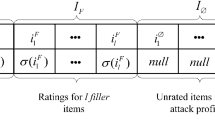
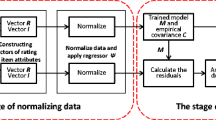
Abstract
Although collaborative filtering achieves satisfying performance in recommender systems, many studies suggest that it is vulnerable by shilling attack aimed to manipulate the recommending frequency of a target item by injecting malicious user profiles. The existing attack methods usually generate malicious profiles by rating the item selected randomly. However, as these rating patterns are different from the real users, who have their own preferences on items, these attack methods can be easily detected by shilling attack detection, which significantly reduces the attack ability. Although some attack methods consider disguise ability, these methods require too much information from real users. This study proposes a shilling attack which generates malicious samples with strong attack ability and similarity to real users. To imitate the rating behavior of genuine users, our attack model considers both rated item correlation and item popularity when choosing items to rate. The profiles generated by our attack model is expected to be more similar to real user profiles, which increases the disguise ability. We also investigate whether and how rated item correlation of real user profiles is different from the ones generated by our method and the existing shilling attack. The experimental results confirm that our method achieves the highest attack ability after removing the suspected profiles identified by PCA-based and SVM-based shilling attack detection. The study confirms the correlation of rated item is a critical factor of the robustness of recommender systems.











Similar content being viewed by others
References
Ricci F (2011) Recommender systems handbook. Springer, Berlin
Ding L, Han B, Wang S, Li X, Song B (2017) User-centered recommendation using us-elm based on dynamic graph model in e-commerce. Int J Mach Learn Cybern. https://doi.org/10.1007/s13042-017-0751-z
Silveira T, Zhang M, Lin X, Liu Y, Ma S (2017) How good your recommender system is? A survey on evaluations in recommendation. Int J Mach Learn Cybern 6:1–19
Ortega F, Hernando A, Bobadilla J, Kang JH (2016) Recommending items to group of users using matrix factorization based collaborative filtering. Inf Sci 345(C):313–324
Shan L, Lin L, Sun C, Wang X, Liu B (2016) Optimizing ranking for response prediction via triplet-wise learning from historical feedback. Int J Mach Learn Cybern 8(6):1777–1793
Patel K, Thakkar A, Shah C, Makvana K (2016) A state of art survey on shilling attack in collaborative filtering based recommendation system. Springer, Berlin
Mobasher B, Burke R, Bhaumik R, Williams C (2007) Toward trustworthy recommender systems: an analysis of attack models and algorithm robustness. ACM Trans Internet Technol 7(4):23
Gunes I, Kaleli C, Bilge A, Polat H (2014) Shilling attacks against recommender systems: a comprehensive survey. Artif Intell Rev 42(4):767–799
Lam SK, Riedl J (2004) Shilling recommender systems for fun and profit. Int Conf World Wide Web 2004:393–402
Gunes I, Bilge A, Polat H (2013) Shilling attacks against memory-based privacy-preserving recommendation algorithms. KSII Trans Internet Inf Syst 7(5):1272–1290
Burke R, Mobasher B, Bhaumik R (2005) Limited knowledge shilling attacks in collaborative filtering systems. In: Proceedings of 3rd international workshop in intelligent techniques for personalization (ITWP 2005), 19th international joint conference on artificial intelligence (IJCAI 2005), Edinburgh, Scotland
Zhang F, Zhou Q (2012) A meta-learning-based approach for detecting profile injection attacks in collaborative recommender systems. J Comput 7(1):226–234
Zhang Z, Kulkarni SR (2013) Graph-based detection of shilling attacks in recommender systems. In: Proceedings of the IEEE international workshop on machine learning for signal processing, pp 1–6
Yang Z, Cai Z (2017) Detecting abnormal profiles in collaborative filtering recommender systems. J Intell Inf Syst 48(3):499–518
Xia N, Desrosiers C, Karypis G (2015) A comprehensive survey of neighborhood-based recommendation methods. Springer, Berlin
Luo Z, Liang C (2017) An insider attack on shilling attack detection for recommendation systems. In: 2016 7th IEEE international conference on software engineering and service science (ICSESS), Beijing, pp 277–280
Mobasher B, Burke R, Bhaumik R, Williams C (2005) Effective attack models for shilling item-based collaborative filtering systems. In: Proceedings of the Webkdd workshop, Chicago
Seminario CE (2013) Accuracy and robustness impacts of power user attacks on collaborative recommender systems. In: Proceedings of the 7th ACM conference on recommender systems, RecSys 2013. ACM Press, New York, pp 447–450
