Abstract
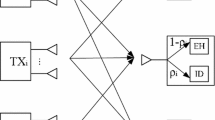
In this paper, the robust beamforming and artificial noise design is investigated in two-user interference networks with wireless information and power transfer. Specifically, we focus on the secure communication of the two pairs in the presence of an energy receiver (ER) which acts as the potential eavesdropper and intends to wiretap the confidential message transmitted to one of the information receivers (IRs). With only imperfect eavesdropper’s channel state information (ECSI) at the transmitters, our goal is to minimize the total transmit power, while guaranteeing the worst-case secrecy rate requirement at the wiretapped IR, the signal-to-interference-plus-noise ratio requirement at the wiretap-free IR and the energy harvesting requirement at the ER. In particular, we first model the imperfect ECSI in the sense of ellipsoidal uncertainties. Then, our design goal can be further reformulated as a two-stage optimization problem. With the help of rank relaxation and one-dimensional line search, the considered two-stage problem can be solved efficiently. Simulation results verify the effectiveness of the proposed design in different scenarios.








Similar content being viewed by others
References
Shiu Y.-S., Chang S.-Y., Wu H.-C., Huang S.-H., Chen H.-H. (2011) Physical layer security in wireless networks: a tutorial. IEEE Wireless Commun 18(2):66–74
Zhang H., Cheng P., Shi L., Chen J. (2016) Optimal DoS attack scheduling in wireless networked control system. IEEE Trans Control Syst Technol 24(3):843–852
Wyner A. D. (1975) The wire-tap channel. Bell Syst Tech J 54(8):1355–1387
Khisti A., Wornell G. W (2007) The MIMOME channel in. Proc Allerton Conf Commun Contr Computing Monticello IL:1–8
Khisti A., Wornell G. W (2010) Secure transmission with multiple antennas I: the MISOME wiretap channel. IEEE Trans Inf Theory 56(7):3088–3104
Zhang H., Cheng P., Shi L., Chen J. (2015) Optimal denial-of-service attack scheduling with energy constraint. IEEE Trans Autom Control 60(11):3023–3028
Yang N., Suraweera H., Collings I., Yuen C. (2013) Physical layer security of TAS/MRC with antenna correlation. IEEE Trans Inf Forens Security 8(1):254–259
Zhang J., Yuen C., Wen C. K., Jin S., Gao X. (2014) Ergodic secrecy sum-rate for multiuser downlink transmission via regularized channel inversion: Large system analysis. IEEE Commun Lett
Chen X., Lei L., Zhang H., Yuen C (2014) On the secrecy outage capacity of physical layer security in large-scale MIMO relaying systems with imperfect CSI in. Proc. IEEE ICC, Sydney, NSW Australia:1–6
Chen X., Yuen C., Zhang Z. (2014) Exploiting large-scale MIMO techniques for physical layer security with imperfect CSI. in Proc. IEEE Globcom
Dong L., Han Z., Petropulu A. P., Poor H. V. (2010) Improving wireless physical layer security via cooperating relays. IEEE Trans Signal Process 58(3):1875–1888
Krikidis I., Thompson J. S., McLaughlin S. (2009) Relay selection for secure cooperative networks with jamming. IEEE Trans Wireless Commun 8(10):5003–5011
Chen J., Xu W., He S., Sun Y., Thulasiraman P., Shen X. (2010) Utility-based asynchronous flow control algorithm for wireless sensor networks. IEEE J Sel Areas Commun 28(7):1116–1126
Meng W., Wang X., Liu S. (2016) Distributed load sharing of an inverter-based microgrid with reduced communication. IEEE Trans Smart Grid. doi:10.1109/TSG.2016.2587685.. to be published
Krikidis I., Timotheou S., Nikolaou S., Zheng G., Ng D. W. K., Schober R. (2014) Simultaneous wireless information and power transfer in modern communication systems,. IEEE Commun Mag 52(11):104–110
Ding Z., Zhong C., Ng D. W. K., Peng M., Suraweera H. A., Schober R., Poor H. V. (2015) Application of smart antenna technologies in simultaneous wireless information and power transfer. IEEE Commun Mag 53(4):86–93
Meng W., Yang Q., Sun Y. (2016) Guaranteed performance control of DFIG variable-speed wind turbines. IEEE Trans Control Syst Technol. doi:10.1109/TCST.2016.2524531.. to be published
Zhang R., Ho C. K. (2013) MIMO broadcasting for simultaneous wireless information and power transfer. IEEE Trans Wireless Commun 12:1989–2001
