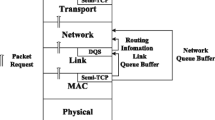
Abstract
In this paper, we study the problem of network utility maximization subject to QoS constraints in a wireless multi-hop network. Recently, virtual queues based cross-layer solution has been proposed to address this issue. Virtual queues can share the burden of the actual queues and also control the lengths of actual queues to ensure certain QoS constraints. In this paper, we introduce link reliability into the virtual queue models and optimization objective and accordingly present a fully distributed adaptive CSMA based flow rate control algorithm (AFCA) to achieve network utility maximization subject to QoS constraints. We analyze AFCA’s stability property and its near-optimality in network utility maximization while satisfying given QoS constraints. We reveal the relationship between various key parameters in AFCA and resulting network utility. Simulation results validate the effectiveness of our analytical results.






Similar content being viewed by others
Notes
In this paper, we assume that it is upper layer’s duty (e.g., transport layer or application layer) to recover those lost packets and we will touch how such packet recovery is realized in the rest of this paper.
References
Low SH, Lapsley DE (1999) Optimization Flow Control, I: Basic Algorithm and Convergence. IEEE/ACM Trans Networking 7(6):861–874
Chiang M, Low SH, Calderbank RA, Doyle JC (2007) Layering as optimization decomposition - A mathematical theory of network architectures. Proc IEEE 95(1):255–312
Lin X, Shroff NB, Srikant R (2008) On the connection-level stability of congestion-controlled communication networks. IEEE Trans Inf Theory 54(5):2317–2338
Li Y, Chiang M, Calderbank AR, Diggavi SN (2009) Optimal rate-reliability-delay tradeoff in networks with composite links. IEEE/ACM Trans Networking 57(5):1390–1401
Pongsajapan J, Low SH (2007) Reverse engineering TCP/IP-like networks using delay-sensitive utility functions. In: Proc. of IEEE INFOCOM’07. Anchorage, pp 418–426
Neely M (2011) Opportunistic scheduling with worst case delay guarantees in single and multi-hop networks. In: Proc. of IEEE INFOCOM’11. Shanghai, pp 1728–1736
Neely MJ, Modiano E, Rohrs CE (2005) Dynamic Power Allocation and Routing for time varing wireless networks. IEEE J Sel Areas Commun 23(1):98–103
Neely MJ, Modiano E, Li CP (2008) Fairness and optimal stochastic control for heterogeneous networks. IEEE/ACM Trans Networking 16(2):396–409
Wang X, Kar K (2006) Cross-layer rate optimization for proportional fairness in multihop wireless networks with random access. IEEE J Sel Areas Commun 24(8):1548–1559
Xue D, Ekici E (2013) Delay-guaranteed cross-Layer scheduling in multihop wireless networks. IEEE/ACM Trans Networking 21(6):1696–1707
Huynh T, Pham N, Lee S, Hwang W (2015) Dynamic Control Policy for Delay Guarantees in Multi-hop Wireless Networks. Wireless Personal Communications: An International Journal 80(2):647–670
Jiang L, Walrand J (2010) A Distributed CSMA Algorithm for Throughput and Utility Maximization in wireless networks. IEEE/ACM Trans Networking 18(3):960–972
Liew SC, Kai CH, Leung HC, Wong P (2010) Back-of-the-envelope computation of throughput distributions in CSMA wireless networks. IEEE Trans Mob Comput 9(9):1319–1331
Deng X, He L, Zhu C, Dong M, Ota K, Cai L (2016) QoS-Aware and Load-Balance Routing for IEEE 802.11s Based Neighborhood Area Network in Smart Grid. Wirel Pers Commun 89(4):1065–1088
