Abstract
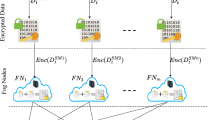
Smart agriculture Internet of Things (IoT) is a typical application of IoT and has become popular due to its advantages in automatic irrigation and fertilization, crop growth monitoring, pest and disease detection, etc. To reduce resource waste, minimize environmental impact, and maximize crop yield, most smart agricultural applications require to collect and process agricultural data in real-time. However, the computational and storage resources of the agricultural IoT devices are limited. To alleviate the computational and storage pressure on agriculture IoT devices and timely process the collected data collected by IoT devices, the fog node is usually placed at the edge of the agricultural IoT. Nevertheless, the fog node may not be completely trusted. The agricultural IoT devices’ data stored in the fog node will face the potential risk of privacy leakage. In this paper, to preserve the privacy of agricultural IoT devices’ data and user query’s result in the fog-based smart agriculture IoT, we first build the K2-treap, which is used for storing the data collected by agriculture IoT devices and support efficient range-max query and dynamic update of the data. Then, we design a data encryption and comparison algorithm based on BGN homomorphic encryption technique and present an efficient and privacy-preserving range-max query in the fog-based smart agriculture IoT, which can not only securely compare two data based on their ciphertexts but also support the incremental update directly over ciphertexts. Notably, our comparison technique and range-max queries are run by the fog node, so there are no interactions between the agricultural IoT devices and the fog node during the comparison and query. Finally, we conduct a detailed security analysis and performance evaluation. The results show that our proposed scheme can indeed protect the privacy of the agricultural IoT devices’ data and query results, and the experimental test results prove that our proposed scheme is efficient.






Similar content being viewed by others
References
Vasisht D, Kapetanovic Z, Won J, Jin X, Chandra R, Sinha SN, Kapoor A, Sudarshan M, Stratman S (2017) Farmbeats: An iot platform for data-driven agriculture. In: 14th USENIX Symposium on networked systems design and implementation, NSDI 2017, Boston, MA, USA, March 27-29, 2017, pp 515–529
Kamilaris A, Gao F, Prenafeta-Boldu FX, Ali MI (2016) Agri-iot: A semantic framework for internet of things-enabled smart farming applications. In: 3rd IEEE World Forum on internet of things, WF-IoT 2016, Reston, VA, USA, December 12-14, 2016, pp 442–447
Bonomi F, Milito RA, Zhu J, Addepalli S (2012) Fog computing and its role in the internet of things. In: Proceedings of the first edition of the MCC workshop on Mobile cloud computing, MCC@SIGCOMM 2012, Helsinki, Finland, August 17, 2012, pp. 13–16
Bonomi F, Milito RA, Natarajan P, Zhu J (2014) Fog computing: A platform for internet of things and analytics. In: Big data and internet of things: A roadmap for smart environments, studies in computational intelligence, vol 546, pp 169–186
Chiang M, Zhang T (2016) Fog and iot: An overview of research opportunities. IEEE Int Things J 3(6):854–864
Dastjerdi AV, Buyya R (2016) Fog computing: Helping the internet of things realize its potential. IEEE Comput 49(8):112–116
Aazam M, Zeadally S, Harras KA (2018) Fog computing architecture, evaluation, and future research directions. IEEE Commun Mag 56(5):46–52
Yan Q, Yang H, Vuran MC, Irmak S (2017) SPRIDE: Scalable and private continual geo-distance evaluation for precision agriculture. In: 2017 IEEE Conference on communications and network security, CNS 2017, Las Vegas, NV, USA, October 9-11, 2017, pp 1–9
Huang C, Liu D, Ni J, Lu R, Shen X (2018) Reliable and privacy-preserving selective data aggregation for fog-based iot. In: 2018 IEEE International conference on communications, ICC 2018, Kansas City, MO, USA, May 20-24, 2018, pp 1–6
Lin X, Ni J, Shen XS (2018) Privacy-enhancing fog computing and its applications springer briefs in electrical and computer engineering
