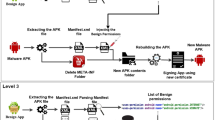
Abstract
The growth of Android mobile platform has led to the increase in the number of malicious applications. Malware creators are ahead of the malware detectors. In this paper, we present eight techniques of hiding a malicious Android application inside images (PNG/JPEG) by using methods such as Concatenation, Obfuscation, Cryptography, and Steganography separately and in conjunction. The image containing the malicious application is stored in the resources of another Android application. After hiding the malicious application using these techniques, we evaluated the vulnerability of ten popular and freely downloadable commercial Android anti-malwares towards them. The results were alarming as only one of them was able to detect two hiding techniques in which the malicious Android application (or its obfuscated version) was hidden by concatenating it at the end of an image and rest all the other anti-malwares were blind towards the eight hiding techniques. If the malicious Android application (or its obfuscated version) is not hidden inside an image but resides as it is in the resources of another Android application, seven out of ten anti-malwares flagged such applications as malicious. Such an evaluation provides a metric for measurement of the available defense against evolving Android malware and also aids in improving the state of the art of the Android malware detection systems.

Similar content being viewed by others
References
Aafer Y, Du W, Yin H (2013) DroidAPIMiner: Mining API-level features for robust malware detection in android. In: Security privacy in communication networks. Springer, Berlin, pp 86–103
Almin SB, Chatterjee M (2015) A novel approach to detect android malware. Procedia Comput Sci 45:407–417
Android Studio (2013) Android developers. http://developer.android.com/tools/studio/index.html. Accessed Oct 2017
AndroMalShare (2013) AndroMalShare. http://andromalshare.androidmalware.net:8080/#home. Accessed Feb 2016
Apvrille A, Albertini A (2014) Hide android applications in images. In: Paper presented at the BlackHat Europe
Apvrille A, Nigam R (2014) Virus bulletin: obfuscation in android malware, and how to fight back. https://www.virusbulletin.com/virusbulletin/2014/07/obfuscation-android-malware-and-how-fight-back. Accessed Jan 2016
Bloisi D, Iocchi, L (2007) Image based steganography and cryptography. In: 2nd International conference on computer vision theory and application—VISAPP ‘07, 2007. pp 127–134
Boehm B (2014) StegExpose-A Tool for Detecting LSB Steganography arXiv preprint arXiv:14106656
Burguera I, Zurutuza U, Nadjm-Tehrani S (2011) Crowdroid: behavior-based malware detection system for android. In: Proceedings on 1st ACM work. Security privacy in smartphones mobiel devices—SPSM’11, 2011. ACM, New York, pp 15–26
ClassLoader (2008) ClassLoader | Android Developers. http://developer.android.com/reference/java/lang/ClassLoader.html. Accessed Jan 2016
Collberg C, Thomborson C, Low D (1997) A taxonomy of obfuscating transformations. Technical Report 148 Department of Computer Science, The University of Auckland
DexClassLoader (2009) DexClassLoader | Android Developers. http://developer.android.com/reference/dalvik/system/DexClassLoader.html. Accessed Jan 2016
Dini G, Martinelli F, Saracino A, Sgandurra D (2012) MADAM: a multi-level anomaly detector for android malware. In: Lecture Notes Computer Science (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics). 7531 LNCS, 2012. Springer, Berlin, pp 240–253
Enck W et al. (2014) TaintDroid: an information-flow tracking system for realtime privacy monitoring on smartphones ACM Transactions on Computer Systems (TOCS) 32:5
Enck W, Ongtang M, McDaniel P (2009) On lightweight mobile phone application certification. In: Proceedings on 16th ACM Conf. Computer Communication Security—CCS’09, 2009. ACM, New York, pp 235–245
FakeRegSMS.B (2012) F-Secure Mobile Threat Report Q1 2012. https://www.f-secure.com/documents/996508/1030743/Mobile+Threat+Report+Q1+2012.pdf
Falsina L (2015) Grab’n run: practical and safe dynamic code loading in Android. http://hdl.handle.net/10589/106725
Google Play Store (2012). https://play.google.com/store?hl=en
IDC (2015) Smartphone OS Market Share, 2015 Q2 http://www.idc.com/prodserv/smartphone-os-market-share.jsp. Accessed Jan 2016
