Abstract
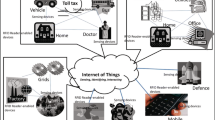
In a Ubiquitous environment many individual devices which have the communication ability with the computation ability are connected with one another. For this change we must be preceded study of Radio Frequency Identification (RFID) afterward research of a sensor network. And we must grasp the threat to protect the RFID system. In this paper we propose safe RFID system modeling based on shared key pool in ubiquitous environment. This proposed modeling is secured to RFID system from many security threat and privacy problem, and it has shorter access delay time. We expect this proposed modeling to be used in ubiquitous environment for the RFID system being safe.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Eschenauer, L., Gligor, V.: A Key-management Scheme for Distributed Sensor Networks. In: ACM CCS 2002, pp. 41–47 (November 2002)
Chan, H., Perrig, A., Song, D.: Random Key Pre-distribution Schemes For Sensor Network. In: IEEE Symposium on Security and Privcy (2003)
Du, W., Deng, J., Yunghsiang, S.H., Pramod, K.V.: A Pairwise Key Predistribution Scheme for Wireless Sensor Networks. In: Proceeding of the 10th ACM conference of Computer and Communication Security, Washington D.C., USA, October 27-30 (2003)
Zhu, S., Xu, S., Setia, S., Jajodia, S.: Establishing Pair-Wise Keys for Secure Communication in Ad Hoc Networks: A Probabilistic Approach. In: 11th IEEE International Conference on Network Protocols (ICNP 2003), Atlanta, Georgia, November 4-7 (2003)
Kalidindi, R., Parachuri, V., Kannan, R., Durresi, A., Iyengar, S.: Sub-Quorum Based Key Vector Assignment: A Key Pre-Distribution Scheme For Wireless Sensor Networs. In: Intnl. Conf. on Wireless Networking (ICWN 2004), Las Vagas (July 2004)
Liu, D., Ning, P.: Establishing Pairwise Keys in Distributed Sensor Networks. In: 10th ACM Conference on Computer and Communications Security (CCS 2003), Washington D.C. (October 2003)
Balfanz, D., Dean, D., Franklin, M., Miner, S., Staddon, J.: Self-healing Key Distribution with Revocation. In: Proceeding of the IEEE Symposium on Research in Security and Privacy, May 2002, pp. 241–257 (2002)
Wong, D.S., Chan, A.H.: Efficient and Mutually Authenticated Key Exchange for Low Power Computing Devices. In: Boyd, C. (ed.) ASIACRYPT 2001. LNCS, vol. 2248, p. 272. Springer, Heidelberg (2001)
Weis, S., et al.: Security and Privacy Aspects of Low-cost Radio Frequency Identification Systems. In: Hutter, D., Müller, G., Stephan, W., Ullmann, M. (eds.) Security in Pervasive Computing. LNCS, vol. 2802, pp. 201–212. Springer, Heidelberg (2004)
Rivest, R.L.: Approaches to RFID Privacy. In: RSA Japen Conference (2003)
Sarma, S., Weis, S., Engls, D.: RFID Systems, Security & Privacy Implications. AutoID Center. white Paper (2002)
Stephen, A.W.: Security and Privacy in Radio-Frequency Identification Devices. MIT, Cambridge (2003)
Juels, A., Rivest, L.R., Szydlo, M.: The Blocker Tag: Selective Blocking of RFID Tags for consumer Privacy. RSA Laboratory. MIT
Juels, A., Brainard, J.: Soft Blocking: Flexible Blocker Tags on the Cheap. RSA Laboratory
Juels, A.: Minimalist Cryptography for Low-Cost RFID Tags. RSA Laboratory
Golle, P., Jakobsson, M., Juels, A., Syverson, P.: Universal Re-encryption for Mixnets. RSA Laboratory (2004)
Sakata, S.: Security Technology for Mobile and Ubiquitous Communication. IEICE Magazine 87(5) (May 2004)
Otsuka, T., Onozawa, A.: User Privacy in Ubiquitous Network: Anonymous Communication Technique for Ad-hoc Network. Technical Report of IEICE ISEC (2003)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2005 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Kim, J., Ryou, H. (2005). Safe RFID System Modeling Using Shared Key Pool in Ubiquitous Environments. In: Huang, DS., Zhang, XP., Huang, GB. (eds) Advances in Intelligent Computing. ICIC 2005. Lecture Notes in Computer Science, vol 3645. Springer, Berlin, Heidelberg. https://doi.org/10.1007/11538356_86
Download citation
DOI: https://doi.org/10.1007/11538356_86
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-28227-3
Online ISBN: 978-3-540-31907-8
eBook Packages: Computer ScienceComputer Science (R0)