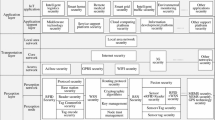
Abstract
As a typical application of Internet of Things (IoT) in the field of transportation, Internet of Vehicles (IoV) aims at achieving an integrated intelligent transportation system to enhance traffics efficiency, avoid accidents, ensure road safety, and improve driving experiences by using new IoT technologies. Different from other Internet, it is characterized by dynamic topological structures, huge network scale, non-uniform distribution of nodes, and mobile limitation. Due to these characteristics, IoV systems face various types of attacks, such as authentication and identification attacks, availability attacks, confidentiality attacks, routing attacks, data authenticity attacks, etc., which result in several challenging requirements in security and privacy. Many security scientists made numerous efforts to ensure the security and privacy for the Internet of Vehicles in recent years. This paper aims to review the advances on issues of security and privacy in IoV, including security and privacy requirements, attack types, and the relevant solutions, and discuss challenges and future trends in this area.






Similar content being viewed by others
References
Leng Y, Zhao L (2011) Novel design of intelligent internet-of-vehicles management system based on cloud-computing and internet-of-things. In: 2011 International Conference on Electronic and Mechanical Engineering and Information Technology (EMEIT), vol 6. IEEE, pp 3190–3193
Kolls HB (2003) Communicating interactive digital content between vehicles and internet based data processing resources for the purpose of transacting e-commerce or conducting e-business. uS Patent,6,615,186
Ahmed SH, Bouk SH, Yaqub MA, Kim D, Song H, Lloret J Codie: Controlled data and interest evaluation in vehicular named data networks
Wang J, Cho J, Lee S, Ma T (2011) Real time services for future cloud computing enabled vehicle networks. In: 2011 International Conference on Wireless Communications and Signal Processing (WCSP), pp 1–5
Lazarevic A, Srivastava J, Kumar V (2002) Cyber threat analysis–a key enabling technology for the objective force (a case study in network intrusion detection). In: 23rd Army Science Conference Proceedings of the IT/C4ISR
Yu L, Deng J, Brooks RR, Yun SB (2015) Automobile ecu design to avoid data tampering. In: Proceedings of the 10th Annual Cyber and Information Security Research Conference. ACM, p 10
Sicari S, Rizzardi A, Grieco L, Coen-Porisini A (2015) Security, privacy and trust in internet of things: the road ahead. Comput Netw 76:146–164
Singh R, Singh P, Duhan M (2014) An effective implementation of security based algorithmic approach in mobile adhoc networks. Human-centric Comput Inf Sci 4(1):1–14
Othmane LB, Weffers H, Mohamad MM, Wolf M (2015) A survey of security and privacy in connected vehicles. In: Wireless Sensor and Mobile Ad-Hoc Networks. Springer, pp 217–247
Yan G, Wen D, Olariu S, Weigle MC (2013) Security challenges in vehicular cloud computing. IEEE Trans Intell Transp Syst 14(1):284–294
Li W, Song H (2016) ART: An Attack-Resistant Trust Management Scheme for Securing Vehicular Ad Hoc Networks. IEEE Transactions on Intelligent Transportation Systems 17(4):960–969
Wang L, Kangasharju J (2013) Measuring large-scale distributed systems: case of bittorrent mainline dht. In: 2013 IEEE Thirteenth International Conference on Peer-to-Peer Computing (P2P). IEEE, pp 1–10
Bellare M, Rogaway P (1993) Random oracles are practical: a paradigm for designing efficient protocols. In: Proceedings of the 1st ACM Conference on Computer and Communications Security. ACM, pp 62–73
