Abstract
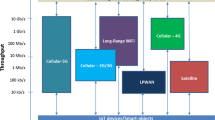
In recent years, Internet of Things (IoT), which aims to achieve ubiquitous communication among a large number of resource constraint embedded devices, has emerged as a new paradigm in the field of wireless communications. Enabling the IoT essentially requires thousands of low-power and low cost embedded devices to be efficiently and seamlessly interconnected. Consequently, routing protocols play a crucial role in providing the interoperability for IoT components. In order to turn IoT into reality, IETF has standardized the IPv6 Routing Protocols for Low-power and Lossy Networks (RPL). As the pervasiveness of RPL increases, a comprehensive survey of RPL is crucial to pave the way for researchers to understand and contribute in the relevant research area of RPL. Therefore, in this paper, we present a comprehensive study of RPL protocol as well as its latest and standardized addition, i.e., point-to-point RPL (P2P-RPL). Specifically, this paper focuses on performance evaluations, research challenges and envisioned opportunities of RPL. In addition, we also introduce a NS-3 framework design of RPL and P2P-RPL protocols. Furthermore, extensive simulation studies are conducted across various scenarios to demonstrate the flexibility and effectiveness of RPL and P2P-RPL protocols. Moreover, research gaps and challenges facing in RPL and P2P-RPL protocols are also addressed. Finally, we summarize the paper by providing valuable insights of enabling technologies and suggestions for future research.


















Similar content being viewed by others
Notes
1 In the non-strong mode, this existing route is along the pre-established DAG and via the root.
2 It is observed that the wireless links have asymmetric nature, mainly because of transmitter power and receiver sensitivity which is different from node to node [77].
References
Al-Omar BA, Landolsi T, Al-Ali A (2015) Evaluation of wimax technology in smart grid communications. J Commun 10 (10)
Atzori L, Iera A, Morabito G (2010) The internet of things: A survey. Comput Netw 54(15):2787–2805
Baccelli E, Philipp M, Goyal M (2011) The p2p-rpl routing protocol for ipv6 sensor networks: Testbed experiments. In: The Proceedings of the 19th IEEE International Conference on Software, Telecommunications and Computer Networks (SoftCOM), pp 1–6
Bartolozzi L, Pecorella T, Fantacci R (2012) Ns-3 rpl module: Ipv6 routing protocol for low power and lossy networks. In: The Proceedings of the 5th International ICST Conference on Simulation Tools and Techniques, pp 359–366
Basu P, Redi J (2004) Effect of overhearing transmissions on energy efficiency in dense sensor networks. In: The Proceedings of the 3rd international symposium on Information processing in sensor networks, pp 196–204
Biswas S, Morris R (2005) Exor: opportunistic multi-hop routing for wireless networks. ACM SIGCOMM Comput Commun Rev 35(4):133–144
Bormann C, Castellani AP, Shelby Z (2012) Coap: An application protocol for billions of tiny internet nodes. IEEE Internet Comput 16(2):62
Boulis A (2007) Castalia: revealing pitfalls in designing distributed algorithms in wsn. In: The Proceedings of the 5th ACM international conference on Embedded networked sensor systems, pp 407–408
Brachman A (2013) Rpl objective function impact on llns topology and performance. Springer, pp 340–351
Brandt A, Buron J (2010) Home automation routing requirements in low-power and lossy networks
Cam-Winget N, Toutain L, Hui J, Popa D, Gillmore M, Monden K (2015) Applicability statement for the routing protocol for low power and lossy networks (rpl) in ami networks
Campolo C, Molinaro A, Scopigno R (2015) Vehicular ad hoc networks: Standards, solutions, and research
Chachulski S, Jennings M, Katti S, Katabi D (2007) Trading structure for randomness in wireless opportunistic routing, vol 37. ACM
