Abstract
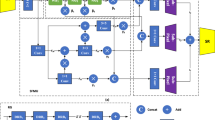
The prevailing method for steganographic payload location aimed at LSB matching is the MAP method, which requires a few hundreds of stego images with load-carrying pixels at same locations and relatively high embedding rates. However, in practice, especially communication security, it is unwise for steganographers to generate stego images with high payloads or heavily utilize a same embedding key. Thus, the requirement of MAP is actually to some degree out of reach which leads to a performance degradation when faced with insufficient stego images with low embedding rates. To this end, we propose a tailored deep neural network (DNN) equipped with the improved feature named the “mean square of adjacency pixel difference”, which remarkably outperforms the previous state-of-the-art methods not only in terms of accuracy but also efficiency. Our approach can considerably reduce computational costs because no cover estimate, as represented by the key in MAP, is involved. This merit stems from the methodology we adopted that takes payload location as a binary classification problem for each pixel. Additionally, our DNN is consistently superior than MAP irrespective of embedding rates. The significance of our main design points in DNN and the improved features are verified, by experiment results. Besides, the time required in our method to handle 256 × 256 pixel images is 82.54 ms on the average, which is nearly 14 times faster than that of MAP. On the basis of relevant knowledge, the incorporation of feature extraction into DNN architecture is likely to enable future researchers to specify real-time payload locations.





Similar content being viewed by others
References
Provos, N., Honeyman, P.: Hide and seek: An introduction to steganography. IEEE Secur. Priv. 1, 32–44 (2003)
Wang, H., Wang, S.: Cyber warfare: steganography vs. steganalysis. Commun. ACM 47, 76–82 (2004)
Quach, T.T.: Optimal cover estimation methods and steganographic payload location. IEEE Trans. Inf. Forensics Secur. 6, 1214–1222 (2011)
Holub, V., Fridrich, J.: Designing steganographic distortion using directional filters. In: Proc. IEEE Int. Workshop Inf. Forensics Secur. (WIFS), pp. 234–239 (2012)
Holub, V., Fridrich, J., Denemark, T.: Universal distortion function for steganography in an arbitrary domain. EURASIP J. Inf. Secur. 2014(1), 1–13 (2014)
Pevný, T., Filler, T., Bas, P.: Using high-dimensional image models to perform highly undetectable steganography. In: Proc. Int. Workshop Inf. Hiding, pp. 161–177 (2010)
Qin, C., Chang, C., Chiu, Y.: A Novel Joint Data-Hiding and Compression Scheme Based on SMVQ and Image Inpainting. IEEE Trans. Image Process. 23(3), 969–978 (2014)
Chuan Qin, W.Z., Cao, F., Zhang, X., Chin-Chen, C.: Separable reversible data hiding in encrypted images via adaptive embedding strategy with block selection. Signal Process. 153, 109–122 (2018)
Petitcolas, F.A.P., Anderson, R.J., Kuhn, M.G.: Information hiding-a survey, In: Proceedings of the IEEE, vol. 87, pp. 1062–1078 (1999)
Sharp, T.: (2001) An Implementation of Key-Based Digital Signal Steganography, International Workshop on Information Hiding, pp. 13–26 (2001)
Ker, A.D.: Locating steganographic payload via WS residuals. In: Proc. 10th Multimedia and Security Workshop, pp. 27–31. ACM (2008)
Ker, A.D., Lubenko, I.: Feature reduction and payload location with WAM steganalysis Proceedings of SPIE—The International Society for Optical Engineering, p. 7254 (2009)
Yan, X., Tao, Z., Ling, X., Ping, X.: New method for payload location aimed at LSB matching. J. Data Acquis. Process. 31(1), 145–151 (2016) (in Chinese)
Pibre, L., Pasquet, J., Ienco, D., Chaumont, M.: Deep learning is a good steganalysis tool when embedding key is reused for different images, even if there is a cover sourcemismatch. Electron. Imaging 4, 1–11 (2016)
Qian, Y., Dong, J., Wang, W., Tan, T.: (2015) Deep learning for steganalysis via convolutional neural networks, Proc. SPIE, vol. 9409, p. 94090J (2015)
Xu, G., Wu, H.Z., Shi, Y.Q.: Structural design of convolutional neural networks for steganalysis. IEEE Signal Process. Lett. 23, 708–712 (2016)
Chen, M., Fridrich, J., Boroumand, M.: (2018) Deep learning regressors for quantitative steganalysis. Electronic imaging, media watermarking, security, and forensics, pp. 160-1-160-7(7) (2018)
Xie, S., Girshick, R., Dollar, P., et al. Aggregated residual transformations for deep neural networks. In: IEEE Conference on Computer Vision & Pattern Recognition. IEEE Computer Society (2017)
Huang, G., Liu, Z., Laurens, V.D.M., Weinberger, K.Q.: Densely connected convolutional networks, pp. 2261–2269 (2016)
Zhao, B., Feng, J., Wu, X., Yan, S.: A survey on deep learning-based fine-grained object classification and semantic segmentation International. J. Autom. Comput. 14, 119–135 (2017)
He, K., Zhang, X., Ren, S., Sun, J.: Deep Residual learning for image recognition, pp 770–778 (2015)
Krizhevsky, A., Sutskever, I., Hinton, G.E.: ImageNet classification with deep convolutional neural networks. In: International Conference on Neural Information Processing Systems (2012)
Khan, S.H., Hayat, M., Bennamoun, M., Sohel, F.A., Togneri, R.: Cost-sensitive learning of deep feature representations from imbalanced data. IEEE Trans. Neural Netw. Learn. Syst. 29, 3573–3587 (2015)
He, H., Garcia, E.A.: Learning from imbalanced data. IEEE Trans. Knowl. Data Eng. 21, 1263–1284 (2009)
Bas, P., Filler, T., Pevný, T.: Break our steganographic system: The Ins and outs of organizing BOSS. In Proc. Int. Workshop Inf. Hiding. Springer, Berlin, Heidelberg, pp. 59–70 (2011)
Bas, P., Furon, T.: Bows-2. http://bows2.gipsa-lab.inpg.fr (2007)
Jia, Y., Shelhamer, E., Donahue, J., Karayev, S., Long, J., Girshick, R., Guadarrama, S., Darrell, T.: Caffe: Convolutional architecture for fast feature embedding, 675–678 (2014)
Zeiler, M.D.: (2012) ADADELTA: An adaptive learning rate method computer science
Simonyan, K., Zisserman, A.: (2014) Very deep convolutional networks for large-scale image recognition computer science
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sun, Y., Zhang, H., Zhang, T. et al. Deep neural networks for efficient steganographic payload location. J Real-Time Image Proc 16, 635–647 (2019). https://doi.org/10.1007/s11554-019-00849-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11554-019-00849-y