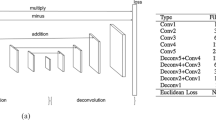
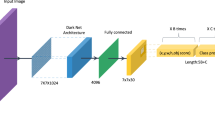
Abstract
Counterfeit integrated circuits (ICs) constitute a major threat to system reliability, as well as security from personal to national scale. Most current techniques for counterfeit electronics detection are expensive, time consuming, and prone to human error. We have proposed a convolutional neural network (CNN) architecture–based supervised technique along with two unsupervised techniques based on depth map and texture of pins to identify bent and corroded pins respectively with high accuracy, thus helping to identify recycled ICs. The supervised technique requires one-time training, and is amenable to be integrated in a fast and automated counterfeit IC detection methodology. We have also compared the proposed CNN–based classification technique accuracy with support vector machine (SVM) and K-nearest neighbor (KNN)–based classification techniques. Using these methods, both corroded and bent pins are differentiated with high accuracy. The unsupervised bent pin detection technique uses depth map images of ICs to construct 3D images of ICs and the corroded pin detection methodology uses Laws’ texture energy method and K-means clustering to differentiate between defective and non-defective pins.






Similar content being viewed by others
References
Guin U, Huang K, DiMase D, Carulli JM, Tehranipoor M, Makris Y. (2014) Counterfeit integrated circuits: a rising threat in the global semiconductor supply chain. Proc IEEE 102(8):1207–1228
Reports of counterfeit parts quadruple since 2009, Challenging US defense industry and national security, (2012). Accessed: 2017-07-04
ICF International (2011) Electronics waste management in the United States through 2009
Higginbotham S (2018) The Internet of trash: IoT has a looming e-waste problem
Guin U, DiMase D, Tehranipoor M (2014) A comprehensive framework for counterfeit defect coverage analysis and detection assessment. J Electron Test 30(1):25–40
Guin U, Forte D, Tehranipoor M (2013) Anti-counterfeit techniques: from design to resign. In: 2013 14th international workshop on microprocessor test and verification (MTV). IEEE, pp 89–94
Guin U, DiMase D, Tehranipoor M. (2014) Counterfeit integrated circuits: detection, avoidance, and the challenges ahead. Journal of Electronic Testing and Test Applications 30(1):9–23
Huang K, Carulli JM, Makris Y (2012) Parametric counterfeit ic detection via support vector machines. In: IEEE international symposium on defect and fault tolerance in VLSI and Nanotechnology systems (DFT). IEEE, pp 7–12
Guin U, Tehranipoor M, DiMase D, Megrdichian M et al (2013) Counterfeit IC detection and challenges ahead. ACM SIGDA 43(3):1–5
Moore SK (2018) That new memory smell: tech can tell if your flash is new or recycled
Ghosh P, Chakraborty RS (2017) Counterfeit IC detection by image texture analysis. In: 2017 Euromicro conference on digital system design (DSD), pp 283–286
Cobb WE, Garcia EW, Temple MA, Baldwin RO, Kim YC (2010) Physical layer identification of embedded devices using RF-DNA fingerprinting. In: Military communications conference, 2010-MILCOM 2010. IEEE, pp 2168–2173
Miller M, Meraglia J, Hayward J (2012) Traceability in the age of globalization: a proposal for a marking protocol to assure authenticity of electronic parts. Technical report, SAE Technical Paper
U.S. Defense Logistics Agency (2012) DNA authentication marking on items in FSC 5962
Semiconductor Industry Association (SIA) (2012) Public comments - DNA authentication marking on items in FSC5962
Lim D, Lee JW, Gassend B, Suh GE, Van Dijk M, Devadas S. (2005) Extracting secret keys from integrated circuits. IEEE Trans Very Large Scale Integr VLSI Syst 13(10):1200–1205
Zhao D, Li S (2005) A 3D image processing method for manufacturing process automation. Computers in Industry (special issue on Machine Vision) 56(8):975–985
Tapia G, Elwany A. (2014) A review on process monitoring and control in metal-based additive manufacturing. J Manuf Sci Eng 060801(12):136