Chakeres ID, Klein-Berndt L (2002) Aodvjr, aodv simplified. ACM SIGMOBILE Mob Comput Commun Rev 6(3):100– 101
Chen YB, Hou KM, Chanet JP, El Gholami K (2013) A rpl based adaptive and scalable data-collection protocol module for ns-3 simulation platform. NICST 2103 New Information Communication Science and Technology for Sustainable Development: France-China International Workshop pp. 8–p
Clausen TH, De Verdière AC (2011) The lln on-demand ad hoc distance-vector routing protocol-next generation (loadng)
Cuomo F, Abbagnale A, Cipollone E (2013) Cross-layer network formation for energy-efficient ieee 802.15. 4/zigbee wireless sensor networks. Ad Hoc Netw 11(2):672–686
Dawson-Haggerty S, Tavakoli A, Culler D (2010) Hydro: A hybrid routing protocol for low-power and lossy networks. In: The Proceedings of the First IEEE International Conference on Smart Grid Communications (SmartGridComm), pp 268– 273
Depuru S.S.S.R., Wang L, Devabhaktuni V (2011) Smart meters for power grid: Challenges, issues, advantages and status. Renew Sust Energy Rev 15(6):2736–2742
Dvir A, Holczer T, Buttyan L (2011) Vera-version number and rank authentication in rpl. In: The Proceedings of the 8th IEEE International Conference on Mobile Adhoc and Sensor Systems (MASS), pp 709–714
Elloumi O, Song J, Ghamri-Doudane Y, Leung V (2015) Iot/m2m from research to standards: the next steps (part i)[guest editorial]. IEEE Commun Mag 53(9):8–9
Fonseca R, Ratnasamy S, Culler D, Shenker S, Stoica I (2004) Beacon vector routing: Scalable point-to-point in wireless sensornets. IRB-TR-04-012, Berkeley: Intel Res 14
Gaddour O, Koubâa A (2012) Rpl in a nutshell: A survey. Comput Netw 56(14):3163–3178
Ghavimi F, Chen HH (2015) M2m communications in 3gpp lte/lte-a networks: Architectures, service requirements, challenges, and applications. IEEE Commun Surv Tutorials 17(2):525–549
Gnawali O (2012) The minimum rank with hysteresis objective function
Gnawali O, Fonseca R, Jamieson K, Moss D, Levis P (2009) Collection tree protocol. In: The Proceedings of the 7th ACM Conference on Embedded Networked Sensor Systems, pp 1– 14
Gnawali O, Levis P (2011) The minimum rank objective function with hysteresis, draft-ietf-roll-minrank-hysteresis-of-10 work in progress. The Minimum Rank Objective Function with Hysteresis, draft-ietf-roll-minrank-hysteresis-of-10 work in progress
Gomez C, Salvatella P, Alonso O, Paradells J (2006) Adapting aodv for ieee 802.15. 4 mesh sensor networks: theoretical discussion and performance evaluation in a real environment. In: The Proceedings of the IEEE Computer Society International Symposium on on World of Wireless, Mobile and Multimedia Networks, pp 159–170
Gong MX, Perahia E, Mao S, Hart B (2015) Advanced technologies in gigabit wireless lans: An in-depth overview of 802.11 ac. Fut Wirel Netw: Architectures, Protocol, Serv 21:23
Gormus S, Tosato F, Fan Z, Bocus Z, Kulkarni P (2012) Opportunistic rpl for reliable ami mesh networks. Wireless Networks:1–18
Goyal M, Baccelli E, Philipp M, Brandt A, Martocci J (2012) Reactive discovery of point-to-point routes in low power and lossy networks (draft-ietf-roll-p2p-rpl-09). Technical Report, Internet Draft, Work in Progress
Goyal M, Brandt A, Baccelli E (2013) A mechanism to measure the routing metrics along a point-to-point route in a low-power and lossy network
Goyal M, Philipp M, Brandt A, Baccelli E (2013) Reactive discovery of point-to-point routes in low-power and lossy networks
Güngör VC, Sahin D, Kocak T, Ergüt S, Buccella C, Cecati C, Hancke GP (2011) Smart grid technologies: communication technologies and standards. IEEE Trans Indust Inf 7(4):529– 539
Han D, Gnawali O (2013) Performance of rpl under wireless interference. IEEE Commun Mag 51(12):137–143
Herberg U, Clausen T (2011) A comparative performance study of the routing protocols load and rpl with bi-directional traffic in low-power and lossy networks (lln). In: The Proceedings of the 8th ACM Symposium on Performance evaluation of wireless ad hoc, sensor, and ubiquitous networks, pp 73–80
