Abstract
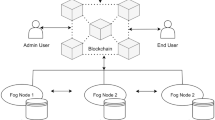
Currently, more and more intellectual property (IP) applications, including blockchain-based platforms, are presented to protect personal intellectual achievement. However, these applications are independent of each other, and the user’s identity information is controlled by an organization, which may not only reveal the user’s identity information due to the single point of failure, but also add extra communication overhead when the user accesses other applications. Additionally, current research focuses on the user’s control over their information, while the IP field requires tracing the user’s identity information in the event of IP dispute. In this paper, we propose a blockchain-based privacy-preserving and traceability identity management scheme for IP, where the user’s identity information is private and traceable. Our proposed scheme lets users generate their identity (ID) and corresponding public keys and private keys. Key pairs are used for authentication when accessing the services. We use blockchain to record ID and public key of the legitimate user, and adopt improved-Shamir secret sharing to achieve privacy-preserving and traceability of real identity information and reduce storage overhead. Experimental results confirm that our proposed scheme can protect user’s privacy and effectively reduce storage and computation overhead.







Similar content being viewed by others
References
Zhang Y, Yu J, Hao R et al (2018) Enabling efficient user revocation in identity-based cloud storage auditing for shared big data. IEEE Trans Dependable Secure Comput 17(3):608–619
Goodell G, Aste T (2019) A decentralized digital identity architecture. Frontiers in Blockchain 2:17
Othman A, Callahan J (2018) The Horcrux protocol: a method for decentralized biometric-based self-sovereign identity[C]//2018 international joint conference on neural networks (IJCNN). IEEE 1–7
Nofer M, Gomber P, Hinz O et al (2017) Blockchain. Bus Inf Syst Eng 59(3):183–187
Zheng Z, Xie S, Dai HN et al (2018) Blockchain challenges and opportunities: a survey. Int J Web Grid Serv 14(4):352–375
Francisco K, Swanson D (2018) The supply chain has no clothes: Technology adoption of blockchain for supply chain transparency. Logistics 2(1):2
Saberi S, Kouhizadeh M, Sarkis J et al (2019) Blockchain technology and its relationships to sustainable supply chain management. Int J Prod Res 57(7):2117–2135
Yu KP, Tan L, Aloqaily M et al (2021) Blockchain-enhanced data sharing with traceable and direct revocation in IIoT. IEEE Trans Ind Inform
Wang W, Xu H, Alazab M et al (2021) Blockchain-Based Reliable and Efficient Certificateless Signature for IIoT Devices. IEEE Trans Ind Inform
Cai X, Geng S, Zhang J et al (2021) A sharding scheme based many-objective optimization algorithm for enhancing security in blockchain-enabled industrial internet of things. IEEE Trans Ind Inform
Yaqoob I, Salah K, Jayaraman R et al (2021) Blockchain for healthcare data management: Opportunities, challenges, and future recommendations. Neural Comput App 1–16
Ekblaw A, Azaria A, Halamka JD et al (2016) A case study for blockchain in healthcare: MedRec prototype for electronic health records and medical research data. Proc IEEE Open Big Data Conf 13:13
Jacobovitz O (2016) Blockchain for identity management. The Lynne and William Frankel Center for Computer Science Department of Computer Science. Ben-Gurion University, Beer Sheva
Gao Z, Xu L, Turner G et al (2018) Blockchain-based identity management with mobile device. Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems 66–70
Liu Y, He D, Obaidat MS et al (2020) Blockchain-based identity management systems: a review. J Netw Computer App 166:102731
Hammi MT, Hammi B, Bellot P et al (2018) Bubbles of trust: a decentralized blockchain-based authentication system for IoT. Comput Secur 78:126–142
Shamir A (1979) How to share a secret. Commun ACM 22(11):612–613
Chen H, Wu HL, Chang CC et al (2019) Light repository blockchain system with multisecret sharing for industrial big data. Secur Commun Netw 2019
Xue K et al (2019) A secure, efficient, and accountable edge-based access control framework for information centric networks. IEEE/ACM Trans Netw 27(3):1220–1233
Wu F, Li X, Sangaiah A et al (2017) A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Futur Gener Comput Syst 82:9
Liu Z, Liu Z, Zhang L, Lin X (2020) MARP: a distributed mac layer attack resistant pseudonym scheme for VANET. IEEE Trans Dependable Secure Comput 17(4):869–882
Premarathne U, Khalil I, Tari Z, Zomaya A (2015) Cloud-based utility service framework for trust negotiations using federated identity management. IEEE Trans Cloud Comput 5(2):290–302
Bendiab G, Shiaeles S, Boucherkha S et al (2019) FCMDT: a novel fuzzy cognitive maps dynamic trust model for cloud federated identity management. Comput Secur 86:270–290
