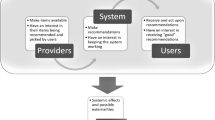
Abstract
Privacy leakage is an important issue for social relationships-based recommender systems (i.e., social recommendation). Existing privacy preserving social recommendation approaches usually allow the recommender to fully control users’ information. This may be problematic since the recommender itself may be untrusted, leading to serious privacy leakage. Besides, building social relationships requires sharing interests as well as other private information, which may lead to more privacy leakage. Although sometimes users are allowed to hide their sensitive private data using personalized privacy settings, the data being shared can still be abused by the adversaries to infer sensitive private information. Supporting social recommendation with least privacy leakage to untrusted recommender and other users (i.e., friends) is an important yet challenging problem. In this paper, we aim to achieve privacy-preserving social recommendation under personalized privacy settings. We propose PrivSR, a novel privacy-preserving social recommendation framework, in which user can model user feedbacks and social relationships privately. Meanwhile, by allocating different noise magnitudes to personalized sensitive and non-sensitive feedbacks, we can protect users’ privacy against untrusted recommender and friends. Theoretical analysis and experimental evaluation on real-world datasets demonstrate that our framework can protect users’ privacy while being able to retain effectiveness of the underlying recommender system.














Similar content being viewed by others
Notes
Facebook provides public pages for products, e.g., https://www.facebook.com/pages/Google-Earth/107745592582048
The idea presented in the extended PrivSR can also be applied to other ranking-based social recommender systems [42] after slight modifications.
References
Bhamidipati, S., Fawaz, N., Kveton, B., Zhang, A.: Priview: Personalized media consumption meets privacy against inference attacks. IEEE Softw. 32(4), 53–59 (2015)
Cao, Y., Yoshikawa, M., Xiao, Y., Xiong, L.: Quantifying differential privacy under temporal correlations. In: 33rd IEEE International Conference on Data Engineering, ICDE 2017. San Diego, CA, USA, April 19-22, 2017, pp. 821–832. https://doi.org/10.1109/ICDE.2017.132 (2017)
Chaudhuri, K., Monteleoni, C., Sarwate, A.D.: Differentially private empirical risk minimization. J. Mach. Learn. Res. 12, 1069–1109 (2011)
Cremonesi, P., Koren, Y., Turrin, R.: Performance of recommender algorithms on top-n recommendation tasks. In: Proceedings of the 2010 ACM Conference on Recommender Systems, RecSys 2010. Barcelona, Spain, September 26-30, 2010, pp. 39–46. https://doi.org/10.1145/1864708.1864721 (2010)
Dwork, C., McSherry, F., Nissim, K., Smith, A.: Calibrating noise to sensitivity in private data analysis. In: Theory of Cryptography Conference, pp. 265–284. Springer (2006)
Dwork, C., Roth, A., et al.: The algorithmic foundations of differential privacy. Found. Trends. Theor. Comput. Sci. 9(3–4), 211–407 (2014)
Eisenberg, B., Sullivan, R.: Why is the sum of independent normal random variables normal? Math. Mag. 81(5), 362–366 (2008)
Fredrikson, M., Lantz, E., Jha, S., Lin, S., Page, D., Ristenpart, T.: Privacy in pharmacogenetics: An end-to-end case study of personalized warfarin dosing. In: Proceedings of the 23rd USENIX Security Symposium, San Diego, CA, USA, August 20-22, 2014., pp. 17–32 (2014)
Fredrikson, M., Jha, S., Ristenpart, T.: Model inversion attacks that exploit confidence information and basic countermeasures. In: ACM Sigsac Conference on Computer and Communications Security, pp. 1322–1333 (2015)
Gross, R., Acquisti, A.: Information revelation and privacy in online social networks. In: Proceedings of the Acm Workshop on Privacy in the Electronic Society, pp. 71–80 (2005)
Hoens, T.R., Blanton, M., Chawla, N.V.: A private and reliable recommendation system for social networks. In: IEEE Second International Conference on Social Computing, pp. 816–825 (2010)