Herberg U, Clausen T (2011) Study of multipoint-to-point and broadcast traffic performance in the ipv6 routing protocol for low power and lossy networks. J Ambient Intell Humanized Comput 2(4):293–305
Hui J, Vasseur J, Culler D, Manral V (2012) An ipv6 routing header for source routes with the routing protocol for low-power and lossy networks (rpl). Technical Report, RFC 6554 (Proposed Standard), Internet Engineering Task Force
Hui JW, Culler DE (2008) Ip is dead, long live ip for wireless sensor networks. In: The Proceedings of the 6th ACM Conference on Embedded Network Sensor Systems, pp 15–28
Hull B, Jamieson K, Balakrishnan H (2004) Mitigating congestion in wireless sensor networks. In: The Proceedings of the 2nd international conference on Embedded Networked Sensor Systems, pp 134–147
Janicijevic N, Lukic M, Mezei I (2011) Routing protocol for low-power and lossy wireless sensor networks. In: The Proceedings of the 19th IEEE Telecommunications Forum (TELFOR), pp 234–237
Jarry A, Leone P, Powell O, Rolim J (2006) An optimal data propagation algorithm for maximizing the lifespan of sensor networks. Springer, pp 405–421
Kim J, Lee J, Kim J, Yun J (2014) M2m service platforms: survey, issues, and enabling technologies. IEEE Commun Surv Tutorials 16(1):61–76
Long J, Dong M, Ota K, Liu A, Hai S (2015) Reliability guaranteed efficient data gathering in wireless sensor networks. IEEE Access 3:430–444
Katti S, Rahul H, Hu W, Katabi D, Médard M, Crowcroft J (2006) Xors in the air: practical wireless network coding. ACM SIGCOMM Comput Commun Rev 36(4):243–254
Kim K, Park SD, Montenegro G, Yoo S, Kushalnagar N (2007) 6lowpan ad hoc on-demand distance vector routing (load). Netw WG Internet Draft (Work in Progress) 19
Ko J, Eriksson J, Tsiftes N, Dawson-Haggerty S, Vasseur JP, Durvy M, Terzis A, Dunkels A, Culler D (2011) Industry: beyond interoperability: pushing the performance of sensor network ip stacks. In: The Proceedings of the 9th ACM Conference on Embedded Networked Sensor Systems, pp 1– 11
Ko J, Terzis A, Dawson-Haggerty S, Culler DE, Hui JW, Levis P (2011) Connecting low-power and lossy networks to the internet. IEEE Commun Mag 49(4):96–101
Korte KD, Sehgal A, Schönwälder J (2012) A study of the rpl repair process using contikirpl. Springer, pp 50–61
Koubaa A, Cunha A, Alves M (2007) A time division beacon scheduling mechanism for ieee 802.15. 4/zigbee cluster-tree wireless sensor networks. In: The Proceedings of the 19th Euromicro Conference on Real-Time Systems (ECRTS’07), pp 125– 135
Kramer G (2015) Ethernet passive optical networks
Landsmann M, Wahlisch M, Schmidt T (2013) Topology authentication in rpl. IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS) pp 73–74
Levis P, Clausen T, Hui J, Gnawali O, Ko J (2011) The trickle algorithm. Internet Engineering Task Force, RFC6206
Levis P, Tavakoli A, Dawson-Haggerty S (2009) Overview of existing routing protocols for low power and lossy networks. Internet Engineering Task Force, Internet-Draft draftietf-roll-protocols-survey-07
Levis PA, Patel N, Culler D, Shenker S (2003) Trickle: A self regulating algorithm for code propagation and maintenance in wireless sensor networks. Computer Science Division University of California
Lien SY, Chen KC (2011) Massive access management for qos guarantees in 3gpp machine-to-machine communications. IEEE Commun Lett 15(3):311–313
Liu A, Jin X, Cui G, Chen Z (2013) Deployment guidelines for achieving maximum lifetime and avoiding energy holes in sensor network. Inf Sci 230:197–226
Long NT, De Caro N, Colitti W, Touhafi A, Steenhaut K (2012) Comparative performance study of rpl in wireless sensor networks. In: The Proceedings of the 19th IEEE Symposium on Communications and Vehicular Technology in the Benelux (SCVT), pp 1–6