Aura T, Nikander P, Leiwo J (2001) Dos-resistant authentication with client puzzles. In: Security Protocols. Springer, pp 170–177
Burgess J, Gallagher B, Jensen D, Levine BN (2006) Maxprop: Routing for vehicle-based disruption-tolerant networks. In: INFOCOM, vol 6, pp 1–11
Mershad K, Artail H (2013) A framework for secure and efficient data acquisition in vehicular ad hoc networks. IEEE Trans Veh Technol 62(2):536–551
Marian S, Mircea P (2015) Sybil attack type detection in wireless sensor networks based on received signal strength indicator detection scheme. IEEE
Chen C-Y, Yein AD, Hsu T-C, Chiang JY, Hsieh W-S (2014) Secure access control method for wireless sensor networks
Wang X, Wong J (2007) An end-to-end detection of wormhole attack in wireless ad-hoc networks. In: 131st Annual International Conference on Computer Software and Applications 2007, COMPSAC 2007. IEEE, pp 39–48
Tun Z, Maw AH (2008) Wormhole attack detection in wireless sensor networks. World Acad Sci Eng Technol 46:2008
Ji S, Chen T, Zhong S (2015) Wormhole attack detection algorithms in wireless network coding systems. IEEE Trans Mob Comput 14(3):660–674
Shah N, Valiveti S (2012) Intrusion detection systems for the availability attacks in ad-hoc networks. Int J Electron Comput Sci Eng (IJECSE, ISSN: 2277-1956) 1(03):1850–1857
Shah V, Modi N (2014) Responsive parameter based an antiworm approach to prevent wormhole attack in ad hoc networks. Int J Netw Secur 5(1):1
Ko Y-B, Vaidya NH (2000) Location-aided routing (lar) in mobile ad hoc networks. Wirel Netw 6(4):307–321
Kannhavong B, Nakayama H, Nemoto Y, Kato N, Jamalipour A (2007) A survey of routing attacks in mobile ad hoc networks. IEEE Wirel Commun 14(5):85–91
Zargar ST, Joshi J, Tipper D (2013) A survey of defense mechanisms against distributed denial of service (ddos) flooding attacks. IEEE Commun Surv Tutorials 15(4):2046–2069
Wallgren L, Raza S, Voigt T (2013) Routing attacks and countermeasures in the rpl-based internet of things. Int J Distrib Sensor Netw 2013
Xia H, Jia Z, Li X, Ju L, Sha EH-M (2013) Trust prediction and trust-based source routing in mobile ad hoc networks. Ad Hoc Netw 11(7):2096–2114
Gite P, Thakur S (2015) An effective intrusion detection system for routing attacks in manet using machine learning technique. Int J Comput Appl 113(9)
Virmani D, Soni A, Chandel S, Hemrajani M (2014) Routing attacks in wireless sensor networks: A survey. arXiv:1407.3987
Pavani K, Damodaram A (2014) Anomaly detection system for routing attacks in mobile ad hoc networks, vol 6
Bakiler H, Safak A (2015) Analysis of current routing attacks in mobile ad hoc networks. Int J Appl Math, Electron Comput 3(2):127–132
Mejri MN, Ben-Othman J, Hamdi M (2014) Survey on vanet security challenges and possible cryptographic solutions. Veh Commun 1(2):53–66
Zhao M, Walker J, Wang C-C (2012) Security challenges for the intelligent transportation system. In: Proceedings of the First International Conference on Security of Internet of Things. ACM, pp 107–115
Rawat DB, Yan G, Bista B, Weigle MC (2014) Trust on the security of wireless vehicular ad-hoc networking
Ellison G, Lacy J, Maher D, Nagao Y, Poonegar A, Shamoon T (2012) The car as an internet-enabled device, or how to make trusted networked cars. In: Electric Vehicle Conference (IEVC), pp 1–8
Anwar RW, Bakhtiari M, Zainal A, Abdullah AH, Qureshi KN (2014) Security issues and attacks in wireless sensor network. World Appl Sci J 30(10):1224–1227
