Abstract
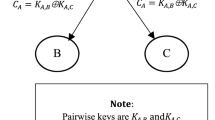
A modification of the KDP scheme for the distribution of encryption keys is considered as applied to a distributed computer system with a discretionary security model. Limited access is specified as forbidden channels of data transmission. The scheme of preliminary key distribution is designed in such a way that it is impossible for forbidden channels to create a key-pair for the data exchange. An example of the construction of the proposed scheme is presented.
Similar content being viewed by others
References
Belim, S.V., Belim, S.Yu., and Polyakov, S.Yu., The implementation of discretionary access separation using the modified Blom’s circuit of pre-shared keys, Probl. Inf. Bezop., Komp’yut. Sist., 2015, no. 3, pp. 72–76.
Belim, S.V., Belim, S.Yu., and Polyakov, S.Yu., Modification of the Blom’s scheme of pre-shared keys taking into account discretionary security policy, Informatsionnaya bezopasnost’ i zashchita personal’nykh dannykh: Problemy i puti ikh resheniya: Materialy VI Mezhregional’noi nauchno-prakticheskoi konferentsii (Information Security and Protection of Personal Data: Problems and Their Solutions: Proc. VI Inter-regional Scientific-Practical Conference), Bryansk: BGTU, 2014, pp. 13–14.
Alferov, A.P., Zubov, A.U., Kuzmin, A.S., and Cheremushkin, A.V., Osnovy kriptografii (Basics of Cryptography), Moscow: Gelios ARV, 2001.
Cheremushkin, A.V., Combinatorial-geometric approaches to design of pre-shared key distribution patterns (review), Prikl. Diskretn. Mat., 2008, no. 1 (1), pp. 55–63.
Shchurov, I.I., Methods of construction of pre-shared key distribution patterns, Vestn. MEI, 2004, no. 6, pp. 94–104.
Author information
Authors and Affiliations
Corresponding author
Additional information
Original Russian Text © S.V. Belim, S.Yu. Belim, 2016, published in Problemy Informatsionnoi Bezopasnosti, Komp’yuternye Sistemy.
About this article
Cite this article
Belim, S.V., Belim, S.Y. KDP scheme of preliminary key distribution in discretionary security policy. Aut. Control Comp. Sci. 50, 773–776 (2016). https://doi.org/10.3103/S014641161608006X
Received:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S014641161608006X