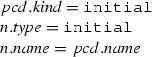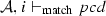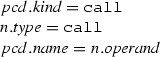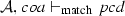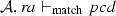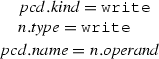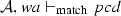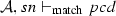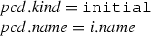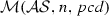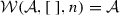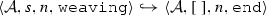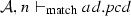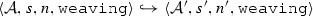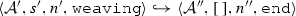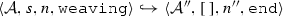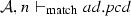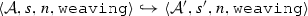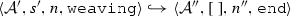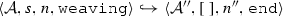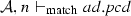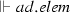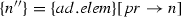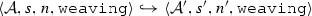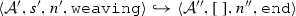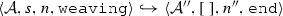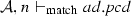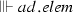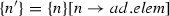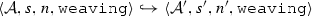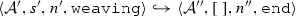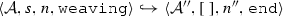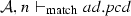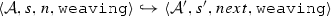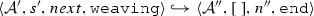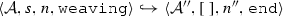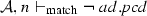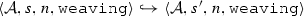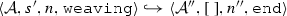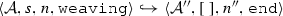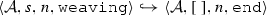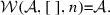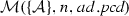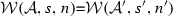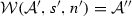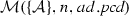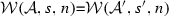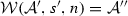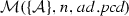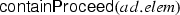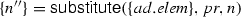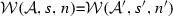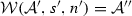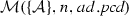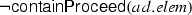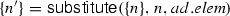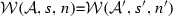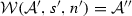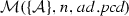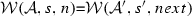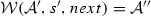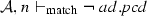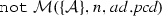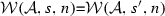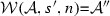Abstract
Aspect-oriented modeling (AOM) emerged as a promising paradigm for handling crosscutting concerns, such as security, at the software modeling level. Most existing AOM contributions are presented from a practical perspective and lack formal syntax and semantics. In this paper, we present a practical and formal AOM framework for software security hardening. Our contributions are threefold. First, we define an AOM approach for the specification of security aspects at the unified modeling language (UML) design level. Second, we design and implement the matching and the weaving processes into UML design models. Third, we elaborate formal specifications for aspect matching and weaving in UML activity diagrams. Finally, we demonstrate the viability and the relevance of our propositions using a case study. The proposed framework is supported by a tool built on top of IBM-Rational Software Modeler.


