Martocci J, Mil P, Riou N, Vermeylen W (2010) Building automation routing requirements in low-power and lossy networks
Misra P, Ahmed N, Ostry D, Jha S (2011) Characterization of asymmetry in low-power wireless links: an empirical study. Springer, pp 340–351
Zhao M, Md. Nawaz Ali GG, Lu R, Joo Chong PH (2016) An Energy-Efficient and Self-regioning based RPL for Low-power and Lossy Networks. In: The Proceedings of the 84th IEEE Vehicular Technology Conference . to appear
Montenegro G, Kushalnagar N (2005) Aodv for ieee 802.15. 4 networks. draft-Montenegro-lowpan-aodv-00 IETF Internet Draft (Work in progress)
Moritz G, Golatowski F, Lerche C, Timmermann D (2013) Beyond 6lowpan: Web services in wireless sensor networks. IEEE Trans Indust Inf 9(4):1795–1805
Dong M, Ota K, Liu A, Guo M (2016) Joint optimization of lifetime and transport delay under reliability constraint wireless sensor networks. IEEE Trans Parallel Distrib Syst 27(1):225– 236
Dong M, Ota K, Yang LT, Chang S, Zhu H, Zhou Z (2014) Mobile agent-based energy-aware and user-centric data collection in wireless sensor networks. Comput Netw 74:58– 70
Ooi CC, Fisal N (2004) Implementation of geocast-enhanced aodv-bis routing protocol in manet. In: The Proceedings of IEEE Region 10 Conference on TENCON, pp 660– 663
Panichpapiboon S, Ferrari G, Tonguz OK (2006) Optimal transmit power in wireless sensor networks. IEEE Trans Mob Comput 5(10):1432–1447
Park M (2015) Ieee 802.11 ah: sub-1-ghz license-exempt operation for the internet of things. IEEE Commun Mag 53(9):145– 151
Pavkovic B, Duda A, Hwang WJ, Theoleyre F (2014) Efficient topology construction for rpl over ieee 802.15. 4 in wireless sensor networks. Ad Hoc Netw 15:25–38
Pavkovic B, Theoleyre F, Duda A (2011) Ieee 802.15. 4 and rpl crossoptimization for reliable opportunistic routing in wsn. In: The Proceedings of the ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems (MSWiM), Miami, USA
Pavković B, Theoleyre F, Duda A (2011) Multipath opportunistic rpl routing over ieee 802.15. 4. In: The Proceedings of the 14th ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, pp 179– 186
Perkins C, Belding-Royer E, Das S (2003) Ad hoc on-demand distance vector (aodv) routing, Technical Reprort
Pfletschinger S, Navarro M, Ibars C (2011) Energy-efficient data collection in wsn with network coding. 2011 IEEE GLOBECOM Workshops (GC Wkshps) pp 394–398
Pham NN, Youn J, Won C (2006) A comparison of wireless sensor network routing protocols on an experimental testbed. In: The Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, vol 2, pp 276–281
Yang Q, He S, Li J, Chen J, Sun Y (2015) Energy-Efficient Probabilistic area coverage in wireless sensor. IEEE Trans Veh Technol 61(1):367–377
Rao A, Ratnasamy S, Papadimitriou C, Shenker S, Stoica I (2003) Geographic routing without location information. In: Proceedings of the 9th Annual International Conference on Mobile Computing and Networking, pp 96–108
Ren F, He T, Das S, Lin C (2011) Traffic-aware dynamic routing to alleviate congestion in wireless sensor networks. IEEE Trans Parallel Distrib Syst 22(9):1585–1599
Lu R, Li X, Liang X, Shen XS, Lin X (2011) Grs: The green, reliability, and security of emerging machine to machine communications. IEEE Comm Mag 49(4):28–35
Lu R, Liang X, Li X, Lin X, Shen XS (2012) Eppa: an efficient and privacy-preserving aggregation scheme for secure smart grid communications. IEEE Trans Parallel Distrib Syst 23(9):1621– 1631
(2007) Source code repository, T.: Tymo: DYMO implementation for TinyOS. [Online] http://tymo.sourceforge.net/
Safdar V, Bashir F, Hamid Z, Afzal H, Pyun JY (2012) A hybrid routing protocol for wireless sensor networks with mobile sinks. In: The Proceedings of the 7th IEEE International Symposium on Wireless and Pervasive Computing (ISWPC) , pp 1–5
