Abstract
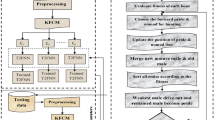
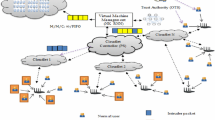
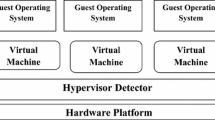
Cloud is a collection of resources such as hardware, networks, servers, storage, applications, and interfaces to provide on-demand services to customers. Since access to cloud is through internet, data stored in clouds are vulnerable to attacks from external as well as internal intruders. In order to preserve privacy of the data in cloud, several intrusion detection approaches, authentication techniques, and access control policies are being used. The common intrusion detection systems are predominantly incompetent to be used in cloud environments. In this paper, the usage of type-2 fuzzy neural network based on genetic algorithm is discussed to incorporate intrusion detection techniques into cloud. These systems are intelligent to gain knowledge of fuzzy sets and fuzzy rules from data to detect intrusions in a cloud environment. Using a standard benchmark data from a cloud intrusion detection dataset experiments are done, tested, and compared with other existing approaches in terms of detection rate accuracy, precision, recall, MSE, and scalability.








Similar content being viewed by others
References
Vieira, K., et al.: Intrusion detection for grid and cloud computing. IT Prof. 12(4), 38–43 (2010)
Xin, W., Ting-lei, H., Xiao-yu, L.: Research on the Intrusion detection mechanism based on cloud computing. In: International conference on intelligent computing and integrated systems (ICISS), Guilin, pp. 125–128 (2010)
Tupakula, U., Varadharajan, V., Akku N.: Intrusion detection techniques for infrastructure as a service cloud. In: IEEE international conference on dependable, autonomic and secure computing, pp. 744–751 (2011)
Dhage, S. et al: Intrusion detection system in cloud computing environment. In: International Conference and Workshop on Emerging Trends in Technology, New York, NY, USA, pp. 235–239 (2011)
Kholidy, H.A., Baiardi, F.: CIDD: A cloud intrusion detection dataset for cloud computing and Masquerade Attacks, Ninth international conference on information technology—New Generations, Las Vegas, Nevada USA, ISBN. 978-0-7695-4654-4 (2012);
Subashini, S., Kavitha, V.: A survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 34(1), 1–11 (2011)
Jin, H. et al: A VMM-based intrusion prevention system in cloud computing environment. J. Supercomput., pp. 1–19 (2011)
Zadeh, L.A.: The concept of a linguistic variable and its application to approximate reasoning I. Inf. Sci. 8(3), 199–249 (1975)
Karnik, N.N., Mendel, J.M.: Centroid of a type-2 fuzzy set. Inf. Sci. 132, 195–220 (2001)
Lin, Faa-Jeng, Chou, Po-Huan, Shieh, Po-Huang, Chen, Syuan-Yi: Robust control of an LUSM-Based XY θ motion control stage using an adaptive interval Type-2 fuzzy neural network. IEEE Trans. Fuzzy Syst. 17(1), 24–38 (2009)
Bhat, A.H., Patra, S., Jena, D.: Machine learning approach for intrusion detection on cloud virtual machines. Int. J. Appl. Innov. Eng. Manag. 2(6), 56–66 (2013)
Shirazi, H.M., Kalaji, Y.: An intelligent intrusion detection system using genetic algorithms and features selection. Majlesi J. Electr. Eng. 4(1), 33–43 (2010)
Gonzalez, A., Herrera, F.: Multi-stage genetic fuzzy systems based on the iterative rule learning approach. Mathw. Soft Comput. 4, 233–249 (1997)
Farag, W.A., Quintana, V.H., Lambert-Torres, G.: A genetic-based neuro-fuzzy approach for modeling and control of dynamical systems. IEEE Trans. Neural Netw. 9(5), 756–767 (1998)
Mamdani, E.H., Assilian, S.: An experiment in linguistic synthesis with a fuzzy logic controller. Int. J. Man Mach. Stud. 7, 1–13 (1975)
Shi, Y., Eberhart, R., Chen, Y.: Implementation of evolutionary fuzzy systems. IEEE Trans. Fuzzy Syst. 7(1), 109–119 (1999)
