Abstract
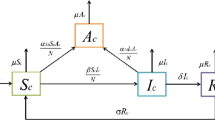
This study made an inductive discussion on the definition and characteristics of computer viruses and analyzed virus transmission models as well as virus control. Like tumor cells in human body, computer viruses will rapidly transfer and disperse if they are not controlled, indicating a poor stability. To investigate the transmission control of computer viruses, a dynamical model was established for virus transmission and the concept of “equivalent day” was introduced to analyze the dynamic characteristics of discrete transfer of the model and the stability of virus-free equilibrium points and endemic equilibrium points. The characteristic value was obtained by calculating the equation of the model. Moreover, the necessary and sufficient conditions for virus-free and endemic equilibrium points of the model were obtained by proof using Lyapunov first method and disc theorem. Then the model was compared with SIS and SIR models. Finally, a control item was added based on the virus discrete transmission model and the transformation trends of the number of the infected principle machine and the infective principal machine before and after the addition of the control item were compared. In this way, the optimal control strategy for virus transmission model was designed and the effectiveness of the optimal control was verified.
Similar content being viewed by others
References
Ying, X., Artificial intelligence and its application in computer network technology, Technol. Mark., 2011, vol. 18, no. 2, p. 20.
Xiaoxiao, Z., Research on the ability of index members in the era of big data, Libr. Work Res., 2016, vol. 3, pp. 25–27.
Mingming, Y. and Jing, L., Introduction of computer virus and preventive measures, Intell. Comput. Appl., 2010, vol. 1, pp. 145–146.
Ping, Z., Discussion on computer network security vulnerabilities and preventive measures, Comput. CD-ROM Software Appl., 2012, vol. 3, pp. 31–32.
Liying, Z., Discussion on the computer network security vulnerabilities and defense, China Mag., 2014, vol. 3, p. 282.
Youfei, Y., Analysis of ARP virus attack in LAN of electric power enterprises, Pract. Electron., 2013, vol. 24, p. 141.
Feng, G., All-pervasive high-tech hacking, People’s Police, 2009, vol. 13, pp. 50–52.
Chunye, L., The Legal Rules and Regulations of the Information of the Rubbish in Our Country, D. Jilin University, 2010.
Chengguang, G., A brief discussion on the connotation and characteristics of computer virus, Electron. Technol. Software Eng., 2012, vol. 22, pp. 50–52.
Wanxin, D. and Zhiqiang, L., Discussion on computer virus protection, Inf. Syst. Eng., 2014, vol. 2, p. 76.
Yan, Z. and Jian, X., Some common knowledge about computer “virus,” Shandong Arch., 2002, vol. 2, pp. 42–43.
Shuang, B., Computer virus prevention measures, Gakuen Scholars: Spiritual Home, 2010, no. 3, p. 175.
Ning, H. and Yonghong, J., Discussion on computer virus and its protective measures, Comput. CD Software Appl., 2012, vol. 8, p. 85.
Chunmei, L., Application of Lyapunov Method in System Stability Theory, Northeast Normal University, 2010.
Qixin, Z., Shousong, H., and Ya, L., Stochastic optimal control of networked control systems with long time delay in network control systems, Control Theory Appl., 2004, vol. 21, no. 3, pp. 321–326.
Author information
Authors and Affiliations
Corresponding author
Additional information
The article is published in the original.
About this article
Cite this article
Han, C., Li, L. Control on the transmission of computer viruses in network. Aut. Control Comp. Sci. 51, 233–239 (2017). https://doi.org/10.3103/S0146411617040022
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S0146411617040022