Abstract
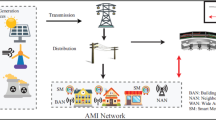
In addition to changing service management, smart devices connect people and objects around them and collect data from them on and on, in order to construct the notion of a smart city. Such data produced by embedded devices and automatically transmitted over the Internet provides people with the information to make decisions. A smart grid is one of the most popular applications for a smart city. Due to the insecurity of the wireless channels, the security of data transmission in a smart grid has become a hot issue nowadays. Many schemes for data protection have been proposed, but weaknesses exist generally. We present a new data transmission scheme for a smart grid among the smart meter (SM), the electricity utility (EU), and the trusted authority (TA). The EU can obtain the power consumption of each SM, but cannot get the real identity of the SM. To keep the privacy of the user, if the consumption value is over the threshold in special time span or identity of SM is required for public affairs, TA could track the identity in time. Formal proof with random oracle model and security analysis are expressed to show the security of the proposed scheme. Via the performance and network simulation, it is easy to see that our scheme is practical for a smart city.



Similar content being viewed by others
References
Li W, Chen Z, Gao X, Liu W, Wang J (2019) Multi-model framework for indoor localization under mobile edge computing environment. IEEE Internet Things J 6(3):4844–4853. https://doi.org/10.1109/JIOT.2018.2872133
Wang J, Gao Y, Yin X, Li F, Kim HJ (2018) An enhanced PEGASIS algorithm with mobile sink support for wireless sensor networks. Wirel Commun Mob Comput, 1–9. https://doi.org/10.1155/2018/9472075
Wang J, Ju C, Gao Y, Sangaiah AK, Gj Kim (2018) A PSO based energy efficient coverage control algorithm for wireless sensor networks. Comput Mater Continua 56(3):433–446
Wang J, Gao Y, Liu W, Wu W, Lim SJ (2019) An asynchronous clustering and mobile data gathering schema based on timer mechanism in wireless sensor networks. Comput Mater Continua 58(3):711–725
Wang J, Gao Y, Liu W, Sangaiah AK, Kim HJ (2019) An intelligent data gathering schema with data fusion supported for mobile sink in wireless sensor networks. International Journal of Distributed Sensor Networks. https://doi.org/10.1177/1550147719839581
Liang W, Fan Y, Li KC, Zhang D, Gaudiot JL (2020) Secure data storage and recovery in industrial blockchain network environments. IEEE Transactions on Industrial Informatics
Liang W, Li KC, Long J, Kui X, Zomaya AY (2020) An industrial network intrusion detection algorithm based on multi-feature data clustering optimization model. IEEE Trans Industr Inform 16(3):2063–2071
He S, Xie K, Xie K, Xu C, Jin W (2019) Interference-aware multi-source transmission in multi-radio and multi-channel wireless network. IEEE Syst J 13 (3):2507–2518. https://doi.org/10.1109/JSYST.2019.2910409
He S, Tang Y, Li Z, Li F, Xie K, Kim HJ, Kim GJ (2019) Interference-aware routing for difficult wireless sensor network environment with SWIPT. Sensors 19(18):3978. https://doi.org/10.3390/s19183978
Zhang J, Wang W, Lu C, Wang J, Sangaiah AK (2019) Lightweight deep network for traffic sign classification. Ann Telecommun, 1–11. https://doi.org/10.1007/s12243-019-00731-9
Zhang M, Lu Q, Li D, Kim J, Wang J (2019) A full convolutional network based on densenet for remote sensing scene classification. Math Biosci Eng: MBE 16(5):3345–3367
He S, Li Z, Tang Y, Liao Z, Wang J, Kim HJ (2019) Parameters compressing in deep learning. Comput Mater Continua, 1–16
Zhang J, Jin X, Sum J, Wang J, Li K (2019) Dual model learning combined with multiple feature selection for accurate visual tracking. IEEE Access 7(1):43,956–43,969