Nikam PA, Sawant SD (2017) Circuit board defect detection using image processing and microcontroller. In: 2017 international conference on intelligent computing and control systems (ICICCS), pp 1096–1098
Baygin M, Karakose M, Sarimaden A, Akin E (2017) Machine vision based defect detection approach using image processing. In: 2017 international artificial intelligence and data processing symposium (IDAP), pp 1–5
Torrance R, James D (2009) The state-of-the-art in IC reverse engineering. In: Proceedings of the international workshop on cryptographic hardware and embedded systems (CHES), pp 363–381
Asadizanjani N, Tehranipoor M, Forte D. (2017) PCB reverse engineering using nondestructive X-ray tomography and advanced image processing. IEEE Trans Compon Packag Manuf Technol 7(2):292–299
Mahmood K, Carmona PL, Shahbazmohamadi S, Pla F, Javidi B. (2015) Real-time automated counterfeit integrated circuit detection using X-ray microscopy. Appl Opt 54(13):D25–D32
Shahbazmohamadi S, Forte D, Tehranipoor M (2014) Advanced physical inspection methods for counterfeit detection. In: Proceedings of international symposium for testing and failure analysis (ISFTA), pp 55–64
Asadizanjani N, Tehranipoor M, Forte D (2017) Counterfeit electronics detection using image processing and machine learning. J Phys Conf Ser 787(1):1–6
Ghosh P, Forte D, Woodard DL, Chakraborty RS (2018) Automated detection of pin defects on counterfeit microelectronics. In: 2018 international symposium for testing and failure analysis (ISTFA)
Lee JS, Jian GA, Chien CA, Chen PS, Guo JI (2012) 3D Depth Map generation for embebbed stereo applications. In: 2012 IEEE conference on visual communications and image processing (VCIP), pp 1–6
Digital Microscope – Leica DVM6, (2017)
Hearst MA, Dumais ST, Osuna E, Platt J, Scholkopf B (1998) Support vector machines. IEEE Intelligent Systems and their applications 13(4):18–28
Cunningham P, Delany SJ (2007) K-nearest neighbour classifiers. Multiple Classifier Systems 34(8):1–17
Beam AL (2017) You can probably use deep learning even if your data isn’t that big
Goodfellow I, Bengio Y, Courville A (2016) Deep learning. MIT Press, Cambridge. http://www.deeplearningbook.org
Radford A, Metz L, Chintala S (2015) Unsupervised representation learning with deep convolutional generative adversarial networks. CoRR arXiv:http://arXiv.org/abs/1511.6434
Thompson CM, Shure L (1995) Image processing toolbox: for use with MATLAB;[user’s Guide] MathWorks
Stockman G, Shapiro LG (2001) Computer vision, 1st. Prentice Hall PTR, Upper Saddle River
Laws KI Textured image segmentation. PhD thesis, University of Southern California, Jan 1980. Accessed: 2017-07-04
Duda RO, Hart PE, Stork DG (2001) Pattern classification, 2nd edn. Wiley, New York
Rousseeuw PJ (1987) Silhouettes: a graphical aid to the interpretation and validation of cluster analysis. J Comput Appl Math 20:53–65
Hsu CW, Chang CC, Lin CJ (2003) A practical guide to support vector classification. Technical report, Department of Computer Science National Taiwan University
Pechenizkiy M, Tsymbal A, Puuronen S (2004) PCA-based feature transformation for classification: issues in medical diagnostics. In: 2004 CBMS 2004. Proceedings. 17th IEEE symposium on computer-based medical systems. IEEE, pp 535–540
Szegedy C, Liu W, Jia Y, Sermanet P, Reed S, Anguelov D, Erhan D, Vanhoucke V, Rabinovich A. (2015) Going deeper with convolutions. In: 2015 IEEE conference on computer vision and pattern recognition (CVPR), pp 1–9
Simonyan K, Zisserman A (2014) Very deep convolutional networks for large-scale image recognition
Funding
Pallabi Ghosh was funded by IBM Corporation, through a Shared University Research (SUR) award to Dr. Rajat Subhra Chakraborty.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
A preliminary version of this paper was published in the proceedings of the ISTFA’18 conference.
Rights and permissions
About this article
Cite this article
Ghosh, P., Bhattacharya, A., Forte, D. et al. Automated Defective Pin Detection for Recycled Microelectronics Identification. J Hardw Syst Secur 3, 250–260 (2019). https://doi.org/10.1007/s41635-019-00069-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41635-019-00069-7