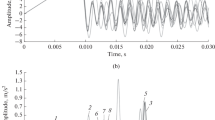
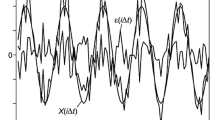
Abstract—
Telecommunication devices are becoming one of the critical elements of industrial systems. They are an attractive target for potential attackers. A method for identification of anomalies based on local signal spectra and using neural networks for evaluation is considered. An experiment is performed on the basis of statistical data on the loading of a computing device.


Similar content being viewed by others
REFERENCES
Vasiliev, Y.S., Zegzhda, P.D., and Kuvshinov, V.I., Modern problems of cybersecurity, Nonlinear Phenom. Complex Syst. (Dordrecht, Neth.), 2014, vol. 17, no. 3, pp. 210–214.
Anisimov, V.G., Anisimov, E.G., Zegzhda, P.D., and Suprun, A.F., The problem of innovative development of information security systems in the transport sector, Autom. Control Comput. Sci., 2018, vol. 52, no. 8, pp. 1105–1110.
Pavlenko, E. and Zegzhda, D., Sustainability of cyber-physical systems in the context of targeted destructive influences, IEEE Industrial Cyber-Physical Systems, ICPS 2018, 2018, pp. 830–834.
Zegzhda, D.P., Poltavtseva, M.A., and Lavrova, D.S., Systematization and security assessment of cyber-physical systems, Autom. Control Comput. Sci., 2017, vol. 51, no. 8, pp. 835–843.
Belenko, V., Krundyshev, V., and Kalinin, M., Synthetic datasets generation for intrusion detection in VANET, ACM International Conference Proceeding Series, 2018. https://doi.org/10.1145/3264437.3264479
Poltavtseva, M.A., Zegzhda, D.P., and Pavlenko, E.Y., High-performance NIDS architecture for enterprise networking, 2019 IEEE International Black Sea Conference on Communications and Networking, BlackSeaCom 2019, 2019. https://doi.org/10.1109/BlackSeaCom.2019.8812808
Platonov, V.V. and Semenov, P.O., Using data-mining methods to detect network attacks, Autom. Control Comput. Sci., 2015, vol. 49, no. 8, pp. 766–769.
Zegzhda, D.P. and Kalinin, M.O., Security assurance for the attribute-based access control systems, International Conference on Enterprise Information Systems and Web Technologies 2008, EISWT 2008, pp. 147–154.
Krundyshev, V. and Kalinin, M., Prevention of false data injections in smart infrastructures, 2019 IEEE International Black Sea Conference on Communications and Networking, BlackSeaCom 2019, 2019. https://doi.org/10.1109/BlackSeaCom.2019.8812786
Demidov, R.A., Zegzhda, P.D., and Kalinin, M.O., Threat analysis of cyber security in wireless adhoc networks using hybrid neural network model, Autom. Control Comput. Sci., 2018, vol. 52, no. 8, pp. 971–976.
Kalinin, M., Krundyshev, V., Rezedinova, E., and Zegzhda, P., Role-based access control for vehicular adhoc networks, 2018 IEEE International Black Sea Conference on Communications and Networking, BlackSeaCom 2018, 2018. https://doi.org/10.1109/BlackSeaCom.2018.8433628
Farwell, J.P. and Rohozinski, R., Stuxnet and the future of cyber war, Survival, 2011, vol. 53, no. 1, pp. 23–40. https://doi.org/10.1080/00396338.2011.555586
Yeung, D.Y. and Ding, Y., Host-based intrusion detection using dynamic and static behavioral models, Pattern Recognit., 2003, vol. 36, no. 1, pp. 229–243.
Yuan, K., Ling, Q., and Yin, W., On the convergence of decentralized gradient descent, SIAM J. Optim., 2016, vol. 26, no. 3, pp. 1835–1854.
Slay, J. and Miller, M., Lessons learned from the Maroochy water breach, in Critical Infrastructure Protection, Springer, 2007, pp. 73–82.
Zegzhda, D.P., Kalinin, M.O., and Levykin, M.V., Actual vulnerabilities of industrial automation protocols of an open platform communications series, Autom. Control Comput. Sci., 2019, vol. 53, no. 8, pp. 972–979.
Gao, D., Reiter, M.K., and Song, D., Beyond output voting: Detecting compromised replicas using hmm-based behavioral distance, IEEE Trans. Dependable Secure Comput., 2009, vol. 6, no. 2, pp. 96–110.
Igure, V.M., Laughter, S.A., and Williams, R.D., Security issues in SCADA networks, Comput. Secur., 2006, vol. 25, no. 7, pp. 498–506.