Zhang J, Jin X, Sun J, Wang J, Sangaih AK (2018) Spatial and semantic convolutional features for robust visual object tracking. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-018-6562-8
Liang W, Huang W, Long J, Zhang K, Li KC, Zhang D (2020) Deep reinforcement learning for resource protection and real-time detection in IoT environment. IEEE Internet of Things Journal
Kumar N, Aujla GS, Das AK, Conti M (2019) Eccauth: a secure authentication protocol for demand response management in a smart grid system. IEEE Trans Industr Inform 15(12):6572– 6582
He D, Kumar N, Zeadally S, Wang H (2018) Certificateless provable data possession scheme for cloud-based smart grid data management systems. IEEE Trans Industr Inform 14(3):1232–1241
Gong Y, Cai Y, Guo Y, Fang Y (2016) A privacy-preserving scheme for incentive-based demand response in the smart grid. IEEE Trans Smart Grid 7(3):1304–1313
Sui Z, Niedermeier M, de Meer H (2016) TAI: a threshold-based anonymous identification scheme for demand-response in smart grids. IEEE Trans Smart Grid 9(4):3496–3506
Ge S, Zeng P, Choo KKR (2017) An enhanced anonymous identification scheme for smart grids. In: International Conference on Applications and Techniques in Cyber Security and Intelligence. Springer, pp 329–337
Cooper C (2017) Humanizing smart cities. https://inform.tmforum.org/features-and-analysis/2017/03/humanizing-smart-cities/
Geisler K (2013) The relationship between smart grids and smart cities. IEEE Smart Grid Newsletter
Kursawe K, Danezis G, Kohlweiss M (2011) Privacy-friendly aggregation for the smart-grid. In: International Symposium on Privacy Enhancing Technologies Symposium. Springer, pp 175–191
He D, Kumar N, Zeadally S, Vinel A, Yang LT (2017) Efficient and privacy-preserving data aggregation scheme for smart grid against internal adversaries. IEEE Trans Smart Grid 8(5):2411–2419
He D, Zeadally S, Wang H, Liu Q (2017) Lightweight data aggregation scheme against internal attackers in smart grid using elliptic curve cryptography. Wirel Commun Mob Comput, 2017. https://doi.org/10.1155/2017/3194845
Wang Z (2017) An identity-based data aggregation protocol for the smart grid. IEEE Trans Industr Inform 13(5):2428–2435
Ni J, Zhang K, Lin X, Shen XS (2016) EDAT: efficient data aggregation without TTP for privacy-assured smart metering. In: 2016 IEEE International Conference on Communications (ICC). IEEE, pp 1–6
Dong X, Zhou J, Cao Z (2016) Efficient privacy-preserving temporal and spacial data aggregation for smart grid communications. Concurr Comput: Practice Exper 28(4):1145–1160
Ferrag MA (2017) EPEC: an efficient privacy-preserving energy consumption scheme for smart grid communications. Telecommun Syst 66(4):671–688
Badra M, Zeadally S (2017) Lightweight and efficient privacy-preserving data aggregation approach for the smart grid. Ad Hoc Netw 64:32–40
Li S, Xue K, Yang Q, Hong P (2018) PPMA: privacy-preserving multisubset data aggregation in smart grid. IEEE Trans Industr Inform 14(2):462–471
Li X, Liu S, Wu F, Kumari S, Rodrigues JJ (2019) Privacy preserving data aggregation scheme for mobile edge computing assisted IoT applications. IEEE Internet Things J 6(3):4755–4763
Shen H, Zhang M, Shen J (2017) Efficient privacy-preserving cube-data aggregation scheme for smart grids. IEEE Trans Inform Forens Secur 12(6):1369–1381
Song J, Liu Y, Shao J, Tang C (2019) A dynamic membership data aggregation (DMDA) protocol for smart grid. IEEE Systems Journal. https://doi.org/10.1109/JSYST.2019.2912415
Kumari S, Li X, Wu F, Das AK, Arshad H, Khan MK (2016) A user friendly mutual authentication and key agreement scheme for wireless sensor networks using chaotic maps. Futur Gener Comput Syst 63:56–75
Wang D, Li W, Wang P (2018) Measuring two-factor authentication schemes for real-time data access in industrial wireless sensor networks. IEEE Trans Industr Inform 14(9):4081–4092