Bezdek, J.: Pattern Recognition with Fuzzy Objective Function Algorithms. Plenum Press, New York (1981)
Kohonen, T.: Self-Organizing Maps. Springer, New York (1997)
Yager, R., Filev, D.: Generation of fuzzy rules by mountain clustering. J. Intell. Fuzzy Syst. 2(3), 209–219 (1994)
Chiu, S.: Fuzzy model identification based on cluster estimation. J. Intell. Fuzzy Syst. 2, 267–278 (1994)
Kanungo, T., et al.: An efficient k-means clustering algorithm: analysis and implementation. IEEE Trans. Pattern Anal. Mach. Intell 24(7), 881–892 (2002)
Su, M.-C., Chou, C.-H.: A modified version of the K-means algorithm with a distance based on cluster symmetry. IEEE Trans. Pattern Anal. Mach. Intell. 23(6), 674–680 (2001)
Aziz, A.S.A., et al.: Artificial immune system inspired intrusion detection system using genetic algorithm. Informatica 36, 347–357 (2012)
Lin, Y., Cunningham, I.I.I.G.A., Coggeshall, S.V.: Using fuzzy partitions to create fuzzy systems from input-output data and set the initial weights in a fuzzy neural network. IEEE Trans. Fuzzy Syst. 5(4), 614–621 (1997)
Wong, C.-C., Chen, C.-C.: A hybrid clustering and gradient descent approach for fuzzy modeling. IEEE Trans. Syst. Man Cybern. Part B 29(6), 686–693 (1999)
Thawonmas, R., Abe, S.: Function approximation based on fuzzy rules extracted from partitioned numerical data. IEEE Trans. Syst. Man Cybern. 29(4), 525–534 (1999)
Vivekanandan, P., Rajalakshmi, M., Nedunchezhian, R.: An intelligent genetic algorithm for mining classification rules in large datasets. Comput. Inform. 32(1), 1–22 (2013)
Leng, G., McGinnity, T.M., Prasad, G.: Design for self-organizing fuzzy neural networks based on genetic algorithms. IEEE Trans. Fuzzy Syst. 14(6), 755–766 (2006)
Uncu, O., Turksen, I.B.: Discrete interval type 2 fuzzy system models using uncertainty in learning parameters. IEEE Trans. Fuzzy Syst. 15(1), 90–106 (2007)
Juang, C.-F., Tsao, Y.-W.: A self-evolving interval type-2 fuzzy neural network with online structure and parameter learning. IEEE Trans. Fuzzy Syst. 16(6), 1411–1424 (2008)
Castro, J.R., et al.: A hybrid learning algorithm for a class of interval type-2 fuzzy neural networks. Inf. Sci. 179(13), 2175–2193 (2009)
Eucalyptus. http://www.eucalyptus.com
Abraham A., Jain R.: Soft computing models for network intrusion detection systems. In: Classification and Clustering for Knowledge Discovery. Studies in Computational Intelligence, vol. 4, pp. 191–207. Springer, Berlin (2005)
Mostaque Md and Morshedur Hassan (2013); Network intrusion detection system using genetic algorithm and fuzzy logic. Int. J. Innov. Res. Comput. Commun. Eng. 1(7)
Mohammad Sazzadul Hoque, Md. Abdul Mukit and Md. Abu Naser Bikas: An implementation of intrusion detection system using genetic algorithm. Int. J. Netw. Secur. Appl., vol. 4, no. 2 (2012)
Tsang, S. K., Wang, H.: Anomaly intrusion detection using multi-objective genetic fuzzy system and agent-based evolutionary computation framework. In: Proceedings of the Fifth IEEE international conference on data mining (2005)
Shafi, K., Abbass, H.A.: An adaptive genetic-based signature learning system for intrusion detection. Expert Syst. Appl. 36, 12036–12043 (2009)
Mukkamala, S., Sung, A.H., Abraham, A.: Intrusion detection using ensemble of soft computing paradigms, advances in soft computing. Intell. Syst. Des. Appl. 23, 239–248 (2003)
Chung, C.-J., Khatkar, P., Xing, T., Lee, J., Huang, D.: NICE: network intrusion detection and countermeasure selection in virtual network systems. IEEE Trans. Dependable Secure Comput. 10(4), 198–211 (2013)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Raja, S., Ramaiah, S. An Efficient Fuzzy-Based Hybrid System to Cloud Intrusion Detection. Int. J. Fuzzy Syst. 19, 62–77 (2017). https://doi.org/10.1007/s40815-016-0147-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40815-016-0147-3