Al Ameen M, Liu J, Kwak K (2012) Security and privacy issues in wireless sensor networks for healthcare applications. J Med Syst 36(1):93–101
Qu F, Wu Z, Wang F-Y, Cho W (2015) A security and privacy review of vanets
Almeida J, Shintre S, Boban M, Barros J (2012) Probabilistic key distribution in vehicular networks with infrastructure support. In: 2012 IEEE Global Communications Conference (GLOBECOM). IEEE, pp 973–978
Aouzellag H, Ghedamsi K, Aouzellag D (2015) Energy management and fault tolerant control strategies for fuel cell/ultra-capacitor hybrid electric vehicles to enhance autonomy, efficiency and life time of the fuel cell system. Int J Hydrog Energy 40(22):7204–7213
MaliK V, Bishnoi S (2014) Security threats in vanets: A review
Serna-Olvera JM, Medina Llinás M., Luna Garcýa A. (2013) A trust-driven privacy architecture for vehicular ad-hoc networks
Qabajeh LK, Kiah MLM, Qabajeh MM (2009) A scalable and secure position-based routing protocols for ad-hoc networks. Malays J Comput Sci 22(2):99–120
Lindgren A, Doria A, Schelén O (2003) Probabilistic routing in intermittently connected networks. ACM SIGMOBILE Mob Comput Commun Rev 7(3):19–20
Balasubramanian A, Levine B, Venkataramani A (2007) Dtn routing as a resource allocation problem. ACM SIGCOMM Comput Commun Rev 37(4):373–384
Costa P, Mascolo C, Musolesi M, Picco GP (2008) Socially-aware routing for publish-subscribe in delay-tolerant mobile ad hoc networks. IEEE J Sel Areas Commun 26(5):748–760
Sharef BT, Alsaqour RA, Ismail M (2014) Vehicular communication ad hoc routing protocols: a survey. J Netw Comput Appl 40:363–396
Daly EM, Haahr M (2007) Social network analysis for routing in disconnected delay-tolerant manets. In: Proceedings of the 8th ACM International Symposium on Mobile ad hoc Networking and Computing. ACM, pp 32–40
Wu J, Xiao M, Huang L (2013) Homing spread: Community home-based multi-copy routing in mobile social networks. In: INFOCOM, 2013 Proceedings IEEE. IEEE, pp 2319– 2327
Gao W, Cao G (2010) On exploiting transient contact patterns for data forwarding in delay tolerant networks. In: 2010 18th IEEE International Conference on Network Protocols (ICNP). IEEE, pp 193–202
Zhang X, Cao G (2013) Transient community detection and its application to data forwarding in delay tolerant networks. In: 2013 21st IEEE International Conference on Network Protocols (ICNP). IEEE, pp 1–10
Hui P, Crowcroft J, Yoneki E (2011) Bubble rap: Social-based forwarding in delay-tolerant networks. IEEE Trans Mob Comput 10(11):1576–1589
Daly EM, Haahr M (2007) Social network analysis for routing in disconnected delay-tolerant manets. In: Proceedings of the 8th ACM International Symposium on Mobile ad hoc Networking and Computing. ACM, pp 32–40
Hussain R (2014) Cooperation-aware vanet clouds: providing secure cloud services to vehicular ad hoc networks. J Inf Process Syst 10(1):103–118
Md Nawaz Ali G, Mollah S, Abdus M, Samantha SK, Mahmud S (2014) An efficient cooperative load balancing approach in rsu-based vehicular ad hoc networks (vanets). In: 2014 IEEE International Conference on Control System, Computing and Engineering (ICCSCE). IEEE, pp 52–57
Sun Y, Zhang J, Xiong Y, Zhu G (2014) Data security and privacy in cloud computing. Int J Distrib Sens Netw 2014
Scandariato R, Wuyts K, Joosen W (2014) A descriptive study of microsoft’s threat modeling technique. Requir Eng 20(2):163–180
Cohen F (1999) Simulating cyber attacks, defences, and consequences. Comput Secur 18(6):479–518
