Abstract
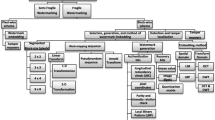
This paper presents a survey of fragile watermarking schemes for image authentication proposed in the past decade. The limited embedding capacity and extent of tampering are some of the important issues among other issues that drive the research in this area. Therefore we have presented in this survey the gist of the fragile watermarking schemes in just enough detail so that the reader may gain a fair idea of the issues, techniques adopted in general to address them and the comparison of results. The general frame work of the fragile watermarking system, different categories of attacks and parameters used to evaluate the schemes are presented in this survey. The comparative analysis and the quantitative comparison of basic schemes and their variations with improvements will help the researchers in quick review of the recent developments in this area.



Similar content being viewed by others
References
Rey C, Dugelay J-L (2002) A survey of watermarking algorithms for image authentication. EURASIP J Appl Signal Proc. doi:10.1155/S1110865702204047
Haouzia A, Noumeir R (2008) Methods for image authentication: a survey. Multimed Tools Appl 39:1–46
Han S-H, Chu C-H (2010) Content-based image authentication: current status, issues, and challenges. Int J Inf Secur 9:19–32
Lin ET, Delp EJ (1999) A review of fragile image watermarks, in proceedings of multimedia and security Workshop multimedia contents, 25–29
Verma VS, Jha RK (2015) An overview of robust digital image watermarking. IETE Tech Rev 32(6):479–496
Wong PW, Memon N (2001) Secret and public key image watermarking schemes for image authentication and ownership verification. IEEE Trans Image Process 10(10):1593–1601
Chang C-C, Fan Y-H, Tai W-L (2008) four-scanning attack on hierarchical digital watermarking method. Pattern Recognit 41:654–661
Fridrich J, Goljan M (1999) Protection of digital images using self embedding, in Symposium on Content Security and Data Hiding in Digital Media. New Jersey Institute of Technology, Newark, NJ
He H, Chen F, Tai H-M, Kalker T, Zhang J (2012) Performance analysis of a block-neighbourhood-based self-recovery fragile watermarking scheme. IEEE Trans Inform Forens Secur 7(1):185–196
He H-J, Zhang J-S, Tai H-M (2009) Self-recovery Fragile Watermarking Using Block-Neighborhood Tampering Characterization, IH, LNCS 5806, pp. 132–145
Lin PL, Hsieh C-K, Huang P-W (2005) A hierarchical digital watermarking method for image tamper detection and recovery. Pattern Recognit 38:2519–2529
Lee T-Y, Lin SD (2008) Dual watermark for image tamper detection and recovery. Pattern Recognit 41:3497–3506
Li CL, Wang YH, Ma B, Zhang ZX (2011) A novel self-recovery fragile watermarking scheme based on dual redundant-ring structure. Comput Electr Eng 37(6):927–940
Xiao D, Shih FY (2012) An improved hierarchical fragile watermarking scheme using chaotic sequence sorting and sub-block post-processing. Opt Commun 285:2596–2606
El’arbi M, Amar CB (2014) Image authentication algorithm with recovery capabilities based on neural networks in the DCT domain. IET Image Process 8(11):619–626
Zhang X, Qian Z, Ren Y, Feng G (2011) Watermarking with flexible self-recovery quality based on compressive sensing and compositive reconstruction. IEEE Trans Inform Foren Secur 6(4):1223–1232
Korus P, Dziech A (2013) Efficient method for content reconstruction with self-embedding. IEEE Trans Image Proc 22(3):1134–1147
Zhang J, Zhanga Q, Lvba H (2013) A novel image tamper localization and recovery algorithm based on watermarking technology. Optik 124:6367–6371
Dadkhah S, Manaf AA, Hori Y, Hassanien AE, Sadeghi S (2014) An effective SVD-based image tampering detection and self-recovery using active watermarking. Signal Proc Image Comm 29:1197–1210
