Abstract
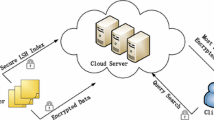
k-nearest neighbor (k-NN) query is widely applied to various networks, such as mobile Internet, peer-to-peer (P2P) network, urban road networks, and so on. The location-based service in the outsourced environment has become a research hotspot with the rise of cloud computing. Meanwhile, various privacy issues have been increasingly prominent. We propose an efficient privacy-preserving query protocol to accomplish the k-nearest neighbor (k-NN) query processing on outsourced data. We adopt the Moore curve to transform the spatial data into one-dimensional sequence and utilize the AES to encrypt the original data. According to the cryptographic transformation, the proposed protocol can minimize the communication overhead to achieve efficient k-NN query while protecting the spatial data and location privacy. Furthermore, the proposed efficient scheme offers considerable performance with privacy preservation. Experiments show that the proposed scheme achieves high accuracy and efficiency while preserving the data and location privacy when compared with the existing related approach.








Similar content being viewed by others
References
Xu G, Li H, Ren H, Yang K, Deng RH (2019) Data security issues in deep learning: attacks, countermeasures, and opportunities. IEEE Commun Mag 57(11):116–122
Li H, Liu D, Dai Y, Luan TH, Yu S (2015) Personalized search over encrypted data with efficient and secure updates in mobile clouds. IEEE Trans Emerg Top Comput 6(1):97–109
Gentry C (2009) Fully homomorphic encryption using ideal lattices. In: Proceedings of the forty-first annual ACM symposium on Theory of computing, pp. 169-178
Van Dijk M, Gentry C, Halevi S, Vaikuntanathan V (2010) Fully homomorphic encryption over the integers. In: Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 24-43. Springer
Smart NP, Vercauteren F (2010) Fully homomorphic encryption with relatively small key and ciphertext sizes. In: International Workshop on Public Key Cryptography, pp. 420-443. Springer
Gentry C, Halevi S (2011) Implementing gentry’s fully-homomorphic encryption scheme. In: Annual international conference on the theory and applications of cryptographic techniques, pp. 129-148. Springer
Brakerski Z, Gentry C, Vaikuntanathan V (2014) (Leveled) fully homomorphic encryption without bootstrapping. ACM Transac Comput Theor (TOCT) 6(3):1–36
Halevi S, Shoup V (2014) Algorithms in helib. In: Annual Cryptology Conference, pp. 554-571. Springer
Halevi S, Shoup V (2018) Faster homomorphic linear transformations in HElib. In: Annual International Cryptology Conference, pp. 93-120. Springer
Lawder JK, King PJH (2001) Querying multi-dimensional data indexed using the Hilbert space-filling curve. ACM SIGMOD Rec 30(1):19–24
Khoshgozaran A, Shahabi C (2007) Blind evaluation of nearest neighbor queries using space transformation to preserve location privacy. In: International Symposium on Spatial and Temporal Databases, pp. 239-257. Springer
Ku W-S, Hu L, Shahabi C, Wang H (2013) A query integrity assurance scheme for accessing outsourced spatial databases. Geoinformatica 17(1):97–124
Tian F, Gui X, Yang P, Zhang X, Yang J (2013) Security analysis for hilbert curve based spatial data privacy-preserving method. In: 2013 IEEE 10th International Conference on High Performance Computing and Communications & 2013 IEEE International Conference on Embedded and Ubiquitous Computing, pp. 929-934. IEEE
Wang P, Ravishankar CV (2013) Secure and efficient range queries on outsourced databases using Rp-trees. In: 2013 IEEE 29th International Conference on Data Engineering (ICDE), pp. 314-325. IEEE
Kim H-I, Hong S, Chang J-W (2016) Hilbert curve-based cryptographic transformation scheme for spatial query processing on outsourced private data. Data Knowl Eng 104:32–44
Paulet R, Kaosar MG, Yi X, Bertino E (2013) Privacy-preserving and content-protecting location based queries. IEEE Trans Knowl Data Eng 26(5):1200–1210
Shao J, Lu R, Lin X (2014) FINE: A fine-grained privacy-preserving location-based service framework for mobile devices. In: IEEE INFOCOM 2014-IEEE Conference on Computer Communications, pp. 244-252. IEEE
Yi X, Paulet R, Bertino E, Varadharajan V (2016) Practical approximate k nearest neighbor queries with location and query privacy. IEEE Trans Knowl Data Eng 28(6):1546–1559
Sweeney L (2002) k-anonymity: A model for protecting privacy. Int J Uncert, Fuzz Knowl-Based Syst 10(05):557–570