Hua, J., Xia, C., Zhong, S.: Differentially private matrix factorization. In: Proceedings of the Twenty-Fourth International Joint Conference on Artificial Intelligence, IJCAI 2015. Buenos Aires, Argentina, July 25-31, 2015, pp. 1763–1770. http://ijcai.org/Abstract/15/251 (2015)
Jorgensen, Z., Yu, T.: A privacy-preserving framework for personalized, social recommendations. In: International Conference on Extending Database Technology, EDBT (2014)
Kasiviswanathan, S.P., Rudelson, M., Ullman, J.: The price of privately releasing contingency tables and the spectra of random matrices with correlated rows. In: ACM Symposium on Theory of Computing, pp. 775–784 (2010)
Komarova, T., Nekipelov, D., Yakovlev, E.: Estimation of treatment effects from combined data: Identification versus data security. In: Iccas-Sice, pp. 3066–3071 (2013)
Koren, Y.: Factorization meets the neighborhood: A multifaceted collaborative filtering model. In: ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, pp. 426–434 (2008)
Koren, Y.: Collaborative filtering with temporal dynamics. Commun. ACM 53 (4), 89–97 (2010)
Koren, Y., Bell, R.M., Volinsky, C.: Matrix factorization techniques for recommender systems. IEEE Comput. 42(8), 30–37 (2009). https://doi.org/10.1109/MC.2009.263
Kotz, S., Kozubowski, T., Podgorski, K.: The Laplace Distribution and Generalizations: A Revisit with Applications to Communications, Economics, Engineering, and Finance. Springer Science & Business Media (2012)
Krohngrimberghe, A., Drumond, L., Freudenthaler, C., Schmidtthieme, L.: Multi-relational matrix factorization using bayesian personalized ranking for social network data, 173–182 (2012)
Li, Q., Li, J., Wang, H., Ginjala, A.: Semantics-enhanced privacy recommendation for social networking sites. In: IEEE International Conference on Trust, Security and Privacy in Computing and Communications, pp. 226–233 (2011)
Liu, K., Terzi, E.: A framework for computing the privacy scores of users in online social networks. Acm Trans. Knowl. Discov. Data 5(1), 1–30 (2010)
Ma, H., Zhou, D., Liu, C., Lyu, M.R., King, I.: Recommender systems with social regularization. In: Proceedings of the Forth International Conference on Web Search and Web Data Mining, WSDM 2011. Hong Kong, China, February 9-12, 2011, pp. 287–296. https://doi.org/10.1145/1935826.1935877 (2011)
Machanavajjhala, A., Korolova, A., Sarma, A.D.: Personalized social recommendations: Accurate or private. Proc. VLDB Endow. 4(7), 440–450 (2011)
McSherry, F.: Privacy integrated queries: An extensible platform for privacy-preserving data analysis. Commun. ACM 53(9), 89–97 (2010). https://doi.org/10.1145/1810891.1810916
Meng, X., Xu, Z., Chen, B., Zhang, Y.: Privacy-preserving query log sharing based on prior n-word aggregation. In: Trustcom, pp. 722–729 (2016)
Meng, X., Wang, S., Liu, H., Zhang, Y.: Exploiting emotion on reviews for recommender systems. In: AAAI (2018)
Minkus, T., Liu, K., Ross, K.W.: Children seen but not heard: When parents compromise children’s online privacy. In: International Conference on World Wide Web, pp. 776–786 (2015)
Nikolaenko, V., Ioannidis, S., Weinsberg, U., Joye, M., Taft, N., Boneh, D.: Privacy-preserving matrix factorization. In: 2013 ACM SIGSAC Conference on Computer and Communications Security, CCS’13. Berlin, Germany, November 4-8, 2013, pp. 801–812. https://doi.org/10.1145/2508859.2516751 (2013)
Rajkumar, A., Agarwal, S.: A differentially private stochastic gradient descent algorithm for multiparty classification. Jmlr (2012)
Rendle, S., Freudenthaler, C., Gantner, Z., Schmidt-Thieme, L.: BPR: Bayesian personalized ranking from implicit feedback. In: UAI 2009, pp. 452–461 (2009)
Salakhutdinov, R., Mnih, A.: Probabilistic matrix factorization. In: Advances in Neural Information Processing Systems 20, Proceedings of the Twenty-First Annual Conference on Neural Information Processing Systems. Vancouver, British Columbia, Canada, December 3-6, 2007, pp. 1257–1264. http://papers.nips.cc/paper/3208-probabilistic-matrix-factorization (2007)