Cheung S, Lindqvist U, Fong MW (2003) Modeling multistep cyber attacks for scenario recognition. In: DARPA Information Survivability Conference and Exposition, 2003. Proceedings, vol 1. IEEE, pp 284–292
Wu J, Yin L, Guo Y (2012) Cyber attacks prediction model based on bayesian network. In: 2012 IEEE 18th International Conference on Parallel and Distributed Systems (ICPADS). IEEE, pp 730–731
Ingols K, Chu M, Lippmann R, Webster S, Boyer S (2009) Modeling modern network attacks and countermeasures using attack graphs. In: Computer Security Applications Conference, 2009. ACSAC’09. Annual. IEEE, pp 117–126
Camtepe SA, Yener B (2007) Modeling and detection of complex attacks. In: Third International Conference on Security and Privacy in Communications Networks and the Workshops, 2007. SecureComm 2007. IEEE, pp 234–243
Chen TM, Sanchez-Aarnoutse JC, Buford J (2011) Petri net modeling of cyber-physical attacks on smart grid. IEEE Trans Smart Grid 2(4):741–749
Ekedebe N, Yu W, Song H, Lu C (2015) On a simulation study of cyber attacks on vehicle-to-infrastructure communication (v2i) in intelligent transportation system (its). In: SPIE Sensing Technology+ Applications. International Society for Optics and Photonics, pp 94 970B–94 970B
Mo Y, Sinopoli B (2009) Secure control against replay attacks. In: 47th Annual Allerton Conference on Communication, Control, and Computing, 2009. Allerton 2009. IEEE, pp 911– 918
Yilin Mo BS, chabukswar R (2014) Detecting integrity attacks on scada systems. IEEE Trans Control Syst Technol 22(4):1396–1407
Kwon C, Liu W, Hwang I (2013) Security analysis for cyber-physical systems against stealthy deception attacks. Am Control Conf (ACC) 2013:3344–3349
Weimerskirch A, Thonet G (2002) A distributed light-weight authentication model for Ad-hoc networks. Springer, Berlin Heidelberg
Scarfone K, Mell P (2007) Guide to intrusion detection and prevention systems (idps), NIST SP - 800–94
Garca-Teodoro P, Daz-Verdejo J, Maci-Fernndez G, Vzquez E (2009) Anomaly-based network intrusion detection: techniques, systems and challenges. Comput Secur 28:188
Li W, Joshi A, Finin T Svm-case: An svm-based context aware security framework for vehicular ad-hoc networks. In: 82nd IEEE Vehicular Technology Conference. IEEE
Spitzner L (2003) Honeypots: tracking hackers, vol 1. Addison-Wesley Reading
Nikolaidis J (2003) Honeypots, tracking hackers [book reviews]. IEEE Netw 17(4):5–5
Gantsou D, Sondi P (2014) Toward a honeypot solution for proactive security in vehicular ad hoc networks. Lecture Notes in Electrical Engineering
Guerrero M, Guerrero M (2001) Secure ad hoc on-demand distance vector (saodv) routing. Internet Draft Ietf Mob Ad Hoc Netw Work Group 6(7):106–107
Hu YC (2002) Perrig a, johnson db. ariadne: a secure on-demand routing protocol for ad hoc networks. Proc Acm Int Conf Mob Comput Netw 11(1-2):21–38
Ping YI, Jiang YC, Zhong YP (2005) A survey of secure routing for mobile ad hoc networks. Comput Sci 1(3):27–31
Yao CC, Yao CC (1982) Protocols for secure computations (extended abstract), Pcr—O(1/n) = O(1) points from P Pcr in Si, since Pr[p Si] = (n 1/c ) is, pp 160–164
Zhang X, Wang X, Liu A, Zhang Q, Tang C (2012) Pri: a practical reputation-based incentive scheme for delay tolerant networks. Ksiitransactionsoninternetandinformationsystems 6(4):973–988
Lu X, Hui P, Towsley D, Pu J, Xiong Z (2010) Anti-localization anonymous routing for delay tolerant network. Comput Netw Int J Comput Telecommun Netw 54(11):1899–1910
Lin X, Lu R, Liang X, Shen X (2011) Stap: a social-tier-assisted packet forwarding protocol for achieving receiver-location privacy preservation in vanets. Proc - IEEE INFOCOM 28(6):2147–2155