Mokbel MF, Chow C-Y, Aref WG (2006) The new casper: Query processing for location services without compromising privacy. In: Proceedings of the 32nd international conference on Very large data bases, pp. 763–774
Lee H, Oh B-S, Kim, H-I, Chang J (2012) Grid-based cloaking area creation scheme supporting continuous location-based services. In: Proceedings of the 27th Annual ACM Symposium on Applied Computing, pp. 537–543
Kim H-I, Chang J-W (2012) A grid-based cloaking scheme for continuous location-based services in distributed systems. In: Computer Science and its Applications. pp. 69–78. Springer
Yiu ML, Jensen CS, Huang X, Lu H (2008) Spacetwist: Managing the trade-offs among location privacy, query performance, and query accuracy in mobile services. In: 2008 IEEE 24th International Conference on Data Engineering, pp. 366-375. IEEE
Ghinita G, Kalnis P, Kantarcioglu M, Bertino E (2011) Approximate and exact hybrid algorithms for private nearest-neighbor queries with database protection. GeoInformatica 15(4):699–726
Um J-H, Kim H-D, Chang J-W (2010) An advanced cloaking algorithm using Hilbert curves for anonymous location based service. In: 2010 IEEE second international conference on social computing, pp. 1093-1098. IEEE
Ni W-W, Zheng J-W, Chong Z-H (2012) HilAnchor: location privacy protection in the presence of users’ preferences. J Comput Sci Technol 27(2):413–427
Liu K, Kargupta H, Ryan J (2005) Random projection-based multiplicative data perturbation for privacy preserving distributed data mining. IEEE Trans Knowl Data Eng 18(1):92–106
Yiu ML, Ghinita G, Jensen CS, Kalnis P (2010) Enabling search services on outsourced private spatial data. VLDB J 19(3):363–384
Hossain AA, Lee S-J, Huh E-N (2013) Shear-based spatial transformation to protect proximity attack in outsourced database. In: 2013 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, pp. 1633-1638. IEEE
Wong WK, Cheung DW-L, Kao B, Mamoulis N (2009) Secure kNN computation on encrypted databases. In: Proceedings of the 2009 ACM SIGMOD International Conference on Management of data, pp. 139–152
Narayanan A, Thiagarajan N, Lakhani M, Hamburg M, Boneh D (2011) Location privacy via private proximity testing. In: NDSS
Yiu ML, Assent I, Jensen CS, Kalnis P (2010) Outsourced similarity search on metric data assets. IEEE Trans Knowl Data Eng 24(2):338–352
Puttaswamy KP, Wang S, Steinbauer T, Agrawal D, El Abbadi A, Kruegel C, Zhao BY (2012) Preserving location privacy in geosocial applications. IEEE Trans Mob Comput 13(1):159–173
Lien I-T, Lin Y-H, Shieh J-R, Wu J-L (2013) A novel privacy preserving location-based service protocol with secret circular shift for k-nn search. IEEE Transac Inform Forensics Sec 8(6):863–873
Utsunomiya Y, Toyoda K, Sasase I (2016) LPCQP: lightweight private circular query protocol with divided POI-table and somewhat homomorphic encryption for privacy-preserving k-NN search. J Inform Process 24(1):109–122
Sagan H (2012) Space-filling curves. Springer Science & Business Media
Moon B, Jagadish HV, Faloutsos C, Saltz JH (2001) Analysis of the clustering properties of the Hilbert space-filling curve. IEEE Trans Knowl Data Eng 13(1):124–141
Jagadish HV (1990) Linear clustering of objects with multiple attributes. In: Proceedings of the 1990 ACM SIGMOD international conference on Management of data, pp. 332–342
Xu G, Li H, Dai Y, Yang K, Lin X (2018) Enabling efficient and geometric range query with access control over encrypted spatial data. IEEE Transac Inform Forensics Sec 14(4):870–885
Ren H, Li H, Dai Y, Yang K, Lin X (2018) Querying in internet of things with privacy preserving: challenges, solutions and opportunities. IEEE Netw 32(6):144–151
Acknowledgments
This work was supported by the National Key Research and Development Program of China under Grant 2017YFB0802704, 2017YFB0802202, and the National Natural Science Foundation of China under Grand 61972249.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection: Special Issue on Security and Privacy in Machine Learning Assisted P2P Networks
Guest Editors: Hongwei Li, Rongxing Lu and Mohamed Mahmoud
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Lian, H., Qiu, W., Yan, D. et al. Efficient and secure k-nearest neighbor query on outsourced data. Peer-to-Peer Netw. Appl. 13, 2324–2333 (2020). https://doi.org/10.1007/s12083-020-00909-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-020-00909-2