Mahara ST (2016) A new similarity measure based on mean measure of divergence for collaborative filtering in sparse environment. Procedia Comput Sci 89:450–456
O’Mahony MP, Hurley NJ, Silvestre GCM (2005) Recommender systems: attack types and strategies. In: The twentieth national conference on artificial intelligence and the seventeenth innovative applications of artificial intelligence conference, Pittsburgh, 9–13 July 2005, pp 334–339
O’Mahony MP, Hurley NJ, Silvestre G, CM (2006) Detecting noise in recommender system databases. In: International conference on intelligent user interfaces, Sydney, 29 Jan–1 Feb 2006, pp 109–115
Hurley N, Cheng Z, Zhang M (2009) Statistical attack detection. In: ACM conference on recommender systems, Recsys 2009, New York, pp 149–156
Zhang F, Zhou Q (2014) HHT–SVM: an online method for detecting profile injection attacks in collaborative recommender systems. Knowl Based Syst 65(4):96–105
Chirita PA, Nejdl W, Zamfir C (2005) Preventing shilling attacks in online recommender systems. In: ACM international workshop on web information and data management. ACM, New York, USA, pp 67–74
Li WT, Gao M, Li H, Xiong QY, Wen JH, Ling B (2011) An shilling attack detection algorithm based on popularity degree features. Acta Autom Sin 41(9):1563–1576
Su XF, Zeng HJ, Chen Z (2005) Finding group shilling in recommendation system. In: Proceedings of the 14th international conference on world wide web, Chiba, Japan, pp 960–961
Burke R, Mobasher B, Williams C, Bhaumik R (2006) Classification features for attack detection in collaborative recommender systems. In: Proceedings of the 12th ACM SIGKDD international conference on knowledge discovery and data mining, Philadelphia, PA, USA, pp 542–547
Williams CA, Mobasher B, Burke R (2007) Defending recommender systems: detection of profile injection attacks. Serv Oriented Comput Appl 1(3):157–170
Chengshu LV, Wang W (2013) Semi-supervised shilling attacks detection method based on SVM-KNN. Comput Eng Appl 49(22):7–10
Wu Z, Wu J, Cao J, Tao D (2012) HySAD: a semi-supervised hybrid shilling attack detector for trustworthy product recommendation. In: Proceedings of the 18th ACM SIGKDD international conference on knowledge discovery and data mining, Beijing, China, pp 985–993
Zahra S, Ghazanfar MA, Khalid A, Azam MA, Naeem U, Prugel-Bennett A (2015) Novel centroid selection approaches for kmeans-clustering based recommender systems. Inf Sci 320(C):156–189
Mehta B, Hofmann T, Fankhauser P (2007) Lies and propaganda: detecting spam users in collaborative filtering. In: International conference on intelligent user interfaces, Honolulu, 28–31 Jan 2007, pp 14–21
Mehta B (2007) Unsupervised shilling detection for collaborative filtering. In: AAAI conference on artificial intelligence, Vancouver, 22–26 July, pp 1402–1407
Sheugh L, Alizadeh SH (2018) A novel 2D-graph clustering method based on trust and similarity measures to enhance accuracy and coverage in recommender systems. Inf Sci 432:210–230
Ferrari DG, Castro LND (2015) Clustering algorithm selection by meta-learning systems: a new distance-based problem characterization and ranking combination methods. Elsevier, Amsterdam
Agrawal R, Imielinski T, Swami AN (1993) Mining association rules between sets of items in large databases. In: Proceedings of the 1993 ACM SIGMOD international conference on management of data, Washington, DC, USA, 25–28 May 1993, pp 207–216
Brin S, Motwani R, Silverstein C (1997) Beyond market baskets. ACM Sigmod Rec 26(2):265–276
Taha A, Hadi AS (2016) Pair-wise association measures for categorical and mixed data. Inf Sci 346–347:73–89
Kohavi R, John GH (1997) Wrappers for feature subset selection. Artif Intell 97(1–2):273–324
O’Mahony M, Hurley N, Kushmerick N, Silvestre G (2004) Collaborative recommendation: a robustness analysis. ACM Trans Internet Technol 4(4):344–377
Burke R, OMahony MP, Hurley NJ (2011) Robust collaborative recommendation. Springer, Berlin
Maratea A, Petrosino A, Manzo M (2014) Adjusted f-measure and kernel scaling for imbalanced data learning. Inf Sci 257(2):331–341
Acknowledgements
This paper is supported by the Natural Science Foundation of Guangdong Province, China (No. 2018A030313203), the Scientific Research Foundation of Henan Normal University (qd15135) and Research Grants for Universities and Colleges in Henan (17A520037).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Chen, K., Chan, P.P.K., Zhang, F. et al. Shilling attack based on item popularity and rated item correlation against collaborative filtering. Int. J. Mach. Learn. & Cyber. 10, 1833–1845 (2019). https://doi.org/10.1007/s13042-018-0861-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13042-018-0861-2