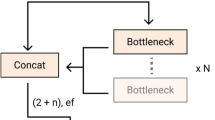
Abstract
Internet of Things (IoT) can provide the interconnection and data sharing among devices, vehicles, buildings via various sensors with the development of 5G, and it has been widely used in different services such as e-commerce, heath-care, smart buildings. In the meantime, various cyber-attacks for IoT have increased and caused huge losses. Lots of security mechanisms are rapidly being proposed to prevent the potentially malicious attackers for IoT, in which machine learning especially deep learning (DL) as increasingly popular solution for security has been implemented in intrusion detection system (IDS) and others. However, the lack of enough datasets prevents the application of IDS in 5G IoT system. As one of fundamental components of IDS, network traffic classification shows a discretization, individualization and fine-grained trend which derives the different personalized classification methods for different requirements and scenarios. In this case, the data-driven DL faces the following challenges. First, there are only a few labeled datasets in the various personalized application scenarios, which undoubtedly limits the deployment of DL classification. Second, not all scenarios have rich computing capability for that training a neural network requires lots of computing resources. Therefore, this paper proposes a traffic classification method based on deep transfer learning for 5G IoT scenarios with scarce labeled data and limited computing capability, and trains the classification model by weight transferring and neural network fine-tuning. Different from the previous work that extract artificially designed features, the proposed method retains the end-to-end learning performance of DL and reduces the risk of suffering concept drift to reduce human intervention. Experimental results show that when only 10% of dataset are used to label the data samples, the classification accuracy is close to the results of full training dataset.









Similar content being viewed by others
References
Scully P (2020) Top 10 IoT applications in 2020. https://iot-analytics.com/top-10-iot-applications-in-2020/. Accessed 5 June 2020
Hellaoui H, Koudil M, Bouabdallah A (2020) Energy efficiency in security of 5G-based IoT: an end-to-end adaptive approach. IEEE Internet Things J 7(7):6589–6602
Manjia TS, Hadis K, Petros S (2020) Machine learning based solutions for security of internet of things (IoT): a survey. J Netw Comput Appl 161:102630
Insider Business (2015) Report on how the internet of things will explode by 2020. http://www.businessinsider.com/. Accessed 5 June 2020
Monika R, Yun TG, Chambers Jonathon A (2020) Multi-objective-based feature selection for DDoS attack detection in IoT networks. IET Netw 9(3):120–127
Zarpelão BB, Miani RS, Kawakani CT, de Alvarenga SC (2017) A survey of intrusion detection in internet of things. J Netw Comput Appl 84:25–37
Chaabouni N, Mosbah M, Zemmari A, Sauvignac C, Faruki P (2019) Network intrusion detection for IoT security based on learning techniques. IEEE Commun Surv Tutor 21(3):2671–2701
Al-Garadi MA, Mohamed A, Al-Ali AK, Du X, Ali I, Guizani M (2020) A survey of machine and deep learning methods for internet of things (IoT) security. IEEE Commun Surv Tutor 22(3):1646–1685
Hussain F, Hussain R, Hassan SA, Hossain E (2020) Machine learning in IoT security: current solutions and future challenges. IEEE Commun Surv Tutor 22(3):1686–1721
Shailendra R, Jong HP (2018) Semi-supervised learning based distributed attack detection framework for IoT. Appl Soft Comput 72:79–89
Hodo E, Bellekens XJA, Hamilton AW, Dubouilh P-L, Iorkyase E, Tachtatzis C, Atkinson RC (2016) Threat analysis of IoT networks using artificial neural network intrusion detection system. In: 2016 international symposium on networks, computers and communications, ISNCC 2016, Yasmine Hammamet, Tunisia, May 11–13, 2016. IEEE, pp 1–6
Hosseinpour Farhoud, Amoli Payam, Plosila Juha, Hämäläinen Timo, Tenhunen Hannu (2016) An intrusion detection system for fog computing and IoT based logistic systems using a smart data approach. Int J Dig Content Technol Appl 10:12
Moustafa N, Turnbull B, Choo K-KR (2019) An ensemble intrusion detection technique based on proposed statistical flow features for protecting network traffic of internet of things. IEEE Internet Things J 6(3):4815–4830
