Abstract
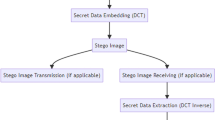
In this paper, a steganographic method for real-time data hiding is proposed. The main goal of the research is to develop steganographic method with increased robustness to unintentional image processing attacks. In addition, we prove the validity of the method in real-time applications. The method is based on a discrete cosine transform (DCT) where the values of a DCT coefficients are modified in order to hide data. This modification is invisible to a human observer. We further the investigation by implementing the proposed method using different target architectures and analyze their performance. Results show that the proposed method is very robust to image compression, scaling and blurring. In addition, modification of the image is imperceptible even though the number of embedded bits is high. The steganalysis of the method shows that the detection of the modification of the image is unreliable for a lower relative payload size embedded. Analysis of OpenCL implementation of the proposed method on four different target architectures shows considerable speedups.




















Similar content being viewed by others
References
Alvarez, P.: Using extended file information (EXIF) file headers in digital evidence analysis. Int. J. Digit. Evid. 2(3), 1–5 (2004)
AMD (2015a) AMD A series APU processors,15.6.2015. http://www.amd.com/en-us/products/processors/desktop/a-series-apu
AMD (2015b) AMD Radeon HD 8670d, 15.6.2015. http://www.pc-specs.com/gpu/AMD/APU_Family/Radeon_HD_8670D/1787
Bamatraf, A., Ibrahim, R., Salleh, M.N.B.M.: Digital watermarking algorithm using LSB. In: 2010 International Conference on Computer Applications and Industrial Electronics, IEEE, Iccaie, pp. 155–159 (2010). doi:10.1109/ICCAIE.2010.5735066, http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=5735066
Bhatnagar, G., Raman, B.: A new robust reference watermarking scheme based on DWT-SVD. Comput. Stand. Interfaces 31(5), 1002–1013 (2009). doi:10.1016/j.csi.2008.09.031, http://linkinghub.elsevier.com/retrieve/pii/S0920548908001499
Celik, M., Sharma, G., Tekalp, A., Saber, E.: Lossless generalized-LSB data embedding. In: IEEE Transactions on Image Processing 14(2), 253–266 (2005). doi:10.1109/TIP.2004.840686, http://www.ncbi.nlm.nih.gov/pubmed/15700530 http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=1381493
Cheddad, A., Condell, J., Curran, K., Mc Kevitt, P.: Digital image steganography: Survey and analysis of current methods. Signal Process. 90(3), 727–752 (2010). doi:10.1016/j.sigpro.2009.08.010. http://linkinghub.elsevier.com/retrieve/pii/S0165168409003648
Cox, I., Miller, M., Bloom, J., Fridrich, J., Kalker, T.: Digital Watermarking and Steganography, 2nd edn. Morgan Kaufmann Publishers, San Francisco (2008)
CUDA (2016) CUDA toolkit documentation-sample reference. http://docs.nvidia.com/cuda/cuda-samples
Dey, S., Abraham, A., Sanyal, S.: An LSB data hiding technique using prime numbers. In: Third International Symposium on Information Assurance and Security, IEEE 1, 101–108 (2007). doi:10.1109/IAS.2007.37. http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=4299758
Dosselmann, R., Yang, X.D.: A comprehensive assessment of the structural similarity index. SIViP 5(1), 81–91 (2011). doi:10.1007/s11760-009-0144-1
Groups, K.: OpenCL Consortium. https://www.khronos.org/opencl (2016)
Hashad, A., Madani, A., Wahdan, A.M.a.: A robust steganography technique using discrete cosine transform insertion. In: 2005 International Conference on Information and Communication Technology, IEEE, Cairo, pp. 255–264 (2005). doi:10.1109/ITICT.2005.1609628. http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=1609628
