Abstract
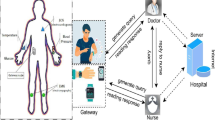
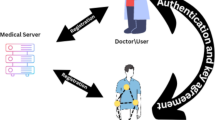
Internet of Medical Things (IoMT) is mainly composed of patients, doctors and medical data collection equipment. In IoMT, the health data of patients is collected in real-time through mobile devices and stored in the network servers for access by legitimate medical personnel to facilitate monitoring, diagnosis and treatment services for patients. To securely transmit various types of data is the essential task of secure group communications for Internet of Things (IoMT). Collected data in IoMT have the particularity of being heterogeneous. At the same time, IoMT networks is exposed to some security threats caused by various attacks, as well as efficiency challenges caused by limited communication range and limited energy. Thus, how to securely group communicate and compute heterogeneous data between resource-constrained IoMT devices is a crucial problem to be solved. Due to the lightweight computational overhead required for group key agreement in resource-constrained environments, traditional protocols are not effectively applied by researchers in the IoMT. Based on symmetric binary polynomial and XOR operation, a lightweight and fast member authentication group key agreement is presented, which can be effectively applied in resource-constrained IoMT. The proposed scheme realizes the functions of membership authentication and group key negotiation, while improving the communication efficiency of group members. In terms of security, our scheme is resistant to both internal and external attacks and can satisfy all the defined security properties. Furthermore, using the logic XOR operation as the main operation method ensures that the computation cost in this protocol is lightweight. More importantly, in our proposal, the communication consumption at each group member end is not affected by the size of group, where the communication method between members is in a non-interactive and broadcast way. In consequence, our protocol provides a more efficient communication and computational process compared to recently proposed cryptographic schemes. Hence, this proposal is an excellent choice for solving membership authentication and group key agreement problems in resource-constrained IoMT systems.



Similar content being viewed by others
Data availability
The data used to support the findings of this study are included within the article. There are no new data associated with this article
References
Tayeh, G. B., Makhoul, A., Demerjian, J., et al. (2020). Fault tolerant data transmission reduction method for wireless sensor networks. World Wide Web, 23, 1197–1216. https://doi.org/10.1007/s11280-019-00767-w
Evans, B. D., Kolesnikov, V., & Rosulek, M. (2018). A pragmatic introduction to secure multi-Party computation. NOW Publishers.
Sadler, C. (2018). Protecting privacy with secure multi-party computation, New America, Blog Post at https://www.newamerica.org/oti/blog/protecting-privacy-secure-multi-party computation/on June 18, 2018.
Song, J., Liu, Y., Shao, J., & Tang, C. (2019). a dynamic membership data aggregation (DMDA) protocol for smart grid. IEEE Systems Journal. https://doi.org/10.1109/JSYST.2019.2912415
Shamir, A. (1979). How to share a secret. Communications of the ACM, 22(11), 612–613.
Goethals, B., Laur, S., Lipmaa, H., & Mielikäinen, T. (2005). On private scalar product computation for privacy-preserving data mining. ICISC
Dagdelen, O., & Venturi, D. (2014). A multiparty protocol for privacy-preserving cooperative linear systems of equations. BalkanCryptSec
Du, W., & Zhan, Z. (2002). A practical approach to solve secure multiparty computation problems. NSPW'02
Jarecki, S. (2018). Efficient covert two-party computation. PKC
Mishra, P. K., Rathee, D., Duong, D. H., & Yasuda, M. (2018). Fast secure matrix mul- tiplications over ring-based homomorphic encryption. IACR Cryptology ePrint Archive, 2018, 663.
Pettai, M., & Laud, P. (2015). Combining differential privacy and secure multiparty computation. in ACSAC
He, X., Machanavajjhala, A., Flynn, C., & Srivastava, D. (2017). Composing differential privacy and secure computation: a case study on scaling private record linkage. Proceedings of the 2017 ACM SIGSAC conference on computer and communications security, pp. 1389–1406
Laih, C. S., Lee, J. Y., & Harn, L. (1989). A new threshold scheme and its application in designing the conference key distribution cryptosystem. Information Processing Letters, 32(3), 95–99.
Wu, S., Hsu, C., Xia, Z., et al. (2020). Symmetric-bivariate-polynomial-based lightweight authenticated group key agreement for industrial internet of things. Journal of Internet Technology, 21(7), 1969–1979.
Jiao, R., Ouyang, H., Lin, Y., Luo, Y., Li, G., Jiang, Z., & Zheng, Q. (2019). A computation-efficient group key distribution protocol based on an secret sharing scheme. Information, 10(5), 175.
Harn, L., Hsu, C., et al. (2015). Novel design of secure end-to-end routing protocol in wireless sensor networks. IEEE Sensors Journal, 16(6), 1779–1785.
Harn, L., & Hsu, C. (2015). Predistribution scheme for establishing group keys in wireless sensor networks. IEEE Sensors Journal, 15(9), 5103–5108.
IEEE 802 LAN/MAN Standards Committee, IEEE 802.11 (2019) The working group setting the standards for wireless LANs, Retrieved 5 (2019).