Ota K, Dong M, Chen X, Liu A, Chen Z (2013) Cross layer optimal design for wireless sensor networks under rayleigh fast fading channels. In: Proc. of IEEE HPCC/EUC’13. Zhangjiajie, pp 183–189
Dong M, Ota K, Liu A, Guo M (2016) Joint Optimization of Lifetime and Transport Delay under Reliability Constraint Wireless Sensor Networks. IEEE Trans Parallel Distrib Syst 27(1):225–236
Li Y, Papachristodoulou A, Chiang M, Calderbank AR (2011) Congestion control and its stability in networks with delay sensitive traffic. Comput Netw 55:20–32
Giaccone P, Leonardi E, Shah D (2007) Throughput region of finite buffered networks. IEEE Trans Parallel Distrib Syst 18(2):251–263
Neely MJ (2006) Energy optimal control for time varying wireless networks. IEEE Trans Inf Theory 52(7):2915–2934
Le LB, Modiano E, Shroff NB (2010) Optimal control of wireless networks with finite buffers. In: Proc. of IEEE INFOCOM’10. San Diego, pp 1–9
Neely MJ (2013) Delay-based network utility maximization. IEEE/ACM Trans Networking 21(1):41–54
Bo J, Joo C, Shroff NB (2013) Delay-Based Back-Pressure Scheduling in Multihop Wireless Networks. IEEE/ACM Trans Networking 21(5):1539–1552
Xue D, Murawski R, Ekici E (2015) Capacity achieving distributed scheduling with finite buffers. IEEE/ACM Trans Networking 23(2):519–532
Ni J, Tan B, Srikant R (2012) Q-CSMA: Queue-Length-Based CSMA/CA Algorithms for Achieving Maximum Throughput and Low Delay in Wireless Networks. IEEE/ACM Trans Networking 20(3):825–836
Wang T, Yao Z, Zhang B, Li C (2017) Utility Bounds of Joint Congestion and Medium Access Control for CSMA based Wireless Networks. KSII Trans Internet Inf Syst 11(1):193–214
Kai C, Zhang S (2013) Throughput analysis of CSMA wireless networks with finite offered-load. In: Proc. of IEEE ICC’13. Budapest, pp 6101–6106
Swamy PS, Ganti RK, Jagannathan K (2015) Adaptive CSMA under the SINR model: Fast convergence through local gibbs optimization. In: Proc. 53rd Ann. Allerton Conf. Communication, Control, and Computing, Monticello
Yun S-Y, Shin J, Yi Y (2013) CSMA over time-varying channels: optimality, uniqueness and limited backoff rate. In: Proc. of ACM MobiHoc’13. New York, pp 137–146
Choi JG, Joo C, Zhang J, Shroff NB (2014) Distributed Link Scheduling Under SINR Model in multihop wireless networks. IEEE/ACM Trans Networking 22(4):1204–1217
Jang H, Yun SY, Shin J, Yi Y (2014) Distributed learning for utility maximization over CSMA-based wireless multihop networks. In: Proc. of IEEE INFOCOM’14. Toronto, pp 280–288
Karaca M, Landfeldt B (2016) Approaching Optimal Centralized Scheduling with CSMA-Based Random Access over Fading Channels. IEEE Commun Lett 20(6):1183–1186
Kelly FP (1979) Reversibility and Stochastic Networks. Wiley, New York
Acknowledgments
This work was supported partially by the National Natural Science Foundation of China under grants 61471339, 61531006, 61173158, and the Natural Sciences and Engineering Research Council (NSERC) of Canada (Discovery Grant 293264-12 and Strategic Project Grant STPGP 397491-10).
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
1.1 Proof of Proposition 1
Proof: According to (3), expanding the first term in (4), and transforming the obtained expression to a form using common denominator, then we have the corresponding numerator becomes the following.