Lee C-W, Tsai W-H (2012) Optimal pixel-level self-repairing authentication method for gray scale images under a mini-max criterion of distortion reduction. Opt Eng 51(5): 0570061–11
Qin C, Chang C-C, Chen K-N (2013) Adaptive self-recovery for tampered images based on VQ indexing and inpainting. Signal Process 93:933–946
Li C, Wang Y, Ma B, Zhang Z (2013) Multi-block dependency based fragile watermarking scheme for fingerprint images protection. Multimed Tools Appl 64:757–776
He H-J, Zhang J-S, Chen F (2009) Adjacent-block based statistical detection method for self-embedding watermarking techniques. Signal Process 89:1557–1566
Singh D, Singh SK (2016) Effective self-embedding watermarking scheme for image tampered detection and localization with recovery capability. J Vis Commun Image R 38:775–789
Qian Z, Feng G, Zhang X, Wang S (2011) Image self-embedding with high-quality restoration capability. Digit Signal Proc 21:278–286
Huo Y, He H, Chen F (2012) Alterable-capacity fragile watermarking scheme with restoration capability. Opt Commun 285:1759–1766
Chen F, He H, Tai H-M, Wang H (2012) Chaos-based self-embedding fragile watermarking with flexible watermark payload. Multimed Tools Appl. doi:10.1007/s11042-012-1332-5
Qian Z, Feng G (2010) Inpainting assisted self recovery with decreased embedding data. IEEE Signal Process Lett 17(11):929–932
Liu K-C (2012) Colour image watermarking for tamper proofing and pattern-based recovery. IET Image Process 6(5):445–454
Liu K-C (2014) Self-embedding watermarking scheme for colour images by bi-level moment-preserving technique. IET Image Process 8(6):363–372
Wang M-S, Chen W-C (2007) A majority-voting based watermarking scheme for color image tamper detection and recovery. Comput Stand Interfac 29:561–570
He H, Zhang J (2012) Cryptanalysis on majority-voting based self-recovery watermarking scheme. Telecommun Syst 49:231–238. doi:10.1007/s11235-010-9380-5
Zhang X, Wang S (2007) Statistical fragile watermarking capable of locating individual tampered pixels. IEEE Signal Process Lett 14(10):727–730
Zhang X, Wang S (2009) Fragile watermarking scheme using a hierarchical mechanism. Signal Process 89:675–679
Zhang X, Wang S, Qian Z, Feng G (2011) Self-embedding watermark with flexible restoration quality. Multimed Tools Appl 54:385–395
Bravo-Solorio S, Nandi AK (2011) Secure fragile watermarking method for image authentication with improved tampering localisation and self-recovery capabilities. Signal Proc 91:728–739
Zhang X, Wang S, Qian Z, Feng G (2010) Reversible fragile watermarking for locating tampered blocks in JPEG images. Signal Process 90:3026–3036
Zhang X, Wang S (2008) Fragile Watermarking With Error-Free Restoration Capability. IEEE Trans Multimed 10(8):1490–1499
Hsu C-S, Tu S-F (2010) Probability-based tampering detection scheme for digital images. Opt Commun 283:1737–1743
Chan CS, Chang CC (2007) An efficient image authentication method based on hamming code. Pattern Recognit 40(2):681–690
Chan C-S (2011) An image authentication method by applying Hamming code on rearranged bits. Pattern Recognit Lett 32:1679–1690
Changa C-C, Chen K-N, Leec C-F, Liu L-J (2011) A secure fragile watermarking scheme based on chaos-and-hamming code. J Syst Softw 84:1462–1470
Qin C, Chang C-C, Chen P-Y (2012) Self-embedding fragile watermarking with restoration capability based on adaptive bit allocation mechanism. Signal Process 92:1137–1150
Wang X, Zhang D, Guo X (2013) A novel image recovery method based on discrete cosine transform and matched blocks. Nonlinear Dyn 73:1945–1954
Li C, Zhang A, Liu Z, Liao L, Huang D (2015) Semi-fragile self-recoverable watermarking algorithm based on wavelet group quantization and double authentication. Multimed Tools Appl 74:10581–10604
Yeh FH, Lee GC (2006) Content-based watermarking in image authentication allowing remedying of tampered images. Opt Eng 45(7):0770041–10
