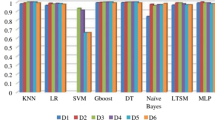
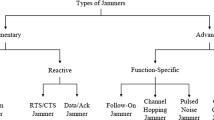
Abstract
Spatial positioning of the sensor nodes in the Wireless Sensor Networks (WSN) promotes remote monitoring of assets or target area in terms of regulating various environmental factors. One of the futuristic characteristic features of WSN is its ability act as autonomous, cooperative yet can be dynamic as well. Data collected from various sensor nodes need to be analysed and processed. Hence, distributed systems could be designed for collection process. Once when the data is collected, it might be aggregated based on the need and has to be sent to the base station. During the process of data transfer, it has to be encrypted. The most challenging task is that ensuring security for the huge data that is being generated with the help of the sensors. While ensuring security, it has to deal with the trade-offs with several other factors such as power consumption, delay, latency and data aggregation paves way for various researches. The idea of the work is to isolate the DoS attacker nodes by deploying a learning model. The proposed deep learning model comprises of few quality metrics of the network as initial nodes and progress the learning. The result shows significant changes while adopting deep learning model to routing, rerouting and data transmission across the network.







Similar content being viewed by others
Data Availability and Materials
The experimental result shows the data availability.
References
Aji, S. M., & McEliece, R. J. (2000). The generalized distributive law. IEEE Transactions on Information Theory, 46(2), 325–343.
Alsheikh, M. A., Lin, S., Niyato, D., & Tan, H. P. (2014). Machine learning in wireless sensor networks: Algorithms, strategies, and applications. IEEE Communications Surveys and Tutorials, 16(4), 1996–2018.
Arulkumaran, K., Deisenroth, M. P., Brundage, M., & Bharath, A. A.: A brief survey of deep reinforcement learning. arXiv:1708.05866, 2017. To appear in IEEE Signal Processing Magazine, Special Issue on Deep Learning for Image Understanding.
Najafabadi, M. M., Villanustre, F., Khoshgoftaar, T. M., Seliya, N., Wald, R., & Muharemagic, E. (2015). Deep learning applications and challenges in big data analytics. Journal of BIG data, 2, 1–21.
Hordri, N. F., Samar, A., Yuhaniz, S. S., & Shamsuddin, S. M. (2017). A systematic literature review on features of deep learning in big data analytics. International Journal of Advances in Soft Computing and its Applications, 9(1), 1–18.
Shui, Yu., Liu, M., Dou, W., Liu, X., & Zhou, S. (2017). Networking for big data: A survey. IEEE Communications Surveys and Tutorials, 19(1), 531–549.
Wang, Y., Wang, X., Agrawal, D., Minai, A. (2006). Impact of heterogeneity on coverage and broadcast reachability in wireless sensor networks. In Proceedings of the 15th international conference on computer communications and networks, Arlington, VA, USA, 9–11 October 2006; pp. 63–67.
Lazos, L., & Poovendran, R. (2006). Stochastic coverage in heterogeneous sensor networks. ACM Transactions on Sensor Networks (TOSN), 2(3), 325–358. https://doi.org/10.1145/1167935.1167937
Tian, D., Georganas, N. D. (2002) A coverage-preserving node scheduling scheme for large wireless sensor networks. In: Proceedings of the 1st ACM International workshop on wireless sensor networks and applications. Atlanta, USA: ACM, pp. 32−41
Zhang, H. H., & Hou, J. C. (2005). Maintaining sensing coverage and connectivity in large sensor networks. Ad-Hoc and Sensor Wireless Networks, 1(1–2), 89–124.
Keshavarzian, A., Lee, H., & Venkatraman, L. (2006). Wakeup scheduling in wireless sensor networks. In: Proceedings of the 7th ACM international symposium on mobile ad hoc networking and computing. Florence, Italy: ACM, pp. 322−333.
Chakrabarty, K., Iyengar, S. S., Qi, H. R., & Cho, E. (2002). Grid coverage for surveillance and target location in distributed sensor networks. IEEE Transactions on Computers, 51(12), 1448–1453.
Deng, J., Han, R., & Mishra, S. (2004). Countermeasures against traffic analysis in wireless sensor networks, Technical Report CU-CS-987-04, University of Colorado at Boulder.
Deng, J., Han, R., & Mishra, S. (2002). INSENS: intrusion-tolerant routing in wireless sensor networks, Technical Report CU-CS-939-02, Department of Computer Science, University of Colorado at Boulder, November 2002. https://arxiv.org/ftp/arxiv/papers/1301/1301.5065.pdf.
Aggarwal, P., & Sharma, S. K. (2015). Analysis of KDD dataset attributes-class wise for intrusion detection. Procedia Computer Science, 57, 842–851.
Jeyanna, J. A., Indumathi, E., & Punithavathani, D. S. (2015). A network intrusion detection system using clustering and outlier detection. International Journal of Innovative Research in Computer and Communication Engineering, 3(2), 975–982.
