Abstract
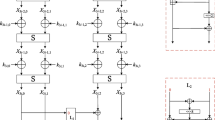
In a (t, n) secret sharing scheme, cheating identification provides a very effective way to protect the security of the secret. In this paper, we propose a fair multi-secret deception identification sharing scheme. The binary polynomials are used to generate k secrets and establish pairs of keys between groups, respectively. During the reconstruction phase, the attackers can be identified and eliminated in a black box by deception verification based on the characteristic equation of n-order matrix with multiple roots. Participants in our scheme cannot directly own useful information, only those who are verified as honest by the black box can get necessary values encrypted by the key, and then multi-secret can be reconstructed successfully. The analysis results show that our scheme can resist both external and internal attacks.
Similar content being viewed by others
References
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Blakley, G.R.: Safeguarding cryptographic keys. IEEE Computer Society, 313–317 (1979)
Chor, B., Goldwassser, S, Macalis, et al.: Verifiable secret sharing and achieving simultanrity in presence of fault. In: Proceeding of IEEE 26th Symposium on Foudation of Computer Science(FOCS), 383–395 (1985)
Liu, Y., Yang, C., Wang, Y., et al.: Cheating identifiable secret sharing scheme using symmetric bivariate polynomial. Inform. Sci., 453 (2018)
Harn, L.: Secure secret reconstruction and multi-secret sharing schemes with unconditional security. Secur. Commun. Netw. 7(3), 567–573 (2014)
Harn, L., Hsu, C.F.: (T,n) multi-secret sharing scheme based on bivariate polynomial. Wirel. Pers. Commun. 95(2), 1–10 (2017)
Harn, L., Lin, C., Li, Y.: Fair secret reconstruction in (t,n) secret sharing. J. Inf. Secur. Appl. 23, 1–7 (2015)
Tompa, M., Woll, H.: How to share a secret with cheaters. J. Cryptol. 1(3), 133–138 (1989)
Y Tian, J, Ma, C, et al.: Peng Fair (t,n) threshold secret sharing scheme. IET Inf. Secur. 7(2), 106–122 (2013)
William Gilbert Strang, G.S.: Introduction to Linear Algebra. Harper and Row (1963)
Peled, D., Vardi, Y., Yannakakis, M.: Black box checking. Formal Methods for Protocol Engineering and Distributed Systems Springer US (1999)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supported by the National Natural Science Foundation of China (No.61972168, No.U21A20428, No.12171134)
Appendix
Appendix
In this part, an example is used to simulate the secret reconstruction process (Table 1). (2,3) cheating identification multi-secret sharing scheme is adopted, where t = 2,n = 3, that is, we have U1,U2 two sets, where U1 = {P11,P12}, U2 = {P21}, n1 = |U1| = 2,n2 = |U2| = 1. The concrete steps are shown in the Table as follows:
Notation 1
A 6-order invertible matrix X generated by black box, like that:
We can obtain the matrix A,
\(=\left (\begin {array}{cccccc} 6&0&0&0&0&0\\ 0&6&0&0&0&0\\ 0&0&6&0&0&0\\ 0&0&0&9&0&0\\ 0&0&0&0&6&0\\ 0&2&0&0&0&9 \end {array} \right )\)
The eigenvalue ω1 = 6 of matrix A corresponds to four independent eigenvectors, denoted by
ω2 = 9 corresponds to two independently eigenvectors, denoted by
Rights and permissions
About this article
Cite this article
Li, F., Liu, Y., Yan, J. et al. A new fair multi-secret sharing scheme based on asymmetric bivariate polynomial. Cryptogr. Commun. 14, 1039–1053 (2022). https://doi.org/10.1007/s12095-022-00576-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12095-022-00576-5