Qin C, Chang C-C, Hsu T-J (2013) Effective fragile watermarking for image authentication with high-quality recovery capability. KSII Trans Internet Inform Syst 7(11):2941–2956
Huo Y, He H, Chen F (2014) A Restorable Semi-fragile Watermarking Combined DCT with Interpolation, IWDW 2013, LNCS 8389, pp. 393–408
Zhang X, Xiao Y, Zhao Z (2014) Self-embedding fragile watermarking based on DCT and fast fractal coding. Multimed Tools Appl. doi:10.1007/s11042-014-1882-9
Pred RO, Vizireanu DN (2015) Watermarking-based image authentication robust to JPEG compression. Electr Lett 51(23):1873–1875
Singh P, Agarwal S (2015) An efficient fragile watermarking scheme with multilevel tamper detection and recovery based on dynamic domain selection. Multimed Tools Appl. doi:10.1007/s11042-015-2736-9
Rosales-Roldan L, Cedillo-Hernandez M, Nakano-Miyatake M, Perez-Meana H, Kurkoski B (2013) Watermarking-based image authentication with recovery capability using halftoning technique. Signal Process Image Comm 28:69–83
He H, Zhang J, Tai H-M (2006) A wavelet-based fragile watermarking scheme for secure image authentication, IWDW 2006, LNCS 4283, pp. 422–432
Chamlawi R, Khan A, Usman I (2010) Authentication and recovery of images using multiple watermarks. Comput Electr Eng 36:578–584
Qi X, Xin X (2011) A quantization-based semi-fragile watermarking scheme for image content authentication. J Vis Commun Image R 22:87–200
Preda RO (2013) Semi-fragile watermarking for image authentication with sensitive tamper localization in the wavelet domain. Measurement 46:367–373
Ullah R, Khan A, Malik AS (2013) Dual-purpose semi-fragile watermark: authentication and recovery of digital images. Comput Electr Eng 39:2019–2030
Tsai M-J, Chien C-C (2008) Authentication and recovery for wavelet-based semi-fragile watermarking. Opt Eng 47(6):0670051–10
Li C-T, Si H (2007) Wavelet-based fragile watermarking scheme for image authentication. J Electr Imaging 16(1):0130091–10
Nguyen T-S, Chang C-C, Yang X-Q (2016) A reversible image authentication scheme based on fragile watermarking in discrete wavelet transform domain. Int J Electron Commun (AEÜ) 70:1055–1061
Phadikar A, Maity SP, Mandal M (2012) Novel wavelet-based QIM data hiding technique for tamper detection and correction of digital images. J Vis Commun Image R 23:454–466
Yang C-W, Shen J-J (2010) Recover the tampered image based on VQ indexing. Signal Process 90:331–343
Chuang J-C, Hu Y-C (2011) An adaptive image authentication scheme for vector quantization compressed image. J Vis Commun Image R 22:440–449
Wang S-S, Tsai S-L (2008) Automatic image authentication and recovery using fractal code embedding and image inpainting. Pattern Recognit 41:701–712
Patra JC, Karthika A, Bornand C (2010) A novel CRT-based watermarking technique for authentication of multimedia contents. Digit Signal Process 20:442–453
Chen W-C, Wang M-S (2009) A fuzzy c-means clustering-based fragile watermarking scheme for image authentication. Expert Systems Appl 36:1300–1307
Ghosal SK, Mandal JK (2014) Binomial transform based fragile watermarking for image authentication. J Inform Secur Appl 19:272–281
Lin P-Y, Lee J-S, Chang C-C (2011) Protecting the content integrity of digital imagery with fidelity preservation. ACM Trans Multimed Comput Commun Appl 7(3):15
Ho ATS, Zhu X, Shen J, Marziliano P (2008) Fragile watermarking based on encoding of the zeroes of the z–Transform. IEEE Trans Inform Foren Secur 3(3):567–569
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sreenivas, K., Kamkshi Prasad, V. Fragile watermarking schemes for image authentication: a survey. Int. J. Mach. Learn. & Cyber. 9, 1193–1218 (2018). https://doi.org/10.1007/s13042-017-0641-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13042-017-0641-4