Roy, S., Maitra, N., Nath, J., Agarwal, S., & Nath, A. (2012).Ultra encryption standard modified (UES) version-I: Symmetric key cryptosystem with multiple encryption and randomized vernam key using generalized modified vernam cipher method, permutation method, and columnar transposition method. In Proc. IEEE Sponsored Nat. Conf. Recent Adv. Commun., Control Comput. Technol. (RACCCT), pp. 29–30.
Swaminathan, A., Krishnan, B. S., & Ramaswamy, M. (2017). A novel security enhancement strategy for improving the concert of CDMA based mobile ad-hocnetwork. In Proc. Int. J. Mod. Electron. Commun. Eng. (IJMECE), Jan. 2017, pp. 1–8.
Kaur, A., & Kang, S. S. (2016). Attacks in wireless sensor network—A review. International Journal of Computational Science and Engineering, 4(5), 157–162.
Shinganjude, R. D. & Theng, D. P. (2014). Inspecting the ways of source anonymity in wireless sensor network. In Proc. 4th Int. Conf. Commun. Syst. Netw. Technol. (CSNT), pp. 705–707.
Lingaraj, K., Biradar, R. V., & Patil, V. C. (2018). Eagilla: An enhanced mobile agent middleware for wireless sensor networks. Alexandria Engineering Journal, 57(3), 1197–1204.
Capra, L. (2007). MaLM: Machine learning middleware to tackle ontology heterogeneity. In Proc. 5th An(PerComWorkshops),WhitePlains,NY,USA, Mar.2007, pp. 449–454.
Avram, T., Oh, S., & Hariri, S. (2007). Analysing attacks in wireless ad hoc network with self-organizing maps. In Proc. 5th Annual .conf. communication. networks. services res. (CNSR), Frederlcton, NB, Canada, May 2007, pp. 166–175.
Alsheikh, M. A., Lin, S., Niyato, D., & Tan, H. P. (2014). Machine learning in wireless sensor networks: Algorithms, strategies, and applications. IEEE Communication. Surveys and Tutorials, 16(4), 1996–2018.
Hodge, V., & Austin, J. (2004). A survey of outlier detection methodologies. Artificial Intelligence Review, 22, 85–126.
Branch, J. W., Szymanski, B., Giannella, C., Wolff, R., & Kargupta, H. (2006). In network outlier detection in wireless sensor networks. InProc.26thIEEE Int. conf. distributed. computing. syst. (ICDCS), Lisboa, Portugal, 2006, p. 51.
Janakiram D., Reddy, V. A., & Kumar, A. V. U. P.: Outlier detection in wireless sensor networks using Bayesian belief networks. In Proc. 1st Int. conf. commun. syst. softw. middleware, New Delhi, India, Jan. 2006, p 16.
Branch, J. W., Giannella, C., Szymanski, B., Wolff, R., & Kargupta, H. (2013). In-network outlier detection in wireless sensor networks. In Proc. 26th IEEE Int. conf. distrib. comput. syst. (ICDCS), Lisboa, Portugal, p 51.
Snow, A., Rastogi, P., & Weckman, G. (2005). Assessing dependability of wireless networks using neural networks. Military Communications Conference IEEE, 5, 2809–2815.
Moustapha, A., & Selmic, R. (2008). Wireless sensor network modeling using modified recurrent neural networks: application to fault detection. IEEE Transactions on Instrumentation and Measurement, 57(5), 981–988.
Chen, Y. S., Qin, Y. S., Xiang, Y. G., Zhong, J. X., & Jiao, X. L. (2011). Intrusion detection system based on immune algorithm and support vector machine in wireless sensor network. In Information and Automation: International Symposium, ser. Communications in Computer and Information Science (pp. 372–376). Springer Berlin Heidelberg.
Kaplantzis, S., Shilton, A., Mani, N., & Sekercioglu, Y. (2017). Detecting selective forwarding attacks in wireless sensor networks using support vector machines. In: 3rd International conference on intelligent sensors, sensor networks and information. IEEE, 2007, pp. 335–340
Zhang, Y., Meratnia, N., & Havinga, P. J. (2013). Distributed online outlier detection in wireless sensor networks using ellipsoidal support vector machine. Ad Hoc Networks, 11(3), 1062–1074.
Steinwart, I., & Christmann, A. (2008). Support vector machines. Cham: Springer.
Sugeng, W., Istiyanto, J. E., Mustofa, K., & Ashari, A. (2015). The impact of QoS changes towards network performance. International Journal of Computer Networks and Communications Security, 3(2), 48–53. https://doi.org/10.1007/978-0-387-77242-4
Saravana Kumar, N. M., Suryaprabha, E., & Hariprasath, K. (2021). Machine learning based hybrid model for energy efficient secured transmission in wireless sensor networks. Journal of Ambient Intelligence and Humanized Computing. https://doi.org/10.1007/s12652-021-02946-y
Funding
Not applicable.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Saravana Kumar, N.M., Suryaprabha, E., Hariprasath, K. et al. Deep Learning Based Hybrid Security Model in Wireless Sensor Network. Wireless Pers Commun 129, 1789–1805 (2023). https://doi.org/10.1007/s11277-023-10208-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10208-7