Lavrova, D., Zegzhda, D., and Yarmak, A., Predicting cyber attacks on industrial systems using the Kalman filter, 3rd World Conference on Smart Trends in Systems, Security and Sustainability, WorldS4 2019, 2019, pp. 317–321. https://doi.org/10.1109/WorldS4.2019.8904038
Zegzhda, P.D., Lavrova, D.S., and Shtyrkina, A.A., Multifractal analysis of Internet backbone traffic for detecting denial of service attacks, Autom. Control Comput. Sci., 2018, vol. 52, no. 8, pp. 936–944.
Kalinin, M.O., Lavrova, D.S., and Yarmak, A.V., Detection of threats in cyberphysical systems based on deep learning methods using multidimensional time series, Autom. Control Comput. Sci., 2018, vol. 52, no. 8, pp. 912–917.
Belenko, V., Krundyshev, V., and Kalinin, M., Intrusion detection for Internet of Things applying metagenome fast analysis, 3rd World Conference on Smart Trends in Systems, Security and Sustainability, WorldS4 2019, 2019, pp. 129–135. https://doi.org/10.1109/WorldS4.2019.8904022
Zegzhda, P.D., Zegzhda, D.P., Kalinin, M.O., and Konoplev, A.S., Security modeling of grid systems using petri nets, Lect. Notes Comput. Sci., 2012, vol. 7531, pp. 299–308.
Kalinin, M., Demidov, R., and Zegzhda, P., Hybrid neural network model for protection of dynamic cyber infrastructure, Nonlinear Phenom. Complex Syst. (Dordrecht, Neth.), 2019, vol. 22, no. 4, pp. 375–382.
Demidov, R.A., Zegzhda, P.D., and Kalinin, M.O., Threat analysis of cyber security in wireless adhoc networks using hybrid neural network model, Autom. Control Comput. Sci., 2018, vol. 52, no. 8, pp. 971–976.
Kalinin, M.O., Zubkov, E.A., Suprun, A.F., and Pechenkin, A.I., Prevention of attacks on dynamic routing in self-organizing adhoc networks using swarm intelligence, Autom. Control Comput. Sci., 2018, vol. 52, no. 8, pp. 977–983.
Krundyshev, V., Kalinin, M., and Zegzhda, P., Artificial swarm algorithm for VANET protection against routing attacks, 2018 IEEE Industrial Cyber-Physical Systems, ICPS 2018, 2018, pp. 795–800. https://doi.org/10.1109/ICPHYS.2018.8390808
Malyshev, E.V., Moskvin, D.A., and Zegzhda, D.P., Application of an artificial neural network for detection of attacks in vanets, Autom. Control Comput. Sci., 2019, vol. 53, no. 8, pp. 889–894.
Krundyshev, V. and Kalinin, M., Hybrid neural network frame work for detection of cyber attacks at smart infrastructures, ACM International Conference Proceeding Series, 2019. https://doi.org/10.1145/3357613.3357623
Belenko, V., Chernenko, V., Kalinin, M., and Krundyshev, V., Evaluation of GAN applicability for intrusion detection in self-organizing networks of cyber physical systems, 2018 International Russian Automation Conference, RusAutoCon, 2018. https://doi.org/10.1109/RUSAUTOCON.2018.8501783
Gers, F.A., Schmidhuber, J., and Cummins, F., Learning to forget: Continual prediction with LSTM, Neural Comput., 2000, vol. 12, no. 10, pp. 2451–2471.
Ho, T.K., Random decision forests in document analysis and recognition, 3rd International Conference on Document Analysis and Recognition, 1995, vol. 1, pp. 278–282.
Stepanova, T., Kalinin, M., Baranov, P., and Zegzhda, D., Homogeneity analysis of power consumption for information security purposes, 3rd International Conference of Security of Information and Networks, 2010, pp. 113–117. https://doi.org/10.1145/1854099.1854124
Semenov, V.V., Lebedev, I.S., and Sukhoparov, M.E., An approach to the classification of the state of information security of elements of cyber-physical systems using collateral electromagnetic radiation, Nauchno-Tekh. Vestn. Inf. Mekh. Opt., 2018, vol. 18, no. 1, pp. 98–105. https://doi.org/10.17586/2226-1494-2018-18-1-98-105
Semenov, V.V., Application of an autonomous object behavior model to classify the cybersecurity state, Internet of Things, Smart Spaces, and Next Generation Networks and Systems, 2009, pp. 104–112.
Bendat, J.S. and Piersol, A.G., Engineering Applications of Correlation and Spectral Analysis, Wiley, 1980.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
The authors declare that they have no conflicts of interest.
Additional information
Translated by I. Obrezanova
About this article
Cite this article
Sukhoparov, M.E., Semenov, V.V., Salakhutdinova, K.I. et al. Identification of Anomalies in the Operation of Telecommunication Devices Based on Local Signal Spectra. Aut. Control Comp. Sci. 54, 1001–1006 (2020). https://doi.org/10.3103/S0146411620080337
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S0146411620080337