Similar content being viewed by others
References
Kiczales G, Lamping J, Menhdhekar A, Maeda C, Lopes C, Loingtier JM, Irwin J (1997) Aspect-oriented programming. In: Proceedings of the European conference on object-oriented programming, vol 1241, pp 220–242. Springer, Berlin
Aspect-oriented modeling workshop (2015) http://www.aspect-modeling.org. Accessed 26 Oct 2015
France RB, Ray I, Georg G, Ghosh S (2004) Aspect-oriented approach to early design modelling. IEE Proc Softw 151(4):173–186
Kienzle J, Al Abed W, Fleurey F, Jézéquel JM, Klein J (2010) Transactions on aspect-oriented software development, chap vii. Aspect-oriented design with reusable aspect models. Springer, Berlin, pp 272–320
Kim D, Whittle J (2005) Generating UML models from domain patterns. ACIS Int Conf Softw Eng Res Manag Appl 166–173
Morin B, Perrouin G, Lahire P, Barais O, Vanwormhoudt G, Jézéquel JM (2009) Weaving variability into domain metamodels. In: Proceedings of the international conference on model driven engineering languages and systems, MODELS ’09. Springer, New York, pp 690–705
Cui Z, Wang L, Li X, Xu D (2009) Modeling and integrating aspects with UML activity diagrams. In: Shin SY, Ossowski S (eds) Proceedings of the symposium on applied computing (SAC). ACM, New York, pp 430–437
Fleurey F, Baudry B, France R, Ghosh S (2007) A generic approach for automatic model composition. In: Proceedings of the workshop on aspect-oriented modeling. Springer, New York, pp 7–15
Fuentes L, Sánchez P (2007) Designing and weaving aspect-oriented executable UML models. J Object Technol 6(7):109–136
Groher I, Voelter M (2007) XWeave: models and aspects in concert. In: Proceedings of the workshop on aspect-oriented modeling. ACM, New York, pp 35–40
Morin B, Klein J, Barais O, Jézéquel J (2008) A generic weaver for supporting product lines. In: Proceedings of the workshop on software architectures and mobility (EA). ACM, New York, pp 11–18
Whittle J, Jayaraman PK, Elkhodary AM, Moreira A, Araújo J (2009) MATA: a unified approach for composing UML aspect models based on graph transformation T. Asp Oriented Softw Dev VI 6:191–237
Zhang J, Cottenier T, Berg A, Gray J (2007) Aspect composition in the Motorola aspect-oriented modeling weaver. J Object Technol (special issue on aspect-oriented modeling) 6(7):89–108
Object Management Group (OMG) (2014) Object constraint language specification, version 2.4. http://www.omg.org/spec/OCL/2.4. Accessed 26 Oct 2015
Object Management Group (OMG) (2015) MOF query/view/transformation, version 1.2. http://www.omg.org/spec/QVT/1.2. Accessed 26 Oct 2015
Medini QVT (2015) http://projects.ikv.de/qvt/. Accessed 26 Oct 2015
Model to model transformation (MMT) (2015) https://wiki.eclipse.org/Model_to_Model_Transformation_-_MMT. Accessed 26 Oct 2015
ModelMorf registration form (2015) http://www.tcs-trddc.com/trddc_website/ModelMorf/ModelMorf.htm. Accessed 26 Oct 2015
SmartQVT (2015) http://sourceforge.net/projects/smartqvt/. Accessed 26 Oct 2015
Software architecture design, visual UML & business process modeling—from Borland (2015) http://www.borland.com/Products/Requirements-Management/Together. Accessed 26 Oct 2015
UMT-QVT homepage (2015) http://umt-qvt.sourceforge.net/. Accessed 26 Oct 2015
Telelogic TAU G2 website (2015) http://www-01.ibm.com/support/docview.wss?uid=swg21380572. Accessed 26 Oct 2015
Kermata—breathe life into your metamodels (2015) http://www.kermeta.org/download. Accessed 26 Oct 2015
Klein J, Fleurey F, Jézéquel JM (2007) Weaving multiple aspects in sequence diagrams T. Asp Oriented Softw Dev 3:167–199
Reddy YR, Ghosh S, France RB, Straw G, Bieman JM, McEachen N, Song E, Georg G (2006) Directives for composing aspect-oriented design class models. Trans Asp Oriented Softw Dev I 3880:75–105
Kompose: a generic model composition tool (2015) http://www.kermeta.org/kompose/. Accessed 26 Oct 2015
Reddy Y, Ghosh S, France R, Straw G, Bieman J, McEachen N, Song E, Georg G (2006) Directives for composing aspect-oriented design class models. In: Rashid A, Aksit M (eds) Transactions on aspect-oriented software development I, vol 3880. Lecture notes in computer science. Springer, Berlin, pp 75–105
Mouheb D, Talhi C, Nouh M, Lima V, Debbabi M, Wang L, Pourzandi M (2010) Aspect-oriented modeling for representing and integrating security concerns in UML. In: Lee RY, Ormandjieva O, Abran A, Constantinides C (eds) Proceedings of the ACIS conference on software engineering research, management, and applications. Studies in computational intelligence, vol 296. Springer, New York, , pp 197–213
Ferraiolo D, Sandhu R, Gavrila S, Kuhn R, Chandramouli R (2001) Proposed NIST standard for role-based access control. ACM Trans Inf Syst Secur 4(3):224–274
Object Management Group (OMG) (2011) Unified modeling language: superstructure, version 2.4.1. http://www.omg.org/spec/UML/2.4.1/Superstructure/PDF. Accessed 26 Oct 2015
Harrop JD (2007) OCaml for scientists. Flying Frog Consulting Ltd, Medford
Object Management Group (OMG) (2011) Unified modeling language: infrastructure, version 2.4.1. http://www.omg.org/spec/UML/2.4.1/Infrastructure/PDF. Accessed 26 Oct 2015
Filman RE, Friedman DP (2000) Aspect-oriented programming is quantification and obliviousness. In: Technical report
Griswold W, Shonle M, Sullivan K, Song Y, Tewari N, Cai Y, Rajan H (2006) Modular software design with crosscutting interfaces. Softw IEEE 23(1):51–60. doi:10.1109/MS.2006.24. Accessed 26 Oct 2015
AspectJ 5 quick reference—eclipse (2015). https://eclipse.org/aspectj/doc/next/quick5.pdf. Accessed 26 Oct 2015
Masuhara H, Kawauchi K (2003) Dataflow pointcut in aspect-oriented programming. In: Ohori A (ed) Proceedings of the first Asian symposium on programming languages and systems (APLAS’03). Lecture notes in computer science, vol 2895. Springer, New York, pp 105–121
Author information
Authors and Affiliations
Corresponding author
Additional information
The research leading to this work is supported by a Collaborative Research and Development (CRD) Grant of the Natural Sciences and Engineering Research Council of Canada (NSERC) in collaboration with Ericsson Canada Inc.
Appendices
Appendix 1: Matching and weaving semantics