Ozturk C, Zhang Y, Trappe W (2004) Source-location privacy in energy-constrained sensor network routing, Acm Sasn, pp 88–93
Chen Y, Xu W, Trappe W, Zhang Y (2005) Enhancing source-location privacy in sensor network routing. In: 2013 IEEE 33rd International Conference on Distributed Computing Systems, pp 599–608
Yong HK, Lee H, Dong HL, Lim J (2006) A key management scheme for large scale distributed sensor networks. Lect Notes Comput Sci:437–446
Zhang C, Lu R, Lin X, Ho P-H, Shen X (2008) An efficient identity-based batch verification scheme for vehicular sensor networks. In: INFOCOM 2008. The 27th Conference on Computer Communications. IEEE. IEEE
Shah N, Huang D (2010) A-weor: Communication privacy protection for wireless mesh networks using encoded opportunistic routing. In: INFOCOM IEEE Conference on Computer Communications Workshops, pp 1–6
Li Y, Ren J (2009) Preserving source-location privacy in wireless sensor networks. In: 6th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, 2009. SECON ’09, pp 1–9
Sherer SA (1992) Risk analysis and management. Appl Modern Technol Bus 269(1):13–24
Raman B, Mao ZM et al (2002) The sahara model for service composition across multiple providers. In: Pervasive Computing, pp 1–14
He Z, Cai Z, Wang X (2015) Modeling propagation dynamics and developing optimized countermeasures for rumor spreading in online social networks. In: The 35th IEEE International Conference on Distributed Computing Systems, pp 205–214
Wang Y, Cai Z, Yin G, Gao Y, Pan Q (2016) A game theory-based trust measurement model for social networks, Computational Social Networks
Wang Y, Yin G, Cai Z, Dong Y, Dong H (2015) A trust-based probabilistic recommendation model for social networks. J Netw Comput Appl 55:59–67
Salama HF, Reeves DS, Viniotis Y (1997) A distributed algorithm for delay-constrained routing. IEEE/ACM Trans Netw 8(2):84
Raisinghani VT, Iyer S (2004) Cross-layer design optimizations in wireless protocol stacks. Comput Commun 27(8):720–724
Wang S, Bie R, Zhao F, Zhang N, Cheng X, Choi H.-A (2015) Security in wearable communications. IEEE Network. (In press)
Whaiduzzaman M, Sookhak M, Gani A, Buyya R (2014) A survey on vehicular cloud computing. J Netw Comput Appl 40(1):325–344
Casetti C, Torino PD (2012) Security and privacy in ivc. In: Proceedings CCNC 2012 Tutorial
King R (2015) Gm grapples with big data, cybersecurity in vehicle broadband connections. The Wall Street Journal, p 10
Sun Y, Jara AJ (2014) An extensible and active semantic model of information organizing for the internet of things. Pers Ubiquit Comput 18(8):1821–1833
Sun Y, Yan H, Lu C, Bie R, Zhou Z (2014) Constructing the web of events from raw data in the web of things. Mob Inf Syst 10(1):105–125
Mccarthy C, Harnett K (2014) National institute of standards and technology (nist) cybersecurity risk management framework applied to modern vehicles, Risk Management
Zhang T, Delgrossi L (2012) Vehicle safety communications: protocols, security, and privacy, vol 103. Wiley
Acknowledgment
This research is sponsored by the National Natural Science Foundation of China (No. 61371185, 61571049) and China Postdoctoral Science Foundation (No.2015M571231).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sun, Y., Wu, L., Wu, S. et al. Attacks and countermeasures in the internet of vehicles. Ann. Telecommun. 72, 283–295 (2017). https://doi.org/10.1007/s12243-016-0551-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12243-016-0551-6