Abstract
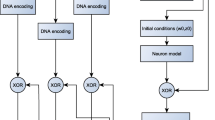
Encryption of image is different from that of texts due to some intrinsic features of images .The time-delay chaotic system can generate complicated dynamical behavior. This is because it has many positive Lapunov exponents. Hence, it is called as super-chaotic system. In this paper, Liao’s chaotic neural system, cat map and general cat map are introduced and analyzed respectively. Then, a new image encryption scheme by employing the Liao’s chaotic system to generate parameters of general cat map is designed. Experimental tests have also demonstrated the high security and fast encryption speed of the proposed scheme.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Liao, X.F., Wong, K.W., Leung, C.S., et al.: Hopf bifurcation and Chaos in a Single Delayed Neuron Equation with Non-monotonic Activation Function. Chaos, Solitions and Fractals 12, 1535–1547 (2001)
Mao, B., Chen, G.R., et al.: A Novel Fast Image Encryption Scheme Based on 3D Chaotic Baker Maps. International Journal of Bifurcation and Chaos 14, 3613–3624 (2004)
Schneier, B.: Applied Cryptography: Protocols, Algorithms, and Source Code in C, 2nd edn. Wiley, New York (1995)
Li, S.J., Zheng, X.: Cryptanalysis of a Chaotic Image Encryption Method. In: IEEE Int Symposium Circuits and Systems, Scottsdale, USA (2002)
Ma, Z., Qiu, S.: An Image Cryptosystem Based on General Cat Map. Journal of China Institute of Communication 24, 51–57 (2003)
Qi, D., Zou, J., et al.: A Novel Transformation and Its Application In Image Formation Hide. Science in China (Series E), vol. 30 (2003)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Copyright information
© 2005 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Deng, S., Zhang, L., Xiao, D. (2005). Image Encryption Scheme Based on Chaotic Neural System. In: Wang, J., Liao, XF., Yi, Z. (eds) Advances in Neural Networks – ISNN 2005. ISNN 2005. Lecture Notes in Computer Science, vol 3497. Springer, Berlin, Heidelberg. https://doi.org/10.1007/11427445_139
Download citation
DOI: https://doi.org/10.1007/11427445_139
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-25913-8
Online ISBN: 978-3-540-32067-8
eBook Packages: Computer ScienceComputer Science (R0)