Roopak M, Tian GY, Chambers JA (2019) Deep learning models for cyber security in IoT networks. In: IEEE 9th annual computing and communication workshop and conference, CCWC 2019, Las Vegas, NV, USA, January 7–9, 2019. IEEE, pp 452–457
Rezaei Shahbaz, Liu Xin (2019) Deep learning for encrypted traffic classification: an overview. IEEE Commun Mag 57(5):76–81
Sun Guanglu, Liang Lili, Chen Teng, Xiao Feng, Lang Fei (2018) Network traffic classification based on transfer learning. Comput Electr Eng 69:920–927
Gomes JVP, Inácio PRM, Pereira M, Freire MM, Monteiro PP (2013) Detection and classification of peer-to-peer traffic: a survey. ACM Comput Surv 45(3):30:1–30:40
Buyun Q, Zhang Z, Zhu X, Meng D (2015) An empirical study of morphing on behavior-based network traffic classification. Secur Commun Netw 8(1):68–79
Hu Y, Zou F, Li L, Yi P (2020) Traffic classification of user behaviors in tor, i2p, zeronet, freenet. In: Guojun W, Ryan KLK, Bhuiyan MZA, Yi P (eds) 19th IEEE international conference on trust, security and privacy in computing and communications, TrustCom 2020, Guangzhou, China, December 29, 2020–January 1, 2021. IEEE, pp 418–424
Wang W, Zhu M, Wang J, Zeng X, Yang Z (2017) End-to-end encrypted traffic classification with one-dimensional convolution neural networks. In: 2017 IEEE international conference on intelligence and security informatics, ISI 2017, Beijing, China, July 22–24, 2017, pp 43–48
Wang W, Zhu M, Zeng X, Ye X, Sheng Y (2017) Malware traffic classification using convolutional neural network for representation learning. In: 2017 international conference on information networking, ICOIN 2017, Da Nang, Vietnam, January 11–13, 2017, pp 712–717
Chen Z, He K, Li J, Geng Y (2017) Seq2img: a sequence-to-image based approach towards IP traffic classification using convolutional neural networks. In: 2017 IEEE international conference on big data, BigData 2017, Boston, MA, USA, December 11–14, 2017, pp 1271–1276
Zhou H, Wang Y, Ye M (2018) A method of CNN traffic classification based on sppnet. In: 14th international conference on computational intelligence and security, CIS 2018, Hangzhou, China, November 16–19, 2018. IEEE Computer Society, pp 390–394
Zou Z, Ge J, Zheng H, Wu Y, Han C, Yao Z (2018) Encrypted traffic classification with a convolutional long short-term memory neural network. In: 20th IEEE international conference on high performance computing and communications; 16th IEEE international conference on smart city; 4th IEEE international conference on data science and systems, HPCC/SmartCity/DSS 2018, Exeter, United Kingdom, June 28–30, 2018. IEEE, pp 329–334
Lotfollahi M, Siavoshani MJ, Zade RSH, Saberian M (2020) Deep packet: a novel approach for encrypted traffic classification using deep learning. Soft Comput 24(3):1999–2012
Cui S, Jiang B, Cai Z, Lu Z, Liu S, Liu J (2019) A session-packets-based encrypted traffic classification using capsule neural networks. In: Zheng X, Laurence TY, Pavan B, Tao L, Keqin L, Albert YZ (eds) 21st IEEE international conference on high performance computing and communications; 17th IEEE international conference on smart city; 5th IEEE international conference on data science and systems, HPCC/SmartCity/DSS 2019, Zhangjiajie, China, August 10–12, 2019. IEEE, pp 429–436
Casino F, Choo K-KR, Patsakis C (2019) HEDGE: efficient traffic classification of encrypted and compressed packets. IEEE Trans Inf Forensics Secur 14(11):2916–2926
Liu C, He L, Xiong G, Cao Z, Li Z (2019) Fs-net: a flow sequence network for encrypted traffic classification. In: 2019 IEEE conference on computer communications, INFOCOM 2019, Paris, France, April 29–May 2, 2019, pp 1171–1179
Ancy S, Paulraj D (2020) Handling imbalanced data with concept drift by applying dynamic sampling and ensemble classification model. Comput Commun 153:553–560
Sheikhpour R, Sarram MA, Gharaghani S, Chahooki MAZ (2017) A survey on semi-supervised feature selection methods. Pattern Recognit 64:141–158
Chandrashekar Girish, Sahin Ferat (2014) A survey on feature selection methods. Comput Electr Eng 40(1):16–28
Xue B, Cervante L, Shang L, Browne WN, Zhang M (2013) Multi-objective evolutionary algorithms for filter based feature selection in classification. Int J Artif Intell Tools 22(4):1350024
Sinno JP, Qiang Y (2010) A survey on transfer learning. IEEE Trans Knowl Data Eng 22(10):1345–1359
Cai L, Jing X, Sun S, Huang H, Chen N, Lu Y (2013) P2P traffic identification based on transfer learning. In: 2013 IEEE international conference on granular computing, GrC 2013, Beijing, China, December 13–15, 2013, pp 22–26