java.lang.reflect (2008) java.lang.reflect | Android Developers. http://developer.android.com/reference/java/lang/reflect/package-summary.html. Accessed Jan 2016
javax.crypto (2008) javax.crypto | Android Developers. http://developer.android.com/reference/javax/crypto/package-summary.html. Accessed Jan 2016
Johnson NF, Jajodia S (1998) Exploring steganography: seeing the unseen. IEEE Comput 31:26–34
Kroustek J (2015) Banking Trojan Vawtrak: Harvesting Passwords Worldwide. AVG. http://now.avg.com/banking-trojan-vawtrak-harvesting-passwords-worldwide/. Accessed Feb 2016
Lockheimer H (2012) Android and Security. http://googlemobile.blogspot.in/2012/02/android-and-security.html. Accessed Feb 2016
Moser A, Kruegel C, Kirda E (2007) Limits of static analysis for malware detection. Annu Comput Secur Appl Conf ACSAC 2007:421–430
OpFake (2012) F-Secure Mobile Threat Report Q1 2012. https://www.f-secure.com/documents/996508/1030743/Mobile+Threat+Report+Q1+2012.pdf. Accessed Jan 2016
Ortega. A, Breslin. S (1997) Jpeg decoder
ProGuard (2011) Shrink Your Code and Resources | Android Developers. http://developer.android.com/tools/help/proguard.html. Accessed Jan 2016
Provos N (2001) Defending against statistical steganalysis. Usenix Sec Symp 2001:323–336
Provos N, Honeyman P (2001) Detecting steganographic content on the internet. Center for information technology integration
Quick Heal Quaterly Threat Report Q1 (2015). http://dlupdate.quickheal.com/documents/others/quick_heal_quarterly_threat_report_Q1_2015.pdf
Rastogi V, Chen Y, Jiang X (2013) Droidchameleon: evaluating android anti-malware against transformation attacks. In: Proceedings of the 8th ACM SIGSAC symposium on information, computer and communications security, 2013. ACM, New York, pp 329–334
Sanz B, Santos I, Laorden C, Ugarte-Pedrero X, Bringas PG, Álvarez G (2013) Puma: permission usage to detect malware in android. Adv Intell Syst Comput AISC 189:289–298
Shabtai A, Kanonov U, Elovici Y, Glezer C, Weiss Y (2012) “Andromaly”: a behavioral malware detection framework for android devices. J Intell Inf Syst 38:161–190
Suarez-Tangil G, Tapiador JE, Peris-Lopez P (2014) Stegomalware: Playing hide and seek with malicious components in smartphone apps. In: Proceedings on 10th international conference on information security cryptology, 2014. Springer, Berlin, pp 496–515
Weeks JR (1998) Jpeg encoder. Independent JPEG Group
Wu D-J, Mao C-H, Wei T-E, Lee H-M, Wu K-P (2012) Droidmat: android malware detection through manifest and api calls tracing. In: Proceedings on 7th Asia joint conference on information security Asia JCIS 2012. IEEE, pp 62–69
Wyatt T (2012) Security Alert: New Variants of Legacy Native (LeNa) Identified. https://blog.lookout.com/blog/2012/04/03/security-alert-new-variants-of-legacy-native-lena-identified/. Accessed Jan 2016
Zhauniarovich Y, Ahmad M, Gadyatskaya O, Crispo B, Massacci F (2015) StaDynA: addressing the problem of dynamic code updates in the security analysis of android applications. In: Proceedings on 5th ACM Conference on Data Application Security Privacy—CODASPY ‘15, 2015. ACM, New York, pp 37–48
Zhou Y, Wang Z, Zhou W, Jiang X (2012) Hey, you, get off of my market: detecting malicious apps in official and alternative android markets. In: Proceedings on 19th annual network distribution system security symposium (NDSS), 2012. pp 1–13
Zhou W, Wang Z, Zhou Y, Jiang X (2014) Divilar: diversifying intermediate language for anti-repackaging on android platform. In: Proceedings on 4th ACM conference on data application security privacy—CODASPY ‘14 2014. ACM, New York, pp 199–210
Acknowledgements
Prof. Sunil K. Muttoo is thankful to University of Delhi for the grant received under the R & D scheme of University of Delhi (Grant No. RC/2015/9677). Ms. Shikha Badhani is grateful to the Principal, Maitreyi College, University of Delhi, New Delhi-110021 for granting study leave to pursue research.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Badhani, S., Muttoo, S.K. Evading android anti-malware by hiding malicious application inside images. Int J Syst Assur Eng Manag 9, 482–493 (2018). https://doi.org/10.1007/s13198-017-0692-7
Received:
Revised:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13198-017-0692-7