Abstract
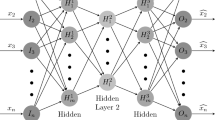
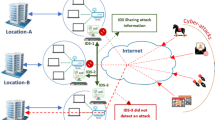
The article discusses the problem of analysis of cybersecurity threats in wireless ad hoc networks—VANET, FANET, MARINET, MANET, WSN. The problem of neural network approximation of the function of cyber threat existence in the system is formulated. The parameters of the neural network model were optimized according to the likelihood maximization criterion on the training data set. A hybrid neural network based on recurrent and graph convolutional neural networks is proposed as a solution architecture.



Similar content being viewed by others
REFERENCES
Kalinin, M.O., Krundyshev, V.M., and Semianov, P.V., Architectures for building secure vehicular networks based on SDN technology, Autom. Control Comput. Sci., 2017, vol. 51, no. 8, pp. 907–914.
Komala, S.R., Srinivas Shetty, Padmashree, S., and Elevarasi, E., Wireless Ad Hoc Mobile Networks, National Conference on Computing Communication and Technology, 2010, pp. 168–174.
Broch, J., Maltz, D.A., Johnson, D.B., Yih-Chun Hu, and Jetcheva, J., A Performance Comparison of Multi-hop Wireless Ad Hoc Network Routing Protocols. http://www.monarch.cs.cmu.edu/.
Perkins, C. and Royer, E., Ad hoc on-demand distance vector routing, Proceedings of Second IEEE Workshop on Mobile Computing Systems and Applications, 1999, pp. 90–100.
Sumra, I., Ahmad, I., Hasbullah, H., and Manan, J., Classes of attacks in VANET, 2011 Saudi International Electronics, Communications and Photonics Conference (SIECPC), 2011, pp. 1–5.
Yifeng Zhou, Lamont, L., and Li Li, Wormhole attack detection based on distance verification and the use of hypothesis testing for wireless ad hoc networks, MILCOM 2009—2009 IEEE Military Communications Conference, Boston, 2009, pp. 1–7.
Tamilselvan, L. and Sankaranarayanan, V., Prevention of blackhole attack in MANET, The 2nd International Conference on Wireless Broadband and Ultra Wideband Communications (AusWireless 2007), Sydney, 2007, p. 21.
Hastad, J., Computational Limitations of Small-Depth Circuits, Cambridge, MA: MIT Press, 1987.
Yoshua Bengio, Learning deep architectures for AI, Found. Trends Mach. Learn., 2009, vol. 2, no. 1, pp. 1–127. http://dx.doi.org/.10.1561/2200000006
Montufar, G., et al., On the number of linear regions of deep neural networks, Proc. 27th NIPS, Cambridge, MA, 2014, pp. 2924–2932.
Perozzi, B., Al-Rfou, R., and Skiena, S., DeepWalk: Online learning of social representations, Proceedings of the 20th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining (KDD '14), New York, 2014, pp. 701–710.
Mikolov, T., Sutskever, I., Kai Chen, Corrado, G., and Dean, J., Distributed representations of words and phrases and their compositionality, Proceedings of the 26th International Conference on Neural Information Processing Systems (NIPS’13), Burges, C.J.C., Bottou, L., Welling, M., Ghahramani, Z., and Weinberger, K.Q., Eds., 2013, vol. 2, pp. 3111–3119.
Xinghuo Yu, Efe, M.O., and Kaynak, O., A general backpropagation algorithm for feedforward neural networks learning, IEEE Trans. Neural Networks, 2002, vol. 13, no. 1, pp. 251–254.
Kipf, T.N. and Welling, M., Semi-supervised classification with graph convolutional networks, CoRR abs/1609.02907, 2016.
Hochreiter, S. and Schmidhuber, J., Long short-term memory, Neural Comput., 1997, vol. 9, no. 8, pp. 1735–1780.
ACKNOWLEDGMENTS
The project results are achieved using the resources of supercomputer center of Peter the Great St.Petersburg Polytechnic University – SCC “Polytechnichesky” (www.spbstu.ru).
Author information
Authors and Affiliations
Corresponding authors
Additional information
The article was translated by the authors.
About this article
Cite this article
Demidov, R.A., Zegzhda, P.D. & Kalinin, M.O. Threat Analysis of Cyber Security in Wireless Adhoc Networks Using Hybrid Neural Network Model. Aut. Control Comp. Sci. 52, 971–976 (2018). https://doi.org/10.3103/S0146411618080084
Received:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S0146411618080084