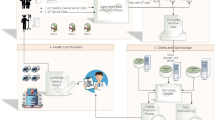
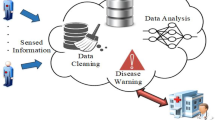
Abstract
Medical Internet of Things (MIoT) plays a vital role in improving people’s health, protection, and treatment. Rather than going to the hospital, it is possible to remotely track patients’ health-related criteria and move them to medical data centers using cloud storage. There is also an exponential rise in the amount of data handled by MIoT devices. This means higher disclosure of confidential data; consequently, data protection and privacy obtained from MIoT devices are major unresolved concerns. As classification systems are growing rapidly, the need to apply machine learning algorithms to large-scale industrial data is also expanding. In this paper, we classify medical data into disease-free individuals from affected ones. To securely store this information in the cloud, we introduce a novel Adaptive Neuro-Fuzzy Inference System (ANFIS) for data protection to improve and determine the degree of security like breaches, data integrity, etc. Results indicate that with the 6.2506e−06 training error and 0.3429 testing error, ANFIS performs extremely well in improving the degree of security parameters for a secure path to the cloud.












Similar content being viewed by others
References
Bai, L., Yang, D., Wang, X., Tong, L., Zhu, N.X., Bai, C.: Chinese experts’ consensus on the internet of things-aided diagnosis and treatment of coronavirus disease 2019 (covid-19). Clinical eHealth of ScienceDirect (2020)
Rehman, S.U., Javed, A.R., Khan, M.U., Nazarwan, M., Farukh, A., Hussien, A.: Personalisedcomfort:a personalised thermal comfort model to predict thermal sensation votes for smart building residents. Enterprise Inf. Syst. (2020). https://doi.org/10.1080/17517575.2020.1852316
Sarwar, M.U., Javed, A.R..: Collaborative health care plan through crowdsource data using ambient application. In: Proceedings of the International Multitopic Conference (INMIC), IEEE, pp 1–6 (2019)
Javed, A.R., Fahad, L.G., Farhan, A.A., Abbas, S., Srivastava, G., Parizi, R.M., Khan, M.S.: Automated cognitive health assessment in smart homes using machine learning. Sustain. Cities Soc. (2020a). https://doi.org/10.1016/j.scs.2020.102572
Javed, A.R., Sarwar, M.U., Beg, M.O., Asim, M., Baker, T., Tawfik, H.: A collaborative healthcare framework for shared healthcare plan with ambient intelligence. Human-centric Comput. Info. Sci. 10(1), 1–21 (2020b)
Jyotheeswari, P., Jeyanthi, N.: Hybrid encryption model for managing the data security in medical internet of things. Int. J. Internet Protoc. Technol. (2020). https://doi.org/10.1504/IJIPT.2020.105049
Usman Sarwar, M., Rehman Javed, A., Kulsoom, F., Khan, S., Tariq, U., Kashif Bashir, A.: Parciv: recognizing physical activities having complex interclass variations using semantic data of smartphone. Pract. Exp. Softw. (2020). https://doi.org/10.1002/spe.2846
Javed, A.R., Sarwar, M.U., Khan, S., Iwendi, C., Mittal, M., Kumar, N.: Analyzing the effectiveness and contribution of each axis of tri-axial accelerometer sensor for accurate activity recognition. Sensors 20(8), 2216 (2020c)
Waurzyniak, P.: Securing manufacturing data in the cloud. Adv. Manuf. (2016)
Shabbir, M., Shabbir, A., Iwendi, C., Javed, A.R., Rizwan, M., Herencsar, N., Lin, J.C.W..: Enhancing security of health information using modular encryption standard in mobile cloud computing. IEEE Access pp 1–1 (2021) https://doi.org/10.1109/ACCESS.2021.3049564
Javed, A.R., Abid, R., Aslam, B., Khalid, H.A., Khan, M.Z., Alhazmi, O.H., Rizwan, M.: Green5g: enhancing capacity and coverage in device-to-device communication. Comput. Mater. Continua 67(2), 1933–1950 (2021)
Sun, W., Cai, Z., Liu, F., Fang, S., Wang, G.: A survey of data mining technology on electronic medical records. In: Proceedings of the 2017 IEEE 19th International Conference on e-Health Networking, pp. 1–6. Applications and Services (Healthcom), IEEE (2017)
Tang, J., Liu, A., Zhao, M., Wang, T.: An aggregate signature based trust routing for data gathering in sensor networks. Security Commun. Netw. (2018). https://doi.org/10.1155/2018/6328504
Hossain, M.M., Fotouhi, M., Hasan, R.: Towards an analysis of security issues, challenges, and open problems in the internet of things. In: Proceedings of the 2015 IEEE World Congress on Services, IEEE, pp 21–28 (2015)
Kagita, M.K., Thilakarathne, N., Gadekallu, T.R., Maddikunta, P.K.R.: A review on security and privacy of internet of medical things. Comput. Sci. (2020)
Wang, Q., Wang, C., Li, J., Ren, K., Lou, W..: Enabling public verifiability and data dynamics for storage security in cloud computing. In: Proceedings of the European symposium on research in computer security, Springer, pp 355–370 (2009)