Li X, Niu J, Bhuiyan MZA, Wu F, Karuppiah M, Kumari S (2018) A robust ECC-based provable secure authentication protocol with privacy preserving for industrial Internet of Things. IEEE Trans Industr Inform 14(8):3599–3609
Fouda MM, Fadlullah ZM, Kato N, Lu R, Shen XS (2011) A lightweight message authentication scheme for smart grid communications. IEEE Trans Smart Grid 2(4):675–685
Mahmood K, Chaudhry SA, Naqvi H, Shon T, Ahmad HF (2016) A lightweight message authentication scheme for smart grid communications in power sector. Comput Electr Eng 52:114–124
Tsai JL, Lo NW (2016) Secure anonymous key distribution scheme for smart grid. IEEE Trans Smart Grid 7(2):906–914
Odelu V, Das AK, Wazid M, Conti M (2016) Provably secure authenticated key agreement scheme for smart grid. IEEE Trans Smart Grid 9(3):1900–1910
He D, Wang H, Khan MK, Wang L (2016) Lightweight anonymous key distribution scheme for smart grid using elliptic curve cryptography. IET Commun 10(14):1795–1802
Wu F, Xu L, Li X, Kumari S, Karuppiah M, Obaidat MS (2019) A lightweight and provably secure key agreement system for smart grid with elliptic curve cryptography. IEEE Syst J 13(3):2830–2838
Mahmood K, Chaudhry SA, Naqvi H, Kumari S, Li X, Sangaiah AK (2018) An elliptic curve cryptography based lightweight authentication scheme for smart grid communication. Futur Gener Comput Syst 81:557–565
Li X, Peng J, Niu J, Wu F, Liao J, Choo KKR (2018) A robust and energy efficient authentication protocol for industrial Internet of Things. IEEE Internet Things J 5(3):1606–1615
Diao F, Zhang F, Cheng X (2015) A privacy-preserving smart metering scheme using linkable anonymous credential. IEEE Trans Smart Grid 6(1):461–467
Kishimoto H, Yanai N, Okamura S (2017) An anonymous authentication protocol for smart grid. In: 2017 31st International Conference on Advanced Information Networking and Applications Workshops (WAINA). IEEE, pp 62–67
Zhang X, Wen M, Lu K, Lei J (2017) A privacy-aware data dissemination scheme for smart grid with abnormal data traceability. Comput Netw 117:32–41
Qu H, Shang P, Lin XJ, Sun L (2015) Cryptanalysis of a privacy-preserving smart metering scheme using linkable anonymous credential. IACR Cryptology ePrint Archive 2015:1066
Pointcheval D, Stern J (2000) Security arguments for digital signatures and blind signatures. J Cryptol 13 (3):361–396
Zeng S, Jiang S, Qin Z (2012) An efficient conditionally anonymous ring signature in the random oracle model. Theor Comput Sci 461:106–114
Wu F, Li X, Sangaiah AK, Xu L, Kumari S, Wu L, Shen J (2018) A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Futur Gener Comput Syst 82:727–737
nsnamorg (2017) Ns-3.26. https://www.nsnam.org/ns-3-26/
Funding
This research was supported by the Program for New Century Excellent Talents in Fujian Province University (Year 2018). Dr. Li is supported by the Scientific Research Fund of Hunan Provincial Education Department under Grant No. 18A178 and the Natural Science Foundation of Hunan Province, China under Grant No. 2018JJ3191. Dingbao Lin is supported by University Distinguished Young Research Talent Training Program of Fujian Province (Year 2018). Prof. Joel Rodrigues is supported by FCT/MCTES through national funds and when applicable co-funded by EU funds under the project UIDB/EEA/50008/2020; and by the Brazilian National Council for Scientific and Technological Development (CNPq) via Grant No. 309335/2017-5.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wu, F., Li, X., Xu, L. et al. An anonymous and identity-trackable data transmission scheme for smart grid under smart city notion. Ann. Telecommun. 75, 307–317 (2020). https://doi.org/10.1007/s12243-020-00765-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12243-020-00765-4