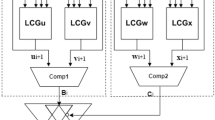
Abstract
While the cryptographic modules used in modern embedded systems may employ mathematically secure algorithms, an attacker may still be able to compromise the security of a design using side-channel analysis. Side-channel attacks use leaked information in order to make inferences regarding the value of the secret key used for encryption. Statistical power analysis attacks are a class of side-channel attack which target power consumption as a leakage vector and apply statistical analysis to collected traces. As these attacks have been proven to be effective on a variety of hardware implementations, there exists a corresponding body of research regarding countermeasures. This work examines several statistical power analysis attack countermeasures in the literature and groups them into three broad categories consisting of secure logic styles, alterations to existing functional modules, and the inclusion of additional modules designed to enhance security. While a variety of options are available to a designer, there will always be a corresponding trade-off in terms of overhead factors like additional power consumption and area. As such, this work seeks to document and classify several of the approaches presented in the literature in order to help designers better select a countermeasure suited to their needs.




































Similar content being viewed by others
References
Kocher, P., Lee, R., McGraw, G., Raghunathan, A., Ravi, S.: Security as a new dimension in embedded system design. In: Proceedings of the Design Automation Conference, pp. 753–760 (2004)
Kocher, P., Jaffe, J., Jun, B.: Differential power analysis. In: Advances in Cryptology—(CRYPTO ’99). LNCS, vol. 1666, pp. 388–397 (1999)
Alioto, M., Polie, M., Rocchi, S.: Power analysis attacks to cryptographic circuits: a comparative analysis of DPA and CPA. In: Proceedings of the ICM ’08, pp. 333–336 (2008)
Gandolfi, K., Mourter, C., Oliver, F.: Electromagnetic analysis: concrete results. In: Proceedings of the CHES 2001. LNCS, vol. 2162, pp. 251–261 (2001)
Kocher, P.: Timing attacks on implementations of Diffie–Hellman, RSA, DSS, other systems. In: Proceedings of the Advances in Cryptology—CRYPTO ’96, pp. 104–113 (1996)
Brier, E., Claiver, C., Olivier, F.: Correlation power analysis with a leakage model. In: CHES 2004. LNCS , vol. 3156, pp. 16–29 (2004)
Kocher, P., Jaffe, J., Jun, B., Rohatgi, P.: Introduction to differential power analysis. J. Cryptogr. Eng. 1(1), 5–27 (2011)
Mangard, S., Oswald, E., Popp, T.: Power Analysis Attacks, Revealing the Secrets of Smart Cards. Springer, New York (2007)
Standaert, F.-X., Gierlichs, B., Verbauwhede, I.: Partition vs. comparison side-channel distinguishers: an empirical evaluation of statistical tests for univariate side-channel attacks against two unprotected CMOS devices. In: Proceedings of the ICISC 2008, pp. 253–267 (2009)
Waddle, J., Wagner, D.: Towards efficient second-order power analysis. In: Proceedings of the CHES 2004. LNCS, vol. 3156, pp. 1–15 (2004)
Messerges, T.S.: Using second-order power analysis to attack DPA resistant software. In: Proceedings of the CHES 2000. LNCS, vol. 1965, pp. 238–251 (2000)
Menicocci, R., Simonetti, A., Scotti, G., Trifiletti, A.: On practical second-order power analysis attacks for block ciphers. In: Proceedings of the ICICS 2010. LNCS, vol. 6476, pp. 155–170 (2010)
Oswald, E., Mangard, S., Herbst, C., Tillich, S.: Practical second-order DPA attacks for masked smart card implementations of block ciphers. In: Proceedings of the CT-RSA 2006. LNCS, vol. 3860, pp. 192–207 (2006)
Standaert, F.-X., Veyrat-Charvillon, N., Oswald, E., Gierlichs, B., Medwed, M., Kasper, M., Mangard, S.: The world is not enough: another look on second-order DPA. In: Advances in cryptology—ASIACRYPT 2010. Proceedings of the 16th International Conference on the Theory and Application of Cryptology and Information Security, pp. 112–129 (2010)