Sheng Z, Yang S, Yu Y, Vasilakos A, Mccann J, Leung K (2013) A survey on the ietf protocol suite for the internet of things: standards, challenges, and opportunities. IEEE Wirel Commun 20(6):91–98
He S, Shin D-H, Zhang J, Chen J, Sun Y Full-View Area Coverage in Camera Sensor Networks: Dimension Reduction and Near-optimal Solutions. IEEE Transactions on Vehicular Technology, 10.1109/TVT.2015.2498281. to appear
Song C, Liu M, Cao J, Zheng Y, Gong H, Chen G (2009) Maximizing network lifetime based on transmission range adjustment in wireless sensor networks. Comput Commun 32(11):1316– 1325
Sun Y, Gurewitz O, Du S, Tang L, Johnson DB (2009) Adb: an efficient multihop broadcast protocol based on asynchronous duty-cycling in wireless sensor networks. In: The Proceedings of the 7th ACM Conference on Embedded Networked Sensor Systems, pp 43–56
Thubert P (2010) Rpl objective function 0 draft-ietf-roll-of0-03 (work in progress)
Thubert P (2012) Objective function zero for the routing protocol for low-power and lossy networks (rpl)
Tian J, Yan T, Wang G (2015) A network coding based energy efficient data backup in survivability-heterogeneous sensor networks. IEEE Trans Mob Comput 14(10):1992–2006
Tunca C, Isik S, Donmez MY, Ersoy C (2014) Distributed mobile sink routing for wireless sensor networks: a survey. IEEE Commun Surv Tutorials 16(2):877–897
Vasseur J, Kim M, Pister K, Dejean N, Barthel D (2012) Routing metrics used for path calculation in low-power and lossy networks RFC6551
Vucinic M, Tourancheau B, Duda A (2013) Performance comparison of the rpl and loadng routing protocols in a home automation scenario. IEEE Wireless Communications and Networking Conference (WCNC) pp 1974–1979
Wang C, Li B, Sohraby K, Daneshmand M, Hu Y (2007) Upstream congestion control in wireless sensor networks through cross-layer optimization. IEEE J Sel Areas Commun 25(4):786– 795
Watteyne T, Molinaro A, Richichi MG, Dohler M (2011) From manet to ietf roll standardization: a paradigm shift in wsn routing protocols. IEEE Commun Surv Tutorials 13(4):688– 707
Xie HF, Zeng F, Zhang GQ, Su DL (2016) Simulation research on routing protocols in zigbee network. In: The Proceedings of the 6th International Asia Conference on Industrial Engineering and Management Innovation, pp 891–898
Li X, Lu R, Liang X, Shen X, Chen J, Lin X (2011) Smart community: an internet of things application. IEEE Commun Mag 49(11):68–75
Lin X, Lu R, Shen X, Nemoto Y, Kato N (2009) Sage: a strong privacy-preserving scheme against global eavesdropping for ehealth systems. IEEE J Sel Areas Commun 27(4):365– 378
Yi J, Clausen T, Igarashi Y (2013) Evaluation of routing protocol for low power and lossy networks: Loadng and rpl. In: The Proceedings of the IEEE Conference on Wireless Sensor (ICWISE), pp 19–24
Zhao M, Shwe HY, Chong PHJ (2015) Cluster-parent based rpl for low-power and lossy networks in building environment. In: The Proceedings of the 12th Annual IEEE Consumer Communications and Networking Conference (CCNC), pp 779– 784
Zheng J, Lee MJ (2004) Will ieee 802.15. 4 make ubiquitous networking a reality?: a discussion on a potential low power, low bit rate standard. IEEE Commun Mag 42(6):140–146
Acknowledgments
This research is funded by the Republic of Singapore’s National Research Foundation (NRF) through a grant to the Berkeley Education Alliance for Research in Singapore (BEARS) for the Singapore-Berkeley Building Efficiency and Sustainability in the Tropics (SinBerBEST) Program. BEARS has been established by the University of California, Berkeley as a center for intellectual excellence in research and education in Singapore.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhao, M., Kumar, A., Joo Chong, P.H. et al. A comprehensive study of RPL and P2P-RPL routing protocols: Implementation, challenges and opportunities. Peer-to-Peer Netw. Appl. 10, 1232–1256 (2017). https://doi.org/10.1007/s12083-016-0475-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-016-0475-y