Selvanathan N, Jayakody D, Damjanovic-Behrendt V (2019) Federated identity management and interoperability for heterogeneous cloud platform ecosystems. Proceedings of the 14th International Conference on Availability, Reliability and Security 1–7
Basney J, Flanagan H, Fleury T et al (2019) CILogon: Enabling federated identity and access management for scientific collaborations. Proc Sci 351:031
Lenz T, Krnjic V (2018) Towards domain-specific and privacy-preserving qualified eID in a user-centric identity model. 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE). IEEE 1157–1163
Beltran V, Martinez JA, Skarmeta AF (2017) User-centric access control for efficient security in smart cities. 2017 Global Internet of Things Summit (GIoTS). IEEE 1–6
Dash P, Rabensteiner C, Hörandner F et al (2017) Towards privacy-preserving and user-centric identity management as a service. Open Identity Summit 2017
Laborde R, Oglaza A, Wazan S et al (2020) A user-centric identity management framework based on the W3C verifiable credentials and the FIDO universal authentication framework. 2020 IEEE 17th Annual Consumer Communications & Networking Conference (CCNC). IEEE 1–8
Singh BC, Carminati B, Ferrari E (2019) Privacy-aware personal data storage (p-pds): Learning how to protect user privacy from external applications. IEEE Trans Dependable Secur Comput
Ruffing T, Moreno-Sanchez P, Kate A (2014) Coinshuffle: Practical decentralized coin mixing for bitcoin. European Symposium on Research in Computer Security. Springer, Cham, pp 345–364
Ruffing T, Moreno-Sanchez P, Kate A (2017) P2P mixing and unlinkable bitcoin transactions. NDSS 1–15
Ziyu W, Jianwei L, Zongyang Z et al (2018) Full anonymous blockchain based on aggregate signature and confidential transaction. J Comput Res Dev 55(10):2185
Saxena A, Misra J, Dhar A (2014) Increasing anonymity in bitcoin. International Conference on Financial Cryptography and Data Security. Springer, Berlin, Heidelberg, pp 122–139
Xu J, Xue K, Tian H et al (2020) An identity management and authentication scheme based on redactable blockchain for mobile networks. IEEE Trans Veh Technol 69(6):6688–6698
Gao S, Su Q, Zhang R et al (2021) A privacy-preserving identity authentication scheme based on the blockchain. Secur Commun Netw 2021
Faber B, Michelet GC, Weidmann N et al (2019) BPDIMS: a blockchain-based personal data and identity management system
ElGayyar MM, ElYamany HF, Grolinger K et al (2020) Blockchain-based federated identity and auditing. Int J Blockchains Cryptocurrencies 1(2):179–205
Rathor S, Agrawal A (2020) A robust verification system for recruitment process by using blockchain technology. Int J Blockchains Cryptocurrencies 1(4):389–399
He D, Zeadally S, Xu B et al (2015) An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans Inf Forensics Secur 10(12):2681–2691
Chang CC, Tsai HC (2010) An anonymous and self-verified mobile authentication with authenticated key agreement for large-scale wireless networks. IEEE Trans Wireless Commun 9(11):3346–3353
Cui Z, Fei XUE, Zhang S et al (2020) A hybrid blockchain-based identity authentication scheme for multi-WSN. IEEE Trans Serv Comput 13(2):241–251
Almadhoun R, Kadadha M, Alhemeiri M et al (2018) A user authentication scheme of IoT devices using blockchain-enabled fog nodes. 2018 IEEE/ACS 15th International Conference on Computer Systems and Applications (AICCSA). IEEE 1–8
Khan S, Jadhav A, Bharadwaj I et al (2020) Blockchain and the identity based encryption scheme for high data security. 2020 Fourth International Conference on Computing Methodologies and Communication (ICCMC). IEEE 1005–1008
Ito T, Kotani D, Okabe Y (2017) A threshold-based authentication system which provides attributes using secret sharing. 2017 IEEE 41st Annual Computer Software and Applications Conference (COMPSAC). IEEE 2:730–737
Liu Y, Cheng ZY, Chang CC et al (2012) A secure dynamic identity based remote user authentication scheme using secret sharing. J Internet Technol 13(3):463–470
Acknowledgements
This work is supported by the Joint Fund of the National Natural Science Foundation of China and Guangdong Province (No. U1701266), and Key Laboratory Project of Intellectual Property Big Data in Guangdong Province (No. 2018B030322016).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have no conflicts of interest to declare that are relevant to the content of this article.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhuang, C., Dai, Q. & Zhang, Y. BCPPT: A blockchain-based privacy-preserving and traceability identity management scheme for intellectual property. Peer-to-Peer Netw. Appl. 15, 724–738 (2022). https://doi.org/10.1007/s12083-021-01277-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-021-01277-1