis and design. Security & Communication Networks, 9(17), 4615–4638.
Maitra, T., Obaidat, M. S., Amin, R., Islam, S. H., Chaudhry, S. A., & Giri, D. (2016). A robust elgamal-based password-authentication protocol using smart card for client-server communication. International Journal of Communication Systems, 30(11), e3242.1-e3242.12.
Wang, C., Ding, W., Xu, G., & Guo, Y. (2017). A lightweight password-based authentication protocol using smart card. International Journal of Communication Systems, 30(11), e3336.
Azrour, M., Farhaoui, Y., & Ouanan, M. (2017). A new secure authentication and key exchange protocol for session initiation protocol using smart card. International Journal of Network Security, 19(6), 870–879.
Messerges, T. S., Dabbish, E. A., & Sloan, R. H. (2002). Examining smart-card security under the threat of power analysis attacks. IEEE Transactions on Computers, 51(5), 541–552.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver environment. IEEE Systems Journal, 9(3), 816–823.
Li, C. T., & Hwang, M. S. (2010). An efficient biometrics-based remote user authentication scheme using smart cards. Journal of Network & Computer Applications, 33(1), 1–5.
Das, A. K. (2011). Analysis and improvement on an efficient biometric-based remote user authentication scheme using smart cards. Iet Information Security, 5(3), 145–151.
Huang, X., Yang, X., Chonka, A., Zhou, J., & Deng, R. H. (2011). A generic framework for three-factor authentication: Preserving security and privacy in distributed systems. IEEE Transactions on Parallel & Distributed Systems, 22(8), 1390–1397.
Fan, W., Xu, L., Kumari, S., & Xiong, L. (2015). A novel and provably secure biometrics-based three-factor remote authentication scheme for mobile client-server networks. Computers & Electrical Engineering, 45(C), 274–285.
Qi, J., Khan, M. K., Xiang, L., Ma, J., & He, D. (2016). A privacy preserving three-factor authentication protocol for e-health clouds. Journal of Supercomputing, 72(10), 3826–3849.
Chuang, M. C., & Chen, M. C. (2014). An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. International Journal of Network Security, 18(5), 997–1000.
Mishra, D., Das, A. K., & Mukhopadhyay, S. (2016). A secure and efficient ecc-based user anonymity-preserving session initiation authentication protocol using smart card. Peer-to-Peer Networking & Applications, 9(1), 171–192.
Moon, J., Choi, Y., Kim, J., & Won, D. (2016). An improvement of robust and efficient biometrics based password authentication scheme for telecare medicine information systems using extended chaotic maps. Journal of Medical Systems, 40(3), 1–11.
S. Ibjaoun, A. A. E. Kalam, V. Poirriez, A. A. Ouahman, & M. D. Montfort, (2017). Analysis and enhancements of an efficient biometric-based remote user authentication scheme using smart cards, in 2016 IEEE/ACS 13th International Conference of Computer Systems and Applications, 1–8.
Mishra, D., Kumari, S., Khan, M. K., & Mukhopadhyay, S. (2017). An anonymous biometric-based remote user-authenticated key agreement scheme for multimedia systems. International Journal of Communication Systems, 30(1), e2946.1-e2946.14.
Park, Y. H., Park, K. S., Lee, K. K., Song, H., & Park, Y. H. (2017). Security analysis and enhancements of an improved multi-factor biometric authentication scheme. International Journal of Distributed Sensor Networks, 13(8), 155014771772430.
Shingala, M., Patel, C., & Doshi, N. (2017). An improve three factor remote user authentication scheme using smart card. Wireless Personal Communications, 99(12), 1–25.
Khan, M. K., & Kumari, S. (2013). An improved biometrics-based remote user authentication scheme with user anonymity. BioMed Research International, 2013(5), 491289.
Wen, F., Susilo, W., & Yang, G. (2015). Analysis and improvement on a biometric-based remote user authentication scheme using smart cards. Wireless Personal Communications, 80(4), 1747–1760.
Xiong, L., Niu, J., Khan, M. K., Liao, J., & Zhao, X. (2014). Robust three-factor remote user authentication scheme with key agreement for multimedia systems. Security & Communication Networks, 9(13), 1916–1927.
He, D., Zeadally, S., Wu, L., & Wang, H. (2016). Analysis of handover authentication protocols for mobile wireless networks using identity-based public key cryptography. Computer Networks, 128(9), 154–163.
Mishra, D., Das, A. K., & Mukhopadhyay, S. (2014). A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Systems with Applications, 41(18), 8129–8143.
Lu, Y., Li, L., Yang, X., & Yang, Y. (2015). A biometrics and smart cards-based authentication scheme for multi-server environment. Security & Communication Networks, 8(17), 3219–3228.