Shokri, R., Stronati, M., Shmatikov, V.: Membership inference attacks against machine learning models (2016)
Shu, K., Wang, S., Tang, J., Wang, Y., Liu, H.: Crossfire: Cross media joint friend and item recommendations. In: WSDM (2018)
Song, D., Meyer, D.A., Tao, D.: Top-k link recommendation in social networks. In: 2015 IEEE International Conference on Data Mining, ICDM 2015. Atlantic City, NJ, USA, November 14-17, 2015, pp. 389–398. https://doi.org/10.1109/ICDM.2015.136 (2015)
Song, S., Wang, Y., Chaudhuri, K.: Pufferfish privacy mechanisms for correlated data. In: Proceedings of the 2017 ACM International Conference on Management of Data, SIGMOD Conference 2017. Chicago, IL, USA, May 14-19, 2017, pp. 1291–1306. https://doi.org/10.1145/3035918.3064025 (2017)
Tang, J., Hu, X., Liu, H.: Social recommendation: A review. Social Netw. Analys. Mining 3(4), 1113–1133 (2013). https://doi.org/10.1007/s13278-013-0141-9
Tang, Q., Wang, J.: Privacy-preserving friendship-based recommender systems. IEEE Trans. Depend. Secur. Comput. PP(99), 1–1 (2016)
Twitter data analysis: An investor’s perspective. https://techcrunch.com/2009/10/05/twitter-data-analysis-an-investors-perspective-2
Wang, S., Tang, J., Liu, H.: Toward dual roles of users in recommender systems. In: CIKM (2015)
Wang, Y., Si, C., Wu, X.: Regression model fitting under differential privacy and model inversion attack. In: Proceedings of the Twenty-Fourth International Joint Conference on Artificial Intelligence, IJCAI 2015, Buenos Aires, Argentina, July 25-31, 2015, pp. 1003–1009. http://ijcai.org/Abstract/15/146 (2015)
Wang, X., Lu, W., Ester, M., Wang, C., Chen, C.: Social recommendation with strong and weak ties. In: ACM International on Conference on Information and Knowledge Management, pp. 5–14 (2016)
Wang, S., Wang, Y., Tang, J., Shu, K., Ranganath, S., Liu, H.: What your images reveal: Exploiting visual contents for point-of-interest recommendation. In: Proceedings of WWW, pp. 391–400 (2017)
Wang, S., Tang, J., Wang, Y., Liu, H.: Exploring hierarchical structures for recommender systems. IEEE Transactions on Knowledge and Data Engineering (2018)
Xin, Y., Jaakkola, T.: Controlling privacy in recommender systems. In: Advances in Neural Information Processing Systems, pp. 2618–2626 (2014)
Ying, X., Wu, X., Wang, Y.: On linear refinement of differential privacy-preserving query answering. In: Advances in Knowledge Discovery and Data Mining, 17th Pacific-Asia Conference, PAKDD 2013, Gold Coast, Australia, April 14-17, 2013, Proceedings, Part II, pp. 353–364 (2013)
Zhang, J., Zhang, Z., Xiao, X., Yang, Y., Winslett, M.: Functional mechanism: Regression analysis under differential privacy. Proc. Vldb Endow. 5(11), 1364–1375 (2012)
Zhao, T., McAuley, J.J., King, I.: Leveraging social connections to improve personalized ranking for collaborative filtering. In: Proceedings of the 23rd ACM International Conference on Conference on Information and Knowledge Management, CIKM 2014. Shanghai, China, November 3-7, 2014, pp. 261–270 (2014)
Acknowledgments
This work is supported by, or in part by, National Science Foundation of China (61672500, 61572474), and Program of International S&T Cooperation (2016YFE0121500). Suhang Wang and Huan Liu are supported by the National Science Foundation (NSF) under the grant #1614576 and Office of Naval Research (ONR) under the grant N00014-16-1-2257.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
A preliminary version of this article was published in AAAI ’18.
This article belongs to the Topical Collection: Special Issue on Social Computing and Big Data Applications
Guest Editors: Xiaoming Fu, Hong Huang, Gareth Tyson, Lu Zheng, and Gang Wang
Rights and permissions
About this article
Cite this article
Meng, X., Wang, S., Shu, K. et al. Towards privacy preserving social recommendation under personalized privacy settings. World Wide Web 22, 2853–2881 (2019). https://doi.org/10.1007/s11280-018-0620-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11280-018-0620-z