Abstract
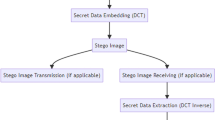
This paper proposes a high-performance steganographic technique in wavelet domain. This algorithm firstly encrypts the information to be embedded and then performs bright-color separation and wavelet transform on the cover-image. With the purpose of guaranteeing the perceptual quality of stego-image and improving the information hiding capacity of cover-image, wavelet trees of cover images are classified into three categories in accordance with human visual system (HVS) characteristics and fuzzy theory. Afterwards, the number of bits to be embedded in each high-frequency coefficient of a wavelet tree is varied adaptively with the type of the trees. Finally following the inverse wavelet transform, the stego-image is generated. Experimental results show that the proposed method is characterized by excellent performances in terms of image quality and message capacity while compatible with JPEG2000 standard. In addition, this algorithm does not need to refer to the original cover-image when the secret information is extracted and achieves blind detection of the extracted information.







Similar content being viewed by others
REFERENCES
Yamin, M. and Sen, A.A.A., Improving privacy and security of user data in location based services, Int. J. Ambient Comput. Intell., 2018, vol. 9, no. 1, pp. 19–42. https://doi.org/10.4018/IJACI.2018010102
Sun, J. and Hu, Y., Chosen-ciphertext secure bidirectional proxy broadcast re-encryption schemes, Int. J. Inf. Commun. Technol., 2016, vol. 8, no. 4, pp. 405–419. https://doi.org/10.1504/IJICT.2016.076798
Djebaili, K. and Melkemi, L., Security and robustness of a modified ElGamal encryption scheme, Int. J. Inf. Commun. Technol., 2018, vol. 13, no. 3, pp. 375–387. https://doi.org/10.1504/IJICT.2018.094325
Mekhaznia, T. and Zidani, A., Swarm intelligence algorithms in cryptanalysis of simple Feistel ciphers, Int. J. Inf. Commun. Technol., 2018, vol. 13, no. 1, pp. 114–138. https://doi.org/10.1504/IJICT.2018.090436
Subhedar, M.S. and Mankar, V.H., Current status and key issues in image steganography: A survey, Comput. Sci. Rev., 2014, vols. 13–14, pp. 95–113. https://doi.org/10.1016/j.cosrev.2014.09.001
Cheddad, A., Condell, J., Curran, K., and Mc Kevitt, P., Digital image steganography: Survey and analysis of current methods, Signal Process., 2010, vol. 90, no. 3, pp. 727–752. https://doi.org/10.1016/j.sigpro.2009.08.010
Mansi, S.S. and Mankar, V.H., Image steganography using redundant discrete wavelet transform and QR factorization, Comput. Electr. Eng., 2016, vol. 54, pp. 406–422. https://doi.org/10.1016/j.compeleceng.2016.04.017
AbdelWahab, O.F., Hussein, A.I., Hamed, H.F., Kelash, H.M., Khalaf, A.A., and Ali, H.M., Hiding data in images using steganography techniques with compression algorithms, Telkomnika, 2019, vol. 17, no. 3, pp. 1168–1175. https://doi.org/10.12928/telkomnika.v17i3.12230
Baby, D., Thomas, J., Augustine, G., George, E., and Michael, N.R., A novel DWT based image securing method using steganography, Procedia Comput. Sci., 2015, vol. 46, pp. 612–618. https://doi.org/10.1016/j.procs.2015.02.105
Levina, A. and Taranov, S., Creation of codes based on wavelet transformation and its application in ADV612 chips, Int. J. Wavelets, Multiresolution Inf. Process., 2017, vol. 15, no. 2, p. 1750014. https://doi.org/10.1142/S021969131750014X
Löhdefink, J., Bär, A., Schmidt, N.M., Hüger, F., Schlicht, P., and Fingscheidt, T., GAN-vs. JPEG2000 image compression for distributed automotive perception: Higher peak SNR does not mean better semantic segmentation, 2019. arXiv:1902.04311 [cs.CV]
Bánoci, V., Bugár, G., and Levický, D., A novel method of image steganography in DWT domain, Proc. 21st Int. Conf. Radioelektronika 2011, Brno, Czech Republic, 2011, IEEE, 2011, pp. 1–4. https://doi.org/10.1109/RADIOELEK.2011.5936455
Ananathavalli, M. and Kuppusamy, K., A novel approach for multilevel steganography, Int. J. Comput. Sci. Mobile Comput., 2014, vol. 3, no. 7, pp. 195–199.
Bedi, P., Bhasin, V., and Yadav, T., 2L-DWTS—Steganography technique based on second level DWT, Int. Conf. on Advances in Computing, Communications and Informatics (ICACCI), Jaipur, India, 2016, IEEE, 2016, pp. 1533–1538. https://doi.org/10.1109/ICACCI.2016.7732266
Li, Q.Z. and Wang, W.J., Low-bit-rate coding of underwater color image using improved wavelet difference reduction, J. Visual Commun. Image Representation, 2010, vol. 21, no. 7, pp. 762–769. https://doi.org/10.1016/j.jvcir.2010.05.003
Li, Q.Z., Zhang, W., Li, M., Niu, J., and Wu, Q.M.J., Automatic detection of ship targets based on wavelet transform for HF surface wavelet radar, IEEE Geosci. Remote Sens. Lett., 2017, vol. 14, no. 5, pp. 714–718. https://doi.org/10.1109/LGRS.2017.2673806
hetre, N.A., Deshpande, A.V., and Mahalle, P.N., Trust management model based on fuzzy approach for ubiquitous computing, Int. J. Ambient Comput. Intell., 2016, vol. 7, no. 2, pp. 33–46. 10.4018/IJACI.201607010
Petitcolas, F.A.P. and Anderson, R.J., Evaluation of copyright marking systems, Proc. IEEE Int. Conf. on Multimedia Computing Systems, Florence, 1999, IEEE, 1999, vol. 1, pp. 574–579. https://doi.org/10.1109/MMCS.1999.779264
Funding
This work was supported by National Natural Science Foundation of China under contract no. 61803178.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
We all declare that we have no conflicts of interest in this paper.
About this article
Cite this article
Wenjin Wang, Liu, X., Lu, M. et al. Intelligent Fuzzy Approach Based High-Performance Steganography in Wavelet Domain. Aut. Control Comp. Sci. 56, 189–197 (2022). https://doi.org/10.3103/S0146411622030087
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S0146411622030087