Lu, J., Pan, J., den Hartog, J.: Principles on the security of AES against first and second-order differential power analysis. In: Proceedings of the ACNS 2010. LNCS, vol. 6123, pp. 168–185 (2010)
Alioto, M., Giancane, L., Scotti, G., Trifiletti, A.: Leakage power analysis attacks: a novel class of attacks to nanometer cryptographic circuits. IEEE Trans. Circuits Syst. I Reg. Pap. 57(2), 355–367 (2010)
Verbauwhede, I.M., Tiri, K.J.V.: Dynamic and Differential CMOS Logic with Signal Independent Power Consumption to Withstand Differential Power Analysis. US Patent 7,417,468 (2009)
Tiri, K., Verbauwhede, I.: A logic level design methodology for a secure DPA resistant ASIC or FPGA implementation. In: Proceedings of the DATE 2004, vol. 1, pp. 246–251 (2004)
Bucci, M., Giancane, L., Luzzi, R., Trifiletti, A.: Three-phase dual-rail pre-charge logic. In: Proceedings of the CHES 2006. LNCS, vol. 4249, pp. 232–241 (2006)
Bucci, M., Giancane, L., Luzzi, R., Trifiletti, A.: A Flip-flop for the DPA resistant three-phase dual-rail pre-charge logic family. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 20(11), 2128–2132 (2012)
Kim, H., Rozic, V., Verbauwhede, I.: Three phase dynamic current mode logic: a more secure DyCML to achieve a more balanced power consumption. In: Proceedings of the WISA. LNCS, vol. 7690, pp. 68–81 (2012)
Allam, M.W., Elmasry, M.I.: Dynamic current mode logic (DyCML): a new low-power high-performance logic style. IEEE J. Solid State Circuits 36(3), 550–558 (2001)
Bharath, L.N., Kumar, G.: A novel countermeasure for power attacks. In: Students Conference on Engineering and Systems, pp. 1–4 (2013)
Popp, T., Mangard, S.: Masked dual-rail pre-charge logic: DPA-resistance without routing constraints. In: Proceedings of the CHES 2005. LNCS, vol. 3659, pp. 172–186 (2005)
Schaumont, P., Tiri, K.: Masking and dual-rail logic don’t add up. In: Proceedings of the CHES 2007. LNCS, vol. 4727, pp. 95–106 (2007)
Razafindraibe, A., Robert, M., Maurine, P.: Improvement of dual rail logic as a countermeasure against DPA. In: Proceedings of the 2007 IFIP International Conference on VLSI, pp. 270–275 (2007)
Soares, R., Calazans, N., Lomne, V., Maurine, P., Torres, L., Robert, M.: Evaluating the robustness of secure triple track logic through prototyping. In: Proceedings of the 2008 SBCCI Symposium on Integrated Circuits and System Design, pp. 193–198 (2008)
Zhu, N.-H., Zhou, Y.-J., Liu, H.-M.: A standard cell-based leakage power analysis attack countermeasure using symmetric dual-rail logic. J. Shanghai Jiaotong Univ. Sci. 19(2), 169–172 (2014)
He, W., Otero, A., de la Torre, E., Riesgo, T.: Automatic generation of identical routing pairs for FPGA implemented dpl logic. In: ReConFig 2012 , pp. 1–6 (2012)
Nassar, M., Bhasin, S., Danger, J.-L., Duc, G., Guilley, S.: BCDL: a high speed balanced DPL for FPGA with global precharge and no early evaluation. In: Proceedings of the DATE 2010, pp. 1–6 (2010)
Baddam, K., Zwolinski, M.: Divided backend duplication methodology for balanced dual rail routing. In: Proceedings of the CHES 2008. LNCS, vol. 5154, pp. 396–410 (2008)
Yu, P., Schaumont, P.: Secure FPGA circuits using controlled placement and routing. In: 5th IEEE/ACM/IFIP CODES+ ISSS, pp. 45–50 (2007)
Kaps, J.-P., Velegalati, R.: DPA resistant AES on FPGA using partial DDL. In: Proceedings of the 2010 IEEE FCCM, pp. 273–280 (2010)
Velegalati, R., Kaps, J.-P.: Improving security of SDDL designs through interleaved placement on xilinx FPGAs. In: Proceedings of the FPL 2011, pp. 506–511 (2011)
Sauvage, L., Nassar, M., Guilley, S., Flament, F., Danger, J.-L., Mathieu, Y.: Exploiting dual-output programmable blocks to balance secure dual-rail logics. Int. J. Reconfigurable Comput. 2010, 1–12 (2010)
Altera Corporation (2011) Stratix II device handbook, vol. 1, version 4.5. https://www.altera.com/content/dam/altera-www/global/en_US/pdfs/literature/hb/stx2/stx2_sii5v1.pdf. Accessed 6 June 2016