Xue L, Liu D, Huang C, Lin X, Shen XS (2020) Secure and privacy-preserving decision tree classification with lower complexity. J Commun Inf Networks 5(1):16–25
Shi X, An X, Zhao Q, Liu H, Xia L, Sun X, Guo Y (2019) State-of-the-art internet of things in protected agriculture. Sensors 19(8):1833
Ferrag MA, Shu L, Yang X, Derhab A, Maglaras LA (2020) Security and privacy for green iot-based agriculture: Review, blockchain solutions, and challenges. IEEE Access 8:32031–32053
Gupta M, Abdelsalam M, Khorsandroo S, Mittal S (2020) Security and privacy in smart farming: Challenges and opportunities. IEEE Access 8:34564–34584
Chen L, Lu R, Cao Z, Alharbi K, Lin X (2015) Muda: Multifunctional data aggregation in privacy-preserving smart grid communications. Peer Peer Netw Appl 8(5):777–792
Chen L, Lu R, Cao Z (2015) PDAFT: A privacy-preserving data aggregation scheme with fault tolerance for smart grid communications. Peer Peer Netw Appl 8(6):1122–1132
Ge S, Zeng P, Lu R, Choo KR (2018) FGDA: Fine-grained data analysis in privacy-preserving smart grid communications. Peer Peer Netw Appl 11(5):966–978
Zheng Y, Lu R, Li B, Shao J, Yang H, Choo KR (2019) Efficient privacy-preserving data merging and skyline computation over multi-source encrypted data. Inf Sci 498:91–105
Zheng Y, Lu R, Shao J (2019) Achieving efficient and privacy-preserving k-nn query for outsourced ehealthcare data. J Medical Syst 43(5):123:1–123:13
Yao Y, Xiong N, Park JH, Ma L, Liu J (2013) Privacy-preserving max/min query in two-tiered wireless sensor networks. Comput Math Appl 65(9):1318–1325
Samanthula BK, Jiang W, Madria S (2013) A probabilistic encryption based MIN/MAX computation in wireless sensor networks. In: 2013 IEEE 14th International conference on mobile data management, Milan, Italy, June 3-6, 2013 - Volume 1, pp 77–86
Dai H, Ji Y, Xiao F, Yang G, Yi X, Chen L (2019) Privacy-preserving MAX/MIN query processing for WSN -as-a -service. In: 2019 IFIP networking conference, networking 2019, Warsaw, Poland, May 20-22, 2019, pp 1–9
Agrawal R, Kiernan J, Srikant R, Xu Y (2004) Order-preserving encryption for numeric data. In: Proceedings of the ACM SIGMOD International Conference on Management of Data, Paris, France, June 13-18, 2004, pp 563–574
Boldyreva A, Chenette N, Lee Y, O’Neill A (2009) Order-preserving symmetric encryption. In: Advances in Cryptology - EUROCRYPT 2009, 28th Annual international conference on the theory and applications of cryptographic techniques, Cologne, Germany, April 26-30, 2009. Proceedings, Lecture Notes in Computer Science, vol. 5479, pp 224–241
Lu R (2019) A new communication-efficient privacy-preserving range query scheme in fog-enhanced iot. IEEE Int Things J 6(2):2497–2505
Mahdikhani H, Lu R, Zheng Y, Shao J, Ghorbani AA (2020) Achieving o(log3n) communication-efficient privacy-preserving range query in fog-based iot. IEEE Int Things J 7 (6):5220–5232
Boneh D, Goh E, Nissim K (2005) Evaluating 2-dnf formulas on ciphertexts. In: Theory of cryptography, second theory of cryptography conference, TCC 2005, Cambridge, MA, USA, February 10-12, 2005, Proceedings, Lecture Notes in Computer Science, vol. 3378, pp 325–341
Lu R (2016) Privacy-Enhancing Aggregation Techniques for Smart Grid Communications Wireless Networks
Menezes A, van Oorschot PC, Vanstone SA (1996) Handbook of applied cryptography
Acknowledgements
This work was supported by the China Scholarship Council when Min Zhou was visiting the University of New Brunswick, Canada. This work was also supported in part by the National Natural Science Foundation of China (No. 61872152, 61872409, 61902132), the Natural Science Foundation of Guangdong Province (No. 2018A03 0310147), Guangdong Basic and Applied Basic Research Foundation (No. 2019B030302008, No. 2020A1515010751), Science and Technology Program of Guangzhou (No.201902010081), Guangzhou Key Laboratory of Intelligent Agriculture.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhou, M., Zheng, Y., Guan, Y. et al. Efficient and privacy-preserving range-max query in fog-based agricultural IoT. Peer-to-Peer Netw. Appl. 14, 2156–2170 (2021). https://doi.org/10.1007/s12083-021-01179-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-021-01179-2