Cheng, Q., Hsu, C., Xia, Z., & Harn, L. (2020). Fast multivariate-polynomial-based membership authentication and key establishment for secure group communications in WSN. IEEE Access, 8, 71833–71839. https://doi.org/10.1109/ACCESS.2020.2987978
Cheng, Q., Hsu, C., & Harn, L. (2020). Lightweight noninteractive membership authentication and group key establishment for WSNs. Mathematical Problems in Engineering. https://doi.org/10.1155/2020/1452546
Hsu, C., Harn, L., Xia, Z., et al. (2021). Non-interactive integrated membership authentication and group arithmetic computation output for 5G sensor networks[J]. IET Communications, 15(2), 328–336.
Kumar, M., & Chand, S. (2020). A secure and efficient cloud-centric internet-of-medical-things-enabled smart healthcare system with public verifiability. IEEE Internet of Things Journal, 7(10), 10650–10659.
Rakesh Kumar, M., & Velusamy, P. (2020). A secure fuzzy extractor based biometric key authentication scheme for body sensor network in Internet of medical things”. Computer Communications, 153, 545–552.
Ahamad, S. S., & Pathan, Al.-S.K. (2021). A formally verified authentication protocol in secure framework for mobile healthcare during COVID-19-like pandemic. Connection Science, 33(3), 532–554.
Hao, J., Tang, W., Huang, C., Liu, J., Wang, H., & Xian, M. (2022). Secure data sharing with flexible user access privilege update in cloud-assisted IoMT. IEEE Transactions on Emerging Topics in Computing, 10(2), 933–947.
Zhou, Y., Tan, H., Iroshan, K.C.A.A. (2022). A secure and privacy-preserving authentication scheme in IoMT. International symposium on security and privacy in social networks and big data, (vol. 1663, pp. 163-174) Springer
Chor,B., Goldwasser,S., Micali, S., & Awerbuch, B. (10985).Verifiable secret sharing and achieving simultaneity in the presence of faults. Proceedings of the 26th IEEE SFCS, pp. 383–395
Cramer, R., Damgard, I., Dziembowski, S., Hirt,M., & Rabin, T. (1999). Efficient multiparty computations secure against an adaptive adversary. Proceedings of 18th Annual IACR EUROCRYPT, pp. 311–326
Liu, Y., Yang, C., Wang, Y., et al. (2018). Cheating identifiable secret sharing scheme using symmetric bivariate polynomial. Information Sciences, 453, 21–29.
Y. Desmedt and Frankel,Y. (1991) Shared generation of authenticators and signatures. Advances in CRYPTO, pp. 457–569
Katz, J., Koo, C. & Kumaresan R. (2008), Improved the round complexity of VSS in point-to-point networks. Proceedings of ICALP '08, Part II, in: LNCS, (vol. 5126, pp. 499–510), Springer
Kumaresan, R., Patra, A., & Rangan, C. P. (2010). “The round complexity of verifiable secret sharing: The statistical case”, in Advances in Cryptology - ASIACRYPT 2010. LNCS, 6477, 431–447.
Harn, L., & Hsu, C. (2017). A practical hybrid group key establishment for secure group communications. The Computer Journal, 60(11), 1582–1589.
Harn, L., & Hsu, C. (2017). A novel design of membership authentication and group key establishment protocol. Security and Communication Networks. https://doi.org/10.1155/2017/8547876
Hsu, C., et al. (2017). Computation-efficient key establishment in wireless group communications. Wireless Networks, 23(1), 289–297.
Xiong, H., Wu, Y., & Lu, Z. (2019). A survey of group key agreement protocols with constant rounds. ACM Computing Surveys (CSUR), 52(3), 1–32.
Zheng, J., et al. (2018). Cross-cluster asymmetric group key agreement for wireless sensor networks. Science China Information Sciences, 61(4), 048103.
Zhang, Q., et al. (2018). A dynamic and cross-domain authentication asymmetric group key agreement in telemedicine application. IEEE Access, 6, 24064–24074.
Tan, H., & Chung, I. (2018). A secure and efficient group key management protocol with cooperative sensor association in WBANs. Sensors, 18(11), 3930.
Zhang, Q., et al. (2018). An authenticated asymmetric group key agreement based on attribute encryption. Journal of Network and Computer Applications, 123, 1–10.
Knuth, D. E. (1981). The art of computer programming, semi-numerical algorithms (Vol. II). Addison Wesley.
Rivest, R. L., Shamir, A., & Adleman, L. (1978). A method for obtaining digital signatures and public-key cryptosystems. Communications of the ACM, 21(2), 120–126.
Acknowledgements
This work was partially supported by the National Natural Science Foundation of China (Grants Nos. 61772224, 62172181, 62072133), the National Natural Science Foundation of China (Grants Nos. U21A20465, 61922045, U1836115) and the key projects of Guangxi Natural Science Foundation (no. 2018GXNSFDA281040). The data used to support the findings of this study are included within the article.
Funding
The authors have not disclosed any funding.
Author information
Authors and Affiliations
Ethics declarations
Conflict of interest
The authors have not disclosed any competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Hsu, C., Harn, L., Xia, Z. et al. Fast and Lightweight Authenticated Group Key Agreement Realizing Privacy Protection for Resource-Constrained IoMT. Wireless Pers Commun 129, 2403–2417 (2023). https://doi.org/10.1007/s11277-023-10239-0
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10239-0