Kang, X., Huang, J., Member, S., Zeng, W.: Efficient general print-scanning resilient data hiding based on uniform log-polar mapping. In: IEEE Transactions on Information Forensics and Security 5(1), 1–12 (2010). doi:10.1109/TIFS.2009.2039604. http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=5378607
Kedmenec, L., Poljicak, A., Mandic, L.: Copyright protection of images on a social network. In: Proceedings ELMAR-2014, IEEE, September, pp. 1–4 (2014). doi:10.1109/ELMAR.2014.6923345. http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=6923345
Kee, E., Johnson, M.K., Farid, H.: Digital image authentication from JPEG headers. In: IEEE Transactions on Information Forensics and Security 6(3), 1066–1075 (2011). doi:10.1109/TIFS.2011.2128309. http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=5732683
Kodovský, J., Fridrich, J., Holub, V.: Ensemble classifiers for steganalysis of digital media. IEEE Trans. Inf. Forensics Secur. 7(2), 432–444 (2012). doi:10.1109/TIFS.2011.2175919
Kurak, C., McHugh, J.: A cautionary note on image downgrading. In: 1992 Proceedings Eighth Annual Computer Security Application Conference, IEEE Comput. Soc. Press, pp. 153–159 (1992). doi:10.1109/CSAC.1992.228224. http://ieeexplore.ieee.org/xpls/abs_all.jsp?arnumber=228224 http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=228224
Lu, W., Sun, W., Lu, H.: Robust watermarking based on DWT and nonnegative matrix factorization. Computers & Electrical Engineering 35(1), 183–188 (2009). doi:10.1016/j.compeleceng.2008.09.004. http://linkinghub.elsevier.com/retrieve/pii/S0045790608001067
Naveed, I., Puech, W.: Data cryptography. In: Naït-Ali, A., Fournier, R. (eds.) Signal and image processing for biometrics. Wiley, Hoboken, pp. 263–277 (2013). doi:10.1002/9781118561911.ch13.
Parthasarathy, A., Kak, S.: An Improved method of content based image watermarking. IEEE Trans. Broadcast. 53(2), 468–479 (2007). doi:10.1109/TBC.2007.894947. http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=4215117
Pevny, T., Fridrich, J.: Merging Markov and DCT features for multi-class JPEG steganalysis. Proc SPIE 6505(650), 503 (2007). doi:10.1117/12.696774. http://link.aip.org/link/?PSISDG/6505/650503/1
Poljicak, A., Mandic, L., Agic, D.: Discrete fourier transformbased watermarking method with an optimal implementation radius. J. Electron. Imaging 20(3):033,008 (2011). doi:10.1117/1.3609010. http://link.aip.org/link/JEIME5/v20/i3/p033008/s1 \(\{\)&\(\}\)Agg=doi
Scarpino, M.: OpenCL in Action: How to Accelerate Graphics and Computation. NY (2012)
Schneier, B.: Applied Cryptography: Protocols, Algorithm, and Source Code in C, 2nd edn. Wiley, New York (1995)
Shi, Y., Chen, C., Chen, W.: A Markov process-based approach to effective attacking JPEG steganography. Inf. Hiding, pp. 249–264 (2007). doi:10.1007/978-3-540-74124-4. http://www.springerlink.com/index/c308w1674110v420.pdf
Sung, T., Shieh, Y., Yu, C., Hsin, H.: High-efficiency and low-power architectures for 2-d dct and idct based on cordic rotation. In: Seventh International Conference on Parallel and Distributed Computing, Applications and Technologies, 2006. PDCAT ’06, pp. 191–196 (2006). doi:10.1109/PDCAT.2006.70
Wang, Z., Bovik, A.C., Sheikh, H.R., Simoncelli, E.P.: Image quality assessment: from error visibility to structural similarity. IEEE Trans. Image Process. 13(4), 600–612 (2004). doi:10.1109/TIP.2003.819861
Author information
Authors and Affiliations
Corresponding author
Additional information
This work has been supported by the EU (FEDER) and the Spanish MINECO, under grants TIN 2015-65277-R and TIN2012-32180.
Rights and permissions
About this article
Cite this article
Poljicak, A., Botella, G., Garcia, C. et al. Portable real-time DCT-based steganography using OpenCL. J Real-Time Image Proc 14, 87–99 (2018). https://doi.org/10.1007/s11554-016-0616-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11554-016-0616-9