Huang K., Larsson E. (2013) Simultaneous information and power transfer for broadband wireless systems. IEEE Trans Signal Process 61:5972–5986
Chen J., Yu Q., Cheng P., Sun Y., Fan Y., Shen X. (2011) Game theoretical approach for channel allocation in wireless sensor and actuator networks,. IEEE Trans Autom Control 56(10):2332–2344
Shi Q., Liu L., Xu W., Zhang R. (2014) Joint transmit beamforming and receive power splitting for MISO SWIPT systems. IEEE Trans Wireless Commun 13(6):3269–3280
Shi Q., Xu W., Chang T.-H., Wang Y., Song E. (2014) Joint beamforming and power splitting for MISO interference channel with SWIPT: an SOCP relaxation and decentralized algorithm. IEEE Trans Signal Process 62(23):6194–6208
Shi X., Anderson B. D. O., Mao G., Yang Z., Chen J., Lin Z. (2016) Robust localization using time difference of arrivals. IEEE Signal Process Lett. doi:10.1109/LSP.2016.2569666.. to be published
Leng S., Ng D. W. K., Schober R (2014) Power efficient and secure multiuser communication systems with wireless information and power transfer in Proc. IEEE ICC, Sydney, NSW. Australia:800–806
Shi Q., Xu W., Wu J., Song E., Wang Y. (2015) Secure beamforming for MIMO broadcasting with wireless information and power transfer. IEEE Trans. Wireless Commun. 14(5):2841–2853
Ng D. W. K., Lo E. S., Schober R. (2016) Multiobjective resource allocation for secure communication in cognitive radio networks with wireless information and power transfer. IEEE Trans Veh Technol 65(5):3166–3184
Li Q., Zhang Q., Qin J. (2014) Secure relay beamforming for simultaneous wireless information and power transfer in nonregenerative relay networks. IEEE Trans Veh Technol 63 (5):2462–2467
Wu W., Wang B. (2015) Robust secrecy beamforming for wireless information and power transfer in multiuser MISO communication system,. Eurasip J Wireless Commun Networking 2015:161
Khandaker M. R. A., Wong K.-K. (2015) Masked beamforming in the presence of energy-harvesting eavesdroppers. IEEE Trans. Inf. Forensics Security 10(1):40–54
Feng R., Li Q., Zhang Q., Qin J. (2015) Robust secure transmission in MISO simultaneous wireless information and power transfer system. IEEE Trans Veh Technol 64(1):400–405
Zhang J., Yuen C., Wen C.-K., Jin S., Wong K.-K., Zhu H. (2016) Large system secrecy rate analysis for SWIPT MIMO wiretap channels. IEEE Trans Inf Forensics Security 11(1):74–85
Zhang Y., He S., Chen J. (2016) Data gathering optimization by dynamic sensing and routing in rechargeable sensor networks. IEEE/ACM Trans Netw 24(3):1632–1646
Liang Y., Poor H. V., Shamai S. (2008) Secure communication over fading channels. IEEE Trans Inf Theory 54(6):2470–2492
Boyd S., Vandenberghe L. (2004) Convex optimization. Cambridge. Cambridge University Press, U.K.
Grant M., Boyd S. (2010) CVX: Matlab software for disciplined convex programming, version 1.21 (2011),. Available: cvxr. com/cvx
Horn R. A., Johnson C. R. (1990) Matrix Analysis. Cambridge. Cambridge University Press, U.K.
Luo Z., Ma W. K., So A. M.-C., Ye Y., Zhang S. (2010) Semidefinite relaxation of quadratic optimization problems. IEEE Signal Process Mag 27(3):20–34
Ben-Tal A., Nemirovski A (2001) Lectures on Modern Convex Optimization: analysis, algorithms, and engineering applications. ser MPS-SIAM Series on Optimization
Timotheou S., Krikidis I., Zheng G., Ottersten B. (2014) Beamforming for MISO interference channels with QoS and RF energy transfer. IEEE Trans Wireless Commun 13(5):2646–2658
Acknowledgments
This work is financially supported by the National Natural Science Foundation of China (NSFC) (Grant No. 61271188, Grant No. 61671072 and Grant No. 61401041), and the National High Technology Research and Development Program of China (863 Program) (Grant No. 2015AA01A706).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ren, Y., Gao, H. & Lv, T. Robust beamforming and artificial noise design in interference networks with wireless information and power transfer. Peer-to-Peer Netw. Appl. 10, 622–632 (2017). https://doi.org/10.1007/s12083-016-0509-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-016-0509-5