Yosinski J, Clune J, Bengio Y, Lipson H (2014) How transferable are features in deep neural networks? In: Advances in neural information processing systems 27: annual conference on neural information processing systems 2014, December 8–13 2014, Montreal, Quebec, Canada, pp 3320–3328
Wang Z (2015) The applications of deep learning on traffic identification. In: 2015 Blackhat US, pp 1–10
Sun Guanglu, Liang Lili, Chen Teng, Xiao Feng, Lang Fei (2018) Network traffic classification based on transfer learning. Comput Electr Eng 69:920–927
Rezaei S, Liu X (2019) How to achieve high classification accuracy with just a few labels: a semisupervised approach using sampled packets. In: Advances in data mining—applications and theoretical aspects, 19th industrial conference, ICDM 2019, New York, USA, July 17–July 21, 2019, pp 28–42
Tan M, Le Q (2019) EfficientNet: rethinking model scaling for convolutional neural networks. In: Kamalika C, Ruslan S (eds) Proceedings of the 36th international conference on machine learning, volume 97 of Proceedings of machine learning research, Long Beach, California, USA, 09–15 June. PMLR, pp 6105–6114
Kolesnikov A, Beyer L, Zhai X, Puigcerver J, Yung J, Gelly S, Houlsby N (2020) Big Transfer (BiT): general visual representation learning. In: Andrea V, Horst B, Thomas B, Jan-Michael F (eds) Computer vision—ECCV 2020. Springer International Publishing, Cham, pp 491–507
Wang W, Lu D (2019) USTC-TFC2016. https://github.com/yungshenglu/USTC-TFC2016/. Accessed 5 June 2020
He Kaiming, Zhang Xiangyu, Ren Shaoqing, Sun Jian (2015) Spatial pyramid pooling in deep convolutional networks for visual recognition. IEEE Trans Pattern Anal Mach Intell 37(9):1904–1916
Draper-Gil G, Lashkari AH, Mamun MSI, Ghorbani AA (2019) UNB VPN-nonVPN dataset (ISCXVPN2016). https://www.unb.ca/cic/datasets/vpn.html/. Accessed 5 June 2020
Casino F (2021) traffic analysis. https://github.com/francasino/traffic_analysis/. Accessed 5 June 2020
Liu C, Cao Z, Xiong G, Gou G, Yiu S-M, He L (2018) Mampf: encrypted traffic classification based on multi-attribute Markov probability fingerprints. In: 26th IEEE/ACM international symposium on quality of service, IWQoS 2018, Banff, AB, Canada, June 4–6, 2018. IEEE, pp 1–10
Aceto Giuseppe, Ciuonzo Domenico, Montieri Antonio, Pescapè Antonio (2019) Mobile encrypted traffic classification using deep learning: experimental evaluation, lessons learned, and challenges. IEEE Trans Netw Serv Manag 16(2):445–458
Moore AW, Zuev D (2005) Internet traffic classification using Bayesian analysis techniques. In: Derek LE, Carey LW, Sem CB, John CSL (eds) Proceedings of the international conference on measurements and modeling of computer systems, SIGMETRICS 2005, June 6–10, 2005, Banff, Alberta, Canada. ACM, pp 50–60
Draper-Gil G, Lashkari AH, Mamun MSI, Ghorbani AA (2016) Characterization of encrypted and VPN traffic using time-related features. In: Olivier C, Steven F, Paolo M (eds) Proceedings of the 2nd international conference on information systems security and privacy, ICISSP 2016, Rome, Italy, February 19–21, 2016. SciTePress, pp 407–414
Xiong P, Cui B, Cheng Z (2020) Anomaly network traffic detection based on deep transfer learning. In: Leonard B, Aneta P-M, Hyunhee P (eds) Innovative mobile and internet services in ubiquitous computing—Proceedings of the 14th international conference on innovative mobile and internet services in ubiquitous computing (IMIS-2020), Lodz, Poland, 1–3 July, 2020, volume 1195 of Advances in intelligent systems and computing. Springer, pp 384–393
He K, Zhang X, Ren S, Sun J (2016) Deep residual learning for image recognition. In: 2016 IEEE conference on computer vision and pattern recognition, CVPR 2016, Las Vegas, NV, USA, June 27–30, 2016. IEEE Computer Society, pp 770–778
Acknowledgements
The authors would like to thank the anonymous reviewers for their valuable comments which helped them to improve the content, organization, and presentation of this paper.
Funding
This research was supported by National Key Research and Development Program (2018YFE0206800) and the Soonchunyhang University Research Fund.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Guan, J., Cai, J., Bai, H. et al. Deep transfer learning-based network traffic classification for scarce dataset in 5G IoT systems. Int. J. Mach. Learn. & Cyber. 12, 3351–3365 (2021). https://doi.org/10.1007/s13042-021-01415-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13042-021-01415-4