Kumar, R.: Research on cloud computing security threats using data transmission. Int. J. Adv. Res. Comput. Sci. Softw. Eng. India 5(1), 399–402 (2015)
Meng, D.: Data security in cloud computing. In: Proceedings of the 8th International Conference on Computer Science & Education (ICCSE 2013) (2013)
Shawish A, Salama M.: Cloud computing: paradigms and technologies. In: Proceedings of the Inter-cooperative collective intelligence: techniques and applications, Springer, pp 39–67 (2014)
Negi, A., Singh, M., Kumar, S.: An efficent security farmework design for cloud computing using artificial neural networks. Int. J. Comput. Appl. 129(4), 1721 (2015)
Khan, S.M., Hamlen, K.W.: Anonymouscloud: a data ownership privacy provider framework in cloud computing. In: Proceedings of the 2012 IEEE 11th International Conference on Trust, pp. 170–176. Security and Privacy in Computing and Communications, IEEE (2012)
Thilakarathne, N.N., Kagita, M.K., Gadekallu, T.R.: The role of the internet of things in health care: a systematic and comprehensive study. Int. J. Eng. Manage. Res. 10(4), 145–159 (2020)
Javed, A.R., Sarwar, M.U., Khan, H.U., Al-Otaibi, Y.D., Alnumay, W.S.: Pp-spa: privacy preserved smartphone-based personal assistant to improve routine life functioning of cognitive impaired individuals. Neural Process. Lett. (2021). https://doi.org/10.1007/s11063-020-10414-5
Zhao, Y.: Identity-concealed authenticated encryption and key exchange. In: Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, pp 1464–1479 (2016)
Abdmeziem, M.R., Tandjaoui, D.: A cooperative end to end key management scheme for e-health applications in the context of internet of things. In: Proceedings of the International Conference on Ad-Hoc Networks and Wireless, Springer, pp 35–46 (2014)
Gong, T., Huang, H., Li, P., Zhang, K., Jiang, H.: A medical healthcare system for privacy protection based on iot. In: Proceedings of the 2015 Seventh International Symposium on Parallel Architectures, pp. 217–222. Algorithms and Programming (PAAP), IEEE (2015)
Hu, J.X., Chen, C.L., Fan, C.L., Wang, K.: An intelligent and secure health monitoring scheme using IoT sensor based on cloud computing. J. Sens. (2017). https://doi.org/10.1155/2017/3734764
Li, C.T., Lee, C.C., Weng, C.Y.: A secure cloud-assisted wireless body area network in mobile emergency medical care system. J. Med. Syst. 40(5), 117 (2016)
Bacis, E., De Capitani di Vimercati, S., Foresti, S., Paraboschi, S., Rosa, M., Samarati, P.: Mix&slice: efficient access revocation in the cloud. In: Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, pp 217–228 (2016)
Vinu, R., Varghese, P.: Robust optimized artificial neural network based pem fuelcell voltage tracking. In: Proceedings of the Innovations in Bio-Inspired Computing and Applications, Springer, pp 79–91 (2016)
Sharma, A., Sarishma, R.T., Chilamkurti, N., Kim, B.G.: Blockchain based smart contracts for internet of medical things in e-healthcare. J. Electron. (2020)
Vidal, R.: Subspace clustering. IEEE Signal Process. Mag. 28(2), 52–68 (2011)
Zhang, T., Sodhro, A.H., Zahid, Z.L.N., Nawaz, M.W.: A joint deep learning and internet of medical things driven framework for elderly patients. IEEE (2020)
Saba, T., Haseeb, K., Ahmed, A.I.: Secure and energy-efficient framework using internet of medical things for e-healthcare. J. Infect. Public Health (2020). https://doi.org/10.1016/j.jiph.2020.06.027
Perveen, S., Shahbaz, M., Guergachi, A., Keshavjee, K.: Performance analysis of data mining classification techniques to predict diabetes. Procedia Comput. Sci. 82, 115–121 (2016)
Miao, Y., Ma, J., Liu, X., Wei, F., Liu, Z., Wang, X.A.: m 2-abks: attribute-based multi-keyword search over encrypted personal health records in multi-owner setting. J. Med. Syst. 40(11), 246 (2016)
Wang, J., Wu, L., Wang, H., Choo, K.K.R., He, D.: An efficient and privacy-preserving outsourced support vector machine training for internet of medical things. IEEE (2020)
Han, J., Pei, J., Kamber, M.: Data Mining: Concepts and Techniques. Elsevier, New York (2011)
Fallahpour, A., Moghassem, A.: Yarn strength modelling using adaptive neuro-fuzzy inference system (anfis) and gene expression programming (gep). J. Eng. Fibers Fabr. 8(4), 155892501300800420 (2013)
Ahmad, A., Ruelens, D.: Development of digital logic design teaching tool using matlab & simulink. IEEE Technol. Eng. Educ. (ITEE) 8(1), 7–11 (2013)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Mohiyuddin, A., Javed, A.R., Chakraborty, C. et al. Secure Cloud Storage for Medical IoT Data using Adaptive Neuro-Fuzzy Inference System. Int. J. Fuzzy Syst. 24, 1203–1215 (2022). https://doi.org/10.1007/s40815-021-01104-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40815-021-01104-y