Monteiro, C., Takahashi, Y., Sekine, T.: Charge-sharing symmetric adiabatic logic in countermeasure against power analysis attacks at cell level. Microelectron. J. 44(6), 496–503 (2013)
Sana, P.K., Satyam, M.: An energy efficient secure logic to provide resistance against differential power analysis attacks. In: Proceedings of the ISED, pp. 61–65 (2010)
Choi, B.-D., Kim, K.E., Chung, K.-S., Kim, D.K.: Symmetric adiabatic logic circuits against differential power analysis. ETRI J. 32(1), 166–168 (2010)
Avital, M., Dagan, H., Keren, O., Fish, A.: Randomized multitopology logic against differential power analysis. IEEE Trans. VLSI Syst. 99, 1–10 (2014)
Bouesse, G.F., Renaudin, M., Dumont, S., Germain, F.: DPA on quasi delay insensitive asynchronous circuits: formalization and improvement. In: Proceedings of the IEEE DATE ’05, vol. 1, pp. 424–429 (2005)
Bouesse, G.F., Sicard, G., Renaudin, M.: Path swapping method to improve DPA resistance of quasi delay insensitive asynchronous circuits. In: Proceedings of the CHES 2006. LNCS, vol. 4249, pp. 384–398 (2006)
Bouesse, G.F., Renaudin, M., Sicard, G.: Improving DPA resistance of quasi delay insensitive circuits using randomly time-shifted acknowledgment signals. IFIP Adv. Inf. Commun. Technol. 240, 11–24 (2007)
Golic, J.D.: Techniques for random masking in hardware. IEEE Trans. Circuits Syst. Regul. Pap 54(2), 291–300 (2007)
Mizuno, H., Iwai, K., Tanaka, H., Kurokawa, T.: A correlation power analysis countermeasure for Enocoro-128 v2 using random switching logic. In: ICNC 2012, pp. 326–328 (2012)
Bonnecaze, A., Liardet, P., Venelli, A.: AES side-channel countermeasure using random tower field constructions. Des. Codes Cryptogr. 69(3), 331–349 (2013)
Wolkerstorfer, J., Oswald, E., Lamberger, M.: An ASIC implementation of the AES S-boxes. In: Proceedings of the Topics in Cryptology—CT-RSA 2002. LNCS, vol. 2271, pp. 67–78 (2002)
Canright, D., Batina, L.: A very compact “perfectly masked” S-box for AES. In: ACNS 2008, pp. 446–459 (2008)
Oswald, E., Mangard, S., Pramstaller, N., Rijmen, V.: A side-channel analysis resistant description of the AES S-box. In: Fast Software Encryption. LNCS, vol. 3557, pp. 413–423 (2005)
Nikova, S., Rechberger, C., Rijmen, V.: Threshold implementations against side-channel attacks and glitches. In: ICICS 2006. LNCS, vol. 4307, pp. 529–545 (2006)
Maghrebi, H., Prouff, E., Guilley, S., Danger, J.-L.: A first-order leak-free masking countermeasure. In: CT-RSA 2012. LNCS, vol. 7178, pp. 156–170 (2012)
Maghrebi, H., Guilley, S., Prouff, E., Danger, J.-L.: Register leakage masking using gray code. In: Proceedings of the Host 2012, pp. 37–42 (2012)
Maghrebi, H., Guilley, S., Danger, J.-L.: Leakage squeezing countermeasure against high-order attacks. In: WISTP 2011. LNCS, vol. 6633, pp. 208–223 (2011)
Sasdrich, P., Mischke, O., Moradi, A., Guneysu, T.: Side-channel protection by randomizing look-up tables on reconfigurable hardware—pitfalls of memory primitives. In: COSADE 2015, Berlin, Germany, April 13–14 (2015) (to appear)
Rostovtsev, A.G., Shemyakina, O.V.: AES side channel attack protection using random isomorphisms. In: Cryptology e-Print Archive (2005)
Jungk, B., Stottinger, M., Gampe, J., Reith, S., Huss, S.A.: Side-channel resistant AES architecture utilizing randomized composite field representations. In: Proceedings of the FPT 2012, pp. 125–128 (2012)
Lee, J.-W., Hsiao, J.-H., Chang, H.-C., Lee, C.-Y.: An efficient DPA countermeasure with randomized montgomery operations for DF-ECC processor. IEEE Trans. Circuits Syst. II Exp. Briefs 59(5), 287–291 (2012)
Mazumdar, B., Mukhopadhyay, D., Sengupta, I.: Design and implementation of rotation symmetric S-boxes with high nonlinearity and high DPA resilience. In: Proceedings of the IEEE HOST 2013, pp. 87–92 (2013)
Shah, S., Velegalati, R., Kaps, J.-P., Hwang, D.: Investigation of DPA resistance of block RAMs in cryptographic implementations on FPGAs. In: Proceedings of the 2010 International Conference on Reconfigurable Computing and FPGAs, pp. 274–279 (2010)