Lu, Y., Li, L., Yang, X., & Yang, Y. (2015). Robust biometrics based authentication and key agreement scheme for multi-server environment using smart cards. Plos One, 10(5), e0126323.
Chaudhry, S. A. (2016). A secure biometric based multi-server authentication scheme for social multimedia networks. Multimedia Tools & Applications, 75(20), 1–21.
Moon, J., Choi, Y., Jung, J., & Won, D. (2015). An improvement of robust biometrics-based authentication and key agreement scheme for multi-server environment using smart cards. Plos One, 10(12), e0145263.
Guo, H., Wang, P., Zhang, X., Huang, Y., & Ma, F. (2017). A robust anonymous biometric-based authenticated key agreement scheme for multi-server environment. Plos One, 12(11), e0187403.
Tomar, A., & Dhar, J. (2019). An ECC based secure authentication and key exchange scheme in multi-server environment. Wireless Personal Communications, 107, 351–372.
Qi, M., & Chen, J. (2019). Anonymous biometrics-based authentication with key agreement scheme for multi-server environment using ECC. Multimedia Tools and Applications, 78(19), 553–568.
Sudhakar, T., & Natarajan, V. (2019). A new three-factor authentication and key agreement protocol for multi-server environment. Wireless Networks, 26(3), 4909–4920.
Chuang, Y., & Lei, C. (2020). An independent three-factor mutual authentication and key agreement scheme with privacy preserving for multiserver environment and a survey. International Journal of Communication Systems, 34, e4660.
Mo, J., Chen, H., & Shen, W. (2020). Cryptanalysis of anonymous three factor-based authentication schemes for multi-server environment. International Conference on Security with Intelligent Computing and Big-data Services, 456–468.
Qi, F., He, D., Zeadally, S., & Wang, H. (2017). Anonymous biometrics-based authentication scheme with key distribution for mobile multi-server environment. Future Generation Computer Systems, 84, 239–251.
Wong, M. K., Hsu, C. L., Le, T. V., Hsieh, M. C., & Lin, T. W. (2020). Three-factor fast authentication scheme with time bound and user anonymity for multi-server e-health systems in 5g-based wireless sensor networks. Sensors, 20(9), 2511.
Kandar, S., Pal, S., & Dhara, B. C. (2021). A biometric based remote user authentication technique using smart card in multi-server environment. Wireless Personal Communications, 120(2), 1–24.
Le, T. V., & Hsu, C. L. (2021). An anonymous key distribution scheme for group healthcare services in 5g-enabled multi-server environment. IEEE Access, 9, 53408–53422.
Iuh, A., Jian, W. A., Yz, A., & Sm, B. (2021). An efficient hash-based authenticated key agreement scheme for multi-server architecture resilient to key compromise impersonation. Digital Communications and Networks, 7(1), 140–150.
Kumar, A., & Om, H. (2017). An improved and secure multi-server authentication scheme based on biometrics and smartcard. Digital Communications and Networks, 4, 27–38.
Kumar, A., & Om, H. (2021). An enhanced and provably secure authentication protocol using chebyshev chaotic maps for multi-server environment. Multimedia Tools and Applications, 80(9), 14163–14189.
Wwa, B., Hha, C., Lxa, C., Qi, L., Rm, D., & Yz, B. (2021). Blockchain-assisted handover authentication for intelligent telehealth in multi-server edge computing environment. Journal of Systems Architecture, 115, 102024.
Wang, D., & Wang, P. (2014). On the anonymity of two-factor authentication schemes for wireless sensor networks: Attacks, principle and solutions. Computer Networks, 73(C), 41–57.
Burrows, M., Abadi, M., & Needham, R. (1990). A logic of authentication. ACM Transactions on Computer Systems, 8(1), 18–36.
M. Abadi B. Blanchet & H.C.L. (2009). Models and proofs of protocol security: A progress report, in a. bouajjani & o. maler (eds.). Computer aided verification, 35–49.
Sklavos N., Koufopavlou O. (2003). On the hardware implementations of the SHA-2 (256, 384, 512) hash functions. Proceedings of the 2003 International Symposium on Circuits and Systems 5.
Buchmann, J. (2004). Introduction to cryptography (2nd ed.). New York: Springer.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflicts of interest
The authors declared that they have no conflicts of interest to this work. We declare that we have no financial and personal relationships with other people or organizations that can inappropriately influence our work, there is no professional or other personal interest of any nature or kind in any product, service and/or company that could be construed as influencing the position presented in, or the review of, the manuscript entitled, “A novel three-factor authentication scheme with high security for multi-server environments”
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Chen, R., Mou, Y. & Zhang, M. A Novel Three-Factor Authentication Scheme with High Security for Multi-Server Environments. Wireless Pers Commun 124, 763–781 (2022). https://doi.org/10.1007/s11277-021-09382-3
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-09382-3