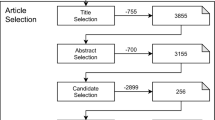
Abstract
It is possible to apply Information Theory to the Software Development process – an approach I have dubbed ’Iterative Theory’. Focusing on the user requirements Iterative Theory is introduced and then used to quantify how the choice of development methodology affects the ’value at risk’ on a software project. The central theme is that end-user requirements cannot be described exactly resulting in an inherent uncertainty in the correctness of any specification. This uncertainty can only be removed by receiving feedback on working software. Iterative Theory, the application of Information Theory to the software development process, is certainly an area requiring further study.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Mackay, David, J.C.: Information Theory, Inference and Learning Algorithms. Cambridge University Press, Cambridge (2004)
Royce, W.: Managing the Development of Large Software Systems. In: Proceedings of IEE Westcon (1970)
Pierce, J.R.: An Introduction to Information Theory. Dover Science Books, New York (1980)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2005 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Tingey, F. (2005). Quantifying Requirements Risk. In: Baumeister, H., Marchesi, M., Holcombe, M. (eds) Extreme Programming and Agile Processes in Software Engineering. XP 2005. Lecture Notes in Computer Science, vol 3556. Springer, Berlin, Heidelberg. https://doi.org/10.1007/11499053_8
Download citation
DOI: https://doi.org/10.1007/11499053_8
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-26277-0
Online ISBN: 978-3-540-31487-5
eBook Packages: Computer ScienceComputer Science (R0)