McEvoy, R.P., Tunstall, M., Whelan, C., Murphy, C.C., Marnane, W.P.: All-or-nothing transforms as a countermeasure to differential side-channel analysis. Int. J. Inf. Secur. 13(3), 291–304 (2014)
Tiri, K., Schaumont, P., Verbauwhede, I.: Side-channel leakage tolerant architectures. In: Proceedings of the Third International Conference on Information Technology: New Generation, pp. 1–6 (2006)
Saputra, H., Vijaykrishnan, N., Kandemir, M., Irwin, M.J., Brooks, R.: Masking the energy behaviour of encryption algorithms. IEE Proc. Comput. Digit. Tech. 150, 274–284 (2003)
Pedersen, B.B.: Programmable Logic Device with Improved Security. US Patent 8,255,702 (2012)
Lu, Y., O’Neill, M., McCanny, J.: Evaluation of random delay insertion against DPA on FPGAS. ACM Trans. Reconfigurable Technol. Syst 4(1), 11:1–11:20 (2010)
Boey, K.H., Lu, Y., O’Neill, M., Woods, R.: Random clock against differential power analysis. In: Proceedings of the IEEE APCCAS 2010, pp. 756–759 (2010)
Muresan, R., Vahedi, H., Yang, Z., Gregori, S.: Power-smart system-on-chip architecture for embedded cryptosystems. In: Proceedings of the CODES/ISSS ’2005, pp. 184–189 (2005)
Avirneni, N.D.P., Somani, A.K.: Countering power analysis attacks using reliable and aggressive designs. IEEE Trans. Comput. 63(6), 1408–1420 (2014)
Mentens, N., Gierlichs, B., Verbauwhede, I.: Power and fault analysis resistance in hardware through dynamic reconfiguration. In: Proceedings of the CHES 2008. LNCS, vol. 5154, pp. 346–362 (2008)
Sasdrich, P., Moradi, A., Mischke, O., Guneysu, T.: Achieving side-channel protection with dynamic logic reconfiguration on modern FPGAs. In: HOST 2015, McLean, VA, USA, May 5–7, 2015 (2015) (to appear)
Baddam, K., Zwolinski, M.: Evaluation of dynamic voltage and frequency scaling as a differential power analysis countermeasure. In: Proceedings of the IEEE International Conference on VLSI Design 2007, pp. 854–859 (2007)
Muresan, R., Gregori, S.: Protection circuit against differential power analysis attacks for smart cards. IEEE Trans. Comput. 57(11), 1540–1549 (2008)
Ratanpal, G.B., Williams, R.D., Blalock, T.N.: An on-chip signal suppression countermeasure to power analysis attacks. IEEE Trans. Dependable Secure Comput. 1(3), 179–188 (2004)
Hubert, G.T.M.: Current Source for Cryptographic Processor. US Patent 7,571,492 (2009)
Seyyedi, S.A., Kamal, M., Noori, H., Safari, S.: Securing embedded processors against power analysis based side channel attacks using reconfigurable architecture. In: Proceedings of the IEEE/IFIP EUC 2011, pp. 255–260 (2011)
Ambrose, J.A., Parameswaran, S., Ignjatovic, A.: MUTE-AES: A multiprocessor architecture to prevent power analysis based side channel attack of the AES algorithm. In: Proceedings of the IEEE/ACM ICCAD 2008, pp. 678–684 (2008)
Zhu, N., Zhou, Y., Liu, H.: Counteracting leakage power analysis attack using random ring oscillators. In: Proceedings of the SNS & PCS 2013, pp. 74–77 (2013)
Mayhew, M., Muresan, R.: On-chip nanoscale capacitor decoupling architectures for hardware security. IEEE Trans. Emerg. Top. Comput. 2(1), 4–15 (2014)
Shamir, A.: Protecting Smart Cards From Power Analysis with Detachable Power Supplies. US Patent 6,507,913 (2003)
Corsonello, P., Perri, S., Margala, M.: An integrated countermeasure against differential power analysis for secure smart-cards. In: Proceedings of the IEEE International Symposium on Circuits System 2006, pp. 5611–5614 (2006)
Tokunaga, C., Blaauw, D.: Securing encryption systems with a switched capacitor current equalizer. IEEE J. Solid State Circuits 45(1), 23–31 (2010)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Mayhew, M., Muresan, R. An overview of hardware-level statistical power analysis attack countermeasures. J Cryptogr Eng 7, 213–244 (2017). https://doi.org/10.1007/s13389-016-0133-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13389-016-0133-6