In this appendix, we present the matching and the weaving semantics in activity diagrams. The matching semantics describes how to identify the join points targeted by the activity adaptations, whereas the weaving semantics describes how to apply the activity adaptations at the identified join points.
1.1 Matching semantics
We define the judgment \(\mathcal {A}, n \vdash _{\mathrm{match}} { pcd}\), which is used in the matching semantic rules, presented in Fig. 20, to describe that a node n belonging to the activity \(\mathcal {A}\) matches the pointcut pcd. A node n can be an initial node i, an activity final node af, a flow final node ff, a fork node f, a join node j, a decision node d, a merge node m, an action node a, a call operation action node coa, a read structural feature action node ra, a write structural feature action node wa, a create object action node ca, a destroy object action node da, or either of these nodes sn. Before presenting the matching rules, we need to explain the notation of equality of type lists presented in Fig. 19, since it is used in the rule Args. Two lists of types are equal if the nth item in the first list is an instance of the nth item in the second list.
1.2 Weaving semantics
The weaving semantics is represented by the weaving configuration \(\langle \textsf {Activity},\textsf {Aspect},\textsf {Node},\textsf {State}\rangle \) (Fig. 24). The state \(\textsf {State}\) is a flag that represents the stage of the weaving process, which is either weaving or end. The flag is equal to weaving when adaptations still have to be woven, whereas it becomes end when the weaving is completed. Hence, the transformation \({\langle \mathcal {A},s,n,\mathtt{weaving}\rangle \hookrightarrow }\) \({ \langle \mathcal {A'},[~],n',\mathtt{end} \rangle }\) means that the activity diagram \(\mathcal {A'}\) is the result of weaving all the applicable adaptations in the adaptation list s into the node n. A node whose type is proceed is denoted pr, whereas the set {action, call, read, write, create, destroy} is called actionSet. Before presenting the weaving rules, we need to explain the following notation:
-
The axiom \({\Vdash n}\) defines that the node n is of type proceed or it is a structured activity node having, at least, one proceed node. Derivations of proceed nodes are shown in Fig. 21.
-
The axiom \({\Vvdash n}\) defines that the node n is not of type proceed or it is a structured activity node that none of its nodes is of type proceed. Derivations of no proceed nodes are shown in Fig. 22.
-
The representation \(s'=s[n_{1}\rightarrow n_{2}]\) describes that the set \(s'\) comes out as a result of substituting \(n_{1}\) by \(n_{2}\) wherever \(n_{1}\) appears in the set s, as long as the nodes in the set s are not proceed structured activities. This is accompanied by modifying the incoming and the outgoing edges of the node \(n_{2}\) together with modifying the corresponding edges’ sources and targets. In the case that a node in the set s is a proceed structured activity, we substitute \(n_{1}\) by \(n_{2}\) wherever \(n_{1}\) appears in the nodes of this proceed structured activity. The substitution rules are shown in Fig. 23.
Appendix 2: Completeness and correctness of the weaving
We state and prove results that establish the soundness and the completeness of the algorithms containProceed in Fig. 10, substitute in Fig. 11, \(\mathcal {M}\) in Fig. 12, and \(\mathcal {W}\) in Figs. 13 and 14 with respect to the semantics reported in Figs. 21, 23, 20, and 24. The following lemma states the soundness of the algorithm containProceed.
Lemma 1
(Soundness of containProceed). Given a node n. If containProceed then \(\Vdash n\).
The following lemma states the completeness of the algorithm containProceed.
Lemma 2
(Completeness of containProceed). Given a node n. If \(\Vdash n\) then containProceed .
The proofs of Lemmas 1 and 2 are straightforward since the algorithm containProceed results from the rules presented in Fig. 21.
The following lemma states the soundness of the algorithm substitute.
Lemma 3
(Soundness of substitute). Given a set s and two nodes \(n_{1}\) and \(n_{2}\). If \(\textsf {substitute}(s,n_{1},n_{2})=s'\) then \(s'=s[n_{1}\rightarrow n_{2}]\).
The following lemma states the completeness of the algorithm substitute.
Lemma 4
(Completness of substitute). Given a set s and two nodes \(n_{1}\) and \(n_{2}\). If \(s'=s[n_{1}\rightarrow n_{2}]\) then \(\textsf {substitute}(s,n_{1},n_{2})=s'\).
The proofs of Lemmas 3 and 4 are straightforward since the algorithm substitute results from the rules presented in Fig. 23.
The following lemma states the soundness of the matching algorithm \(\mathcal {M}\).
Lemma 5
(Soundness of \(\mathcal {M}\)). Given a set of activity diagrams \(\mathcal {AS}\), an activity node n, and a pointcut pcd. If \(\mathcal {M}(\mathcal {AS},n,{ pcd})\) where \(\mathcal {A}\in \mathcal {AS}\) and \(n\in \mathcal {A}.nodes \) then \(\mathcal {A}, n \vdash _{\mathrm{match}} { pcd}\).
Proof
The proof of Lemma 5 is straightforward by case analysis. Let us take as example the following cases:
-
Case (initial):
From the algorithm \(\mathcal {M}\), we have:
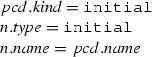
Since \(n.type =\mathtt{initial}\) then n is an initial node i.
By the rule (Initial) of the matching rules presented in Fig. 20, we conclude:
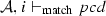
-
Case (call):
From the algorithm \(\mathcal {M}\), we have:
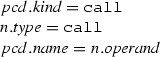
Since \(n.type =\mathtt{call}\) then n is a call operation action node (coa).
By the rule (Call) of the matching rules presented in Fig. 20, we conclude:
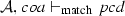
-
Case (read):
From the algorithm \(\mathcal {M}\), we have:
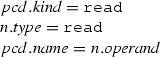
Since \(n.type =\mathtt{read}\) then n is a read structural feature action node (ra).
By the rule (Read) of the matching rules presented in Fig. 20, we conclude:
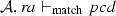
-
Case (write):
From the algorithm \(\mathcal {M}\), we have:
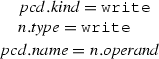
Since \(n.type =\mathtt{write}\) then n is a write structural feature action node (wa).
By the rule (Write) of the matching rules presented in Fig. 20, we conclude:
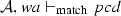
-
Case (inside_activity):
From the algorithm \(\mathcal {M}\), we have:

Since \(n.type =\mathtt{action}\) then n is a simple node (sn).
By the rule (InsideActivity) of the matching rules presented in Fig. 20, we conclude:
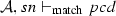
\(\square \)
The following lemma states the completeness of the matching algorithm \(\mathcal {M}\).
Lemma 6
(Completeness of \(\mathcal {M}\)). Given a set of activity diagrams \(\mathcal {AS}\), an activity diagram \(\mathcal {A}\) where \(\mathcal {A}\in \mathcal {AS}\), an activity node n where \(n \in \mathcal {A}.nodes \), and a pointcut pcd. If \(\mathcal {A}, n \vdash _{\mathrm{match}} pcd\) then \(\mathcal {M}(\mathcal {AS},n,pcd)\).
Proof
The proof of Lemma 6 is straightforward by propagating the matching rules, presented in Fig. 20, from conclusion to premises. Let us take as example the following case:
-
Case (initial):
From the rule (Initial), we have:
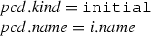
Since n is an initial node i, then \(n.type =\mathtt {initial}\).
Since \(\mathcal {A}\in \mathcal {AS}\) and \(n \in \mathcal {A}.nodes \), by the algorithm \(\mathcal {M}\) presented in Fig. 12, we conclude:
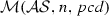
\(\square \)
The following theorem states the soundness of the weaving algorithm \(\mathcal {W}\).
Theorem 1
(Soundness of \(\mathcal {W}\)). Given an activity diagram \(\mathcal {A}\), an adaptation list s, and a node n. If \(\mathcal {W}(\mathcal {A},s,n)\)=\(\mathcal {A''}\) then \(\langle \mathcal {A},s, n,\mathtt{weaving} \rangle \hookrightarrow \langle \mathcal {A}'',[~],n'',\mathtt{end}\rangle \).
Proof
The proof is done by induction over the length of s.
-
1.
Induction basis (\(s=[~]\)):
By the algorithm \(\mathcal {W}\), we have:
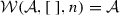
From the algorithm \(\mathcal {W}\), we conclude that \(s=[~]\). From the rule (End) of the semantic weaving rules presented in Fig. 24, we conclude:
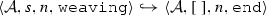
-
2.
Induction step:
We assume as induction hypothesis:
If \(\mathcal {W}(\mathcal {A},s',n)\)=\(\mathcal {A''}\) then \(\langle \mathcal {A},s', n, \mathtt{weaving} \rangle \hookrightarrow \langle \mathcal {A}'',[~],n'',\mathtt{end}\rangle \).
Now, let us consider (\(s=ad::s'\)). Since \(ad.kind \) can be:
-
Case (add):
Since \(ad.pos \) can be:
-
Subcase (before):
From the algorithm \(\mathcal {W}\), we have:

By the soundness of the algorithm \(\mathcal {M}\), we conclude:
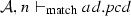
From the rule (Before) of the semantic weaving rules presented in Fig. 24, we conclude:
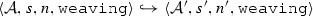
By the hypothesis, we conclude:
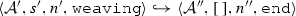
By the transitivity of \(\hookrightarrow \), we conclude:
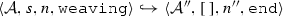
-
Subcase (after):
From the algorithm \(\mathcal {W}\), we have:

By the soundness of the algorithm \(\mathcal {M}\), we conclude:
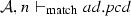
From the rule (After) of the semantic weaving rules presented in Fig. 24, we conclude:
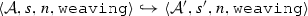
By the hypothesis, we conclude:
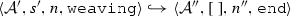
By the transitivity of \(\hookrightarrow \), we conclude:
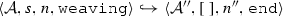
-
Subcase (around with proceed):
From the algorithm \(\mathcal {W}\), we have:

By the soundness of the algorithm \(\mathcal {M}\), we conclude:
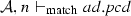
By the soundness of the algorithm containProceed, we conclude:
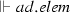
By the soundness of the algorithm substitute, we conclude:
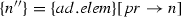
From the rule (\({\small \mathsf{AroundWProceed}}\)) of the semantic weaving rules presented in Fig. 24, we conclude:
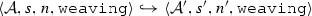
By the hypothesis, we conclude:
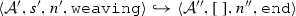
By the transitivity of \(\hookrightarrow \), we conclude:
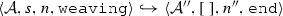
-
Subcase (around without proceed):
From the algorithm \(\mathcal {W}\), we have:

By the soundness of the algorithm \(\mathcal {M}\), we conclude:
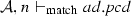
By the soundness of the algorithm containProceed and the rules presented in Figs. 21 and 22, we conclude:
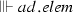
By the soundness of the algorithm substitute, we conclude:
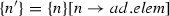
From the rule (\({\small \mathsf{AroundWoutProceed}}\)) of the semantic weaving rules presented in Fig. 24, we conclude:
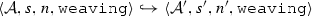
By the hypothesis, we conclude:
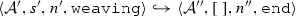
By the transitivity of \(\hookrightarrow \), we conclude:
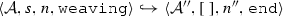
-
-
Case (remove):
From the algorithm \(\mathcal {W}\), we have:

By the soundness of the algorithm \(\mathcal {M}\), we conclude:
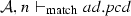
From the rule (Remove) of the semantic weaving rules presented in Fig. 24, we conclude:
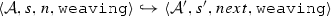
By the hypothesis, we conclude:
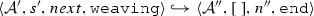
By the transitivity of \(\hookrightarrow \), we conclude:
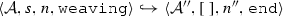
-
Case (no match):
By the soundness and the completeness of the algorithm \(\mathcal {M}\), we conclude:
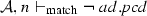
From the rule (NoMatch) of the semantic weaving rules presented in Fig. 24, we conclude:
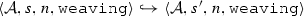
By the hypothesis, we conclude:
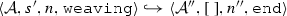
By the transitivity of \(\hookrightarrow \), we conclude:
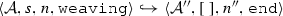
-
\(\square \)
The following theorem states the completeness of the weaving algorithm \(\mathcal {W}\).
Theorem 2
(Completeness of \(\mathcal {W}\)). Given an activity diagram \(\mathcal {A}\), an adaptation list s, and a node n.
If \(\langle \mathcal {A},s, n,\mathtt{weaving} \rangle \hookrightarrow \langle \mathcal {A}'',[~],n'',\mathtt{end}\rangle \) then \(\mathcal {W}(\mathcal {A},s,n)\)=\(\mathcal {A''}\).
Proof
The proof is done by induction over the length of s.
-
1.
Induction basis (\(s=[~]\)):
By the rule (End) of the semantic weaving rules presented in Fig. 24, we have:
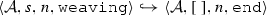
From the rule (End) of the semantic weaving rules presented in Fig. 24, we conclude that \(s=[~]\).
From the algorithm \(\mathcal {W}\), we conclude:
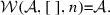
-
2.
Induction step:
We assume as induction hypothesis:
If \(\langle \mathcal {A},s', n,\mathtt{weaving} \rangle \hookrightarrow \langle \mathcal {A}'',[~],n'',\mathtt{end}\rangle \) then \(\mathcal {W}(\mathcal {A},s',n)\)=\(\mathcal {A''}\).
Now, let us consider (\(s=ad::s'\)). Since \(ad.kind \) can be:
-
Case (add):
Since \(ad.pos \) can be:
-
Subcase (before):
From the rule (Before) of the semantic weaving rules presented in Fig. 24, we conclude:

By the completeness of the algorithm \(\mathcal {M}\), we conclude:
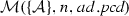
From the algorithm \(\mathcal {W}\), we conclude:
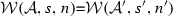
By the hypothesis, we conclude:
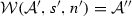
-
Subcase (after):
From the rule (After) of the semantic weaving rules presented in Fig. 24, we conclude:

By the completeness of the algorithm \(\mathcal {M}\), we conclude:
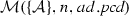
From the algorithm \(\mathcal {W}\), we conclude:
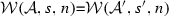
By the hypothesis, we conclude:
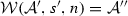
-
Subcase (around with proceed):
From the rule (AroundWProceed) of the semantic weaving rules presented in Fig. 24, we conclude:

By the completeness of the algorithm \(\mathcal {M}\), we conclude:
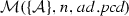
By the completeness of the algorithm containProceed, we conclude:
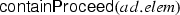
By the completeness of the algorithm substitute, we conclude:
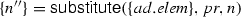
From the algorithm \(\mathcal {W}\), we conclude:
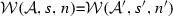
By the hypothesis, we conclude:
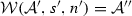
-
Subcase (around without proceed):
From the rule (AroundWouProceed) of the semantic weaving rules presented in Fig. 24, we conclude:

By the completeness of the algorithm \(\mathcal {M}\), we conclude:
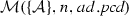
By the completeness of the algorithm containProceed, we conclude:
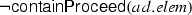
By the completeness of the algorithm substitute, we conclude:
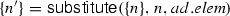
From the algorithm \(\mathcal {W}\), we conclude:
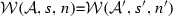
By the hypothesis, we conclude:
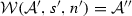
-
-
Case (remove):
From the rule (Remove) of the semantic weaving rules presented in Fig. 24, we conclude:

By the completeness of the algorithm \(\mathcal {M}\), we conclude:
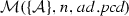
From the algorithm \(\mathcal {W}\), we conclude:
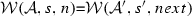
By the hypothesis, we conclude:
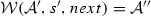
-
Case (no match):
From the rule (NoMatch) of the semantic weaving rules presented in Fig. 24, we conclude:
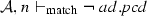
By the soundness and the completeness of the algorithm \(\mathcal {M}\), we conclude:
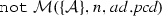
From the algorithm \(\mathcal {W}\), we conclude:
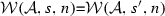
By the hypothesis, we conclude:
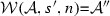
-
\(\square \)
Rights and permissions
About this article
Cite this article
Mouheb, D., Alhadidi, D., Nouh, M. et al. Aspect-oriented modeling framework for security hardening. Innovations Syst Softw Eng 12, 41–67 (2016). https://doi.org/10.1007/s11334-015-0263-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11334-015-0263-5