where λ σ = ∑(n, m)∣σ σ (n, m) λ (n, m), \( {\lambda}_{{\boldsymbol{\upsigma}}^{\mathbf{\prime}}}={\sum}_{\left(n,m\right)\mid {\boldsymbol{\upsigma}}^{\mathbf{\prime}}}{\sigma}_{\left(n,m\right)}{\lambda}_{\left(n,m\right)} \), \( {\lambda}_{\boldsymbol{\upsigma}}^{\ast }={\sum}_{\left(n,m\right)\mid \boldsymbol{\upsigma}}{\sigma}_{\left(n,m\right)}{\lambda}_{\left(n,m\right)}^{\ast } \), and \( {\lambda}_{{\boldsymbol{\upsigma}}^{\mathbf{\prime}}}^{\ast }={\sum}_{\left(n,m\right)\mid {\boldsymbol{\upsigma}}^{\mathbf{\prime}}}{\sigma}_{\left(n,m\right)}{\lambda}_{\left(n,m\right)}^{\ast } \).
Regarding the second term in (4), we use the same way of transformation as above, and obtain a corresponding numerator as follows.
Since both of the above transforms share the same denominator, we add the two numerators (34) and (35) together, and yield
Since \( {\lambda}_{\boldsymbol{\upsigma}}+{\lambda}_{{\boldsymbol{\upsigma}}^{\mathbf{\prime}}}^{\ast } \) is positively correlated to \( \exp \left({\lambda}_{\boldsymbol{\upsigma}}+{\lambda}_{{\boldsymbol{\upsigma}}^{\mathbf{\prime}}}^{\ast}\right) \), we have the first term in (36) is larger than or equal to the second term. So (4) is proved.
1.2 Proof of Proposition 2
Proof: First, we prove that the queue length of source node s(c), ∀c∈C, has upper bound. Second, we prove that the queue length of s(c)‘s next hop node on the path for a session c∈C has upper bound.
First, we prove that, for a session c∈C, \( {Q}_{s(c)}^c(t)\le {q}_M \), ∀t.
Since \( {Q}_{s(c)}^c(0)=0 \), we have \( {Q}_{s(c)}^c(0)\le {q}_M \) when t = 0.
Suppose \( {Q}_{s(c)}^c(t)\le {q}_M \) (t > 0), we need to prove that \( {Q}_{s(c)}^c\left(t+1\right)\le {q}_M \).
There are two cases regarding this.
-
1)
If \( {Q}_{s(c)}^c(t)\le {q}_M-T \) in scheduling cycle t, we can easily obtain that \( {Q}_{s(c)}^c\left(t+1\right)\le {q}_M \) since \( {s}_{\left(s,s\right)}^c(t)\le T \),
-
2)
Else if \( {q}_M-T<{Q}_{s(c)}^c(t)\le {q}_M \), then we have (30a) < 0, which means that \( {s}_{\left(s,s\right)}^c(t)=0 \). Accordingly, we still have \( {Q}_{s(c)}^c\left(t+1\right)\le {q}_M \).
Thus, we have \( {Q}_{s(c)}^c(t)\le {q}_M \), ∀t.
Second, we prove that the queue length of s(c)‘s next-hop on the route of session c, denoted by node m, has upper bound. Here, to ease the presentation, we let n = s(c).
Next, we proceed to prove that \( {Q}_m^c(t)\le {q}_M/{\mathrm{Pr}}_{\left(n,m\right)}+T,\forall t \). The reason why such an upper bound holds at node m (i.e., source node’s next hop) will also be provided in the proof shown below. Let q M ′ = q M /Pr(n, m) + T.
It is obviously \( {Q}_m^c(0)=0 \) when t = 0. Thus, \( {Q}_m^c(0)\le {q_M}^{\prime } \).
Suppose \( {Q}_m^c(t)\le {q_M}^{\prime } \) (when t > 0) holds, we need to prove that \( {Q}_m^c\left(t+1\right)\le {q_M}^{\prime } \).
If \( {Q}_m^c(t)<{q}_M/{\mathrm{Pr}}_{\left(n,m\right)} \), we have (30b) > 0. That is, link (n,m) may have successful transmission scheduling (i.e., 0≤ \( {s}_{\left(n,m\right)}^c(t)+{d}_{\left(n,m\right)}^c(t)\le T \)). Then, in this case, we have \( {Q}_m^c\left(t+1\right)={Q}_m^c(t)+{s}_{\left(n,m\right)}^c(t)<{q}_M/{\mathrm{Pr}}_{\left(n,m\right)}+T={q_M}^{\prime } \).
