Abstract
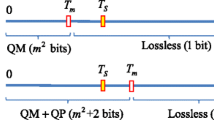
This paper presents a lossless data hiding method for an absolute moment block truncation coding (AMBTC) images, which is a compressed grayscale image. It is not easy to hide secret data in an AMBTC-compressed image because it is composed of bit planes. Thus, it is very sensitive to change some pixels. Nevertheless, to improve the hiding capacity, we present an efficient extension of the histogram modification technique by counting the coefficients of the bit planes in each 4 × 4 block. In addition, our proposed scheme has low complexity and achieves a high embedding capacity with the good perceptual quality compared to the prior arts. In an experiment, we verified our proposed data hiding scheme through the comparison with previous methods.













Similar content being viewed by others
References
Delp, E.J., Mitchell, O.R.: Image compression using block truncation coding. IEEE Trans. Commun. 27(9), 1335–1342 (1979)
Wu, Y.G., Tai, S.C.: An efficient BTC image compression technique. IEEE Trans. Consum. Electron. 44(2), 317–325 (1998)
Suhail, M.A., Obaidat, M.S.: Digital watermarking-based DCT and JPEG model. IEEE Trans. Instrum. Meas. 52(5), 1640–1647 (2003)
Khan, M.K., Xie, L., Zhang, J.: Robust hiding of fingerprint biometric data into audio signals. In: Lee S.W., Li S.Z. (eds.) International Conference, ICB 2007, Lecture Notes in Computer Science, vol. 4642, pp. 702–712. Springer, Berlin, Heidelberg (2007)
Kim, C., Yang, C.N.: Watermark with DSA signature using predictive coding. Multimed. Tools Appl. 74(14), 5189–5203 (2015)
Kim, C.: Data hiding by an improved exploiting modification direction. Multimed. Tools Appl. 69(3), 569–584 (2014)
Yang, C.N., Ye, G.C., Kim, C.: Data hiding in halftone images by XOR block-wise operation with difference minimization. KSII Trans. Internet Inf. Syst. (TIIS) 5(2), 457–476 (2011)
Huy, P.T., Thanh, N.H., Kim, C., Yang, C.N.: Data-hiding for halftone images using an improved CPT scheme. KSII Trans. Internet Inf. Syst. (TIIS) 7(2), 405–424 (2013)
Diffile, W., Hellman, M.: New directions in cryptography. IEEE Trans. Inf. Theory 22(6), 644–654 (1976)
Neelamani, R., Queiroz, R.D., Fan, Z., Dash, S., Baraniuk, R.G.: JPEG compression history estimation for color images. IEEE Trans. Image Process. 15(6), 1365–1378 (2006)
Pfarrhofer, R., Uhl, A.: Selective image encryption using JBIG. Lect. Notes Comput. Sci. 3677, 98–107 (2005)
Guo, J.M.: Improved block truncation coding using modified error diffusion. Electron. Lett. 44(7), 462–464 (2008)
Lin, M.H., Chang, C.C.: A novel information hiding scheme based on BTC. In: Proceedings of 4th International Conference on Computer and Information Technology, pp. 66–71 (2004)
Chuang, J.C., Chang, C.C.: Using a simple and fast image compression algorithm to hide secret information. Int. J. Comput. Appl. 28(4), 329–333 (2006)
Fridrich, J., Goljan, M., Du, R.: Lossless data embedding new paradigm in digital watermarking. EURASIP J. Adv. Signal Process. 2002(2), 185–196 (2002)
Kalker, T., Willems, F.M.J.: Capacity bounds and constructions for reversible data hiding. In: Delp III E.J., Wong P.W. (eds.) Proc. SPIE 5020, Security and Watermarking Multimedia Contents V, vol. 5020, pp. 604–611. Santa Clara, CA (2003)
Celik, M.U., Sharma, G., Tekalp, A.M., Saber, E.: Lossless generalized-LSB data embedding. IEEE Trans. Image Process. 14(2), 253–266 (2005)
Tian, J.: Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 13(8), 890–896 (2003)
Kamstra, L., Heijmans, H.J.A.M.: Reversible data embedding into images using wavelet techniques and sorting. IEEE Trans. Image Process. 14(12), 2082–2090 (2005)
Thodi, D.M., Rodriguez, J.J.: Expansion embedding techniques for reversible watermarking. IEEE Trans. Image Process. 16(3), 721–730 (2007)
Ni, Z., Shi, Y.Q., Ansari, N., Su, W.: Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 16(3), 354–362 (2006)
Lee, S.K., Suh, Y.H., Ho, Y.S.: Reversible image authentication based on watermarking. In: Proceedings of the IEEE International Conference on Multimedia Expo, pp. 1321–1324 (2006)
Hong, W., Chen, T.S., Shiu, C.W.: Reversible data hiding for high quality images using modification of prediction errors. J. Syst. Softw. 82(11), 1833–1842 (2009)
Zhao, H., Wang, H.X., Khan, M.K.: Statistical analysis of several reversible data hiding algorithms. J. Multimed. Tools Appl. 52(2), 277–290 (2011)
Hong, W., Chen, T.S., Shiu, C.W.: Lossless steganography for AMBTC compressed images. In: Proceedings of 1st International Congress on Image and Signal Processing, pp. 13–17 (2008)
Chen, J., Hong, W., Chen, T.S., Shiu, C.W.: Steganography for BTC compressed images using no distortion technique. Imaging Sci. J. 58(4), 177–185 (2010)
Sun, W., Lu, Z.M., Wen, Y.C., Yu, F.X., Shen, R.J.: High performance reversible data hiding for block truncation coding compressed images. SIViP 7(2), 297–306 (2013)
Lo, C.C., Hu, Y.C., Chen, W.L., Wu, C.M.: Reversible data hiding scheme for BTC-compressed images based on histogram shifting. Int. J. Secur. Appl. 8(2), 301–314 (2014)
Lema, M.D., Mitchell, O.R.: Absolute moment block truncation coding and its application to color images. IEEE Trans. Commun. 32(10), 1148–1157 (1984)
USC-SIPI image database website. Last Accessed 6 Apr 2016. http://sipi.usc.edu/database/database.php
Acknowledgments
We are grateful for the support provided by the National Natural Science Foundation of China (61305010), Science and Technology Project of Education Department of Jiangxi Province (GJJ150715), Voyage Project of Jiangxi Province (201450), Open Foundation of Key Laboratory of Jiangxi Province for Image Processing and Pattern Recognition (TX201604002), and Doctoral Initiating Foundation of Nanchang Hangkong University (EA201620045). This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (2015R1D1A1A01059253). This work was supported under the framework of international cooperation program managed by the National Research Foundation of Korea (2016K2A9A2A05005255, FY20**).
Author information
Authors and Affiliations
Corresponding authors
Rights and permissions
About this article
Cite this article
Kim, C., Shin, D., Leng, L. et al. Lossless data hiding for absolute moment block truncation coding using histogram modification. J Real-Time Image Proc 14, 101–114 (2018). https://doi.org/10.1007/s11554-016-0641-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11554-016-0641-8