If \( {q}_M/{\mathrm{Pr}}_{\left(n,m\right)}\le {Q}_m^c(t)\le {q}_M/{\mathrm{Pr}}_{\left(n,m\right)}+T \), we have (30b) < 0. Accordingly, the link (n, m) has no chance to be scheduled (i.e., \( {s}_{\left(n,m\right)}^c(t)+{d}_{\left(n,m\right)}^c(t)=0 \)). Then, we still have \( {Q}_m^c\left(t+1\right)={Q}_m^c(t)+{s}_{\left(n,m\right)}^c(t)\le {q}_M/{\mathrm{Pr}}_{\left(n,m\right)}+T={q_M}^{\prime } \).
Thus, we have we prove that \( {Q}_m^c(t)\le {q}_M/{\mathrm{Pr}}_{\left(n,m\right)}+T,\forall t \).
In this way, we can recursively prove that the queue lengths of all downstream nodes on the path of a session is upper bounded. In addition, it is seen that the actual upper bounds of queue lengths at different nodes on a path for a session can be different.
Based on the above steps, (31) follows.
1.3 Proof of Proposition 3
Before analyzing the stability and near-optimality of the AFCA algorithm, we first give the following a lemma.
Lemma 2: By the AFCA algorithm, the transmission scheduling function (27) satisfies the following condition:
where \( \varDelta (t)=E\left\{\sum_{\left(n,m\right)}{w}_{\left(n,m\right)}^{\max, \ast }(t)\left({\overline{\sigma}}_{\left(n,m\right)}(t)-{\overline{\sigma}}_{\left(n,m\right)}^{\ast }(t)\right)\left|\mathbf{Y}(t)\right.\right\} \).
Proof: According to Proposition 1, the transmission scheduling by (29) and (30) is used to maximize Ω AFCA (t), we have
Substituting the corresponding items in the above expression by (25c), we have,
where \( {s}_{s,s}^{c,\ast }(t) \), \( {s}_{\left(n,m\right)}^{c,\ast }(t) \) and \( {d}_{\left(n,m\right)}^{c,\ast }(t) \), respectively, denote the values of their counterparts when the link scheduling vector picks a near-optimal vector \( {\overline{\boldsymbol{\upsigma}}}^{\ast } \).
Rearranging the right side of the above expression, we have,
According to Lemma 1 in Section 4.3, we have,
According to the characteristics of near-optimal solution as we discussed in Section 4.3, (37) follows.
In the flow rate control by AFCA algorithm, (28) maximizes the term \( {\varPsi}_{AFCA}^c(t) \) over all feasible values of R c(t). Thus, we have the following inequality.
Substituting the corresponding items in (24) by (26), (37) and (38), respectively, we have,
where B M ′ = B M + ∑ c τT 2 + ∑ c ρ c τL max q max.
Given the two conditions in Proposition 3, we have
Summing over all cycles in {0, 1, 2, …, M −1}, we have
Taking the limit sup as M→+∞, (32) is proved.
The (32) means that the AFCA algorithm can achieve stable state, which means that \( {\sum}_{t=0}^{M-1}\varDelta (t) \) will approach a finite value. Thus, for (33), since the utility function φ c (⋅) is strictly concave, using the Jensen’s inequality, we have,
According to the definition of r in (14) and the characteristics of network capacity region as we discussed in Section 4.2, (33) is proved.
Rights and permissions
About this article
Cite this article
Wang, T., Yao, Z., Zhang, B. et al. Adaptive Flow Rate Control for Network Utility Maximization Subject to QoS Constraints in Wireless Multi-hop Networks. Peer-to-Peer Netw. Appl. 11, 881–899 (2018). https://doi.org/10.1